Refer to the exhibit.
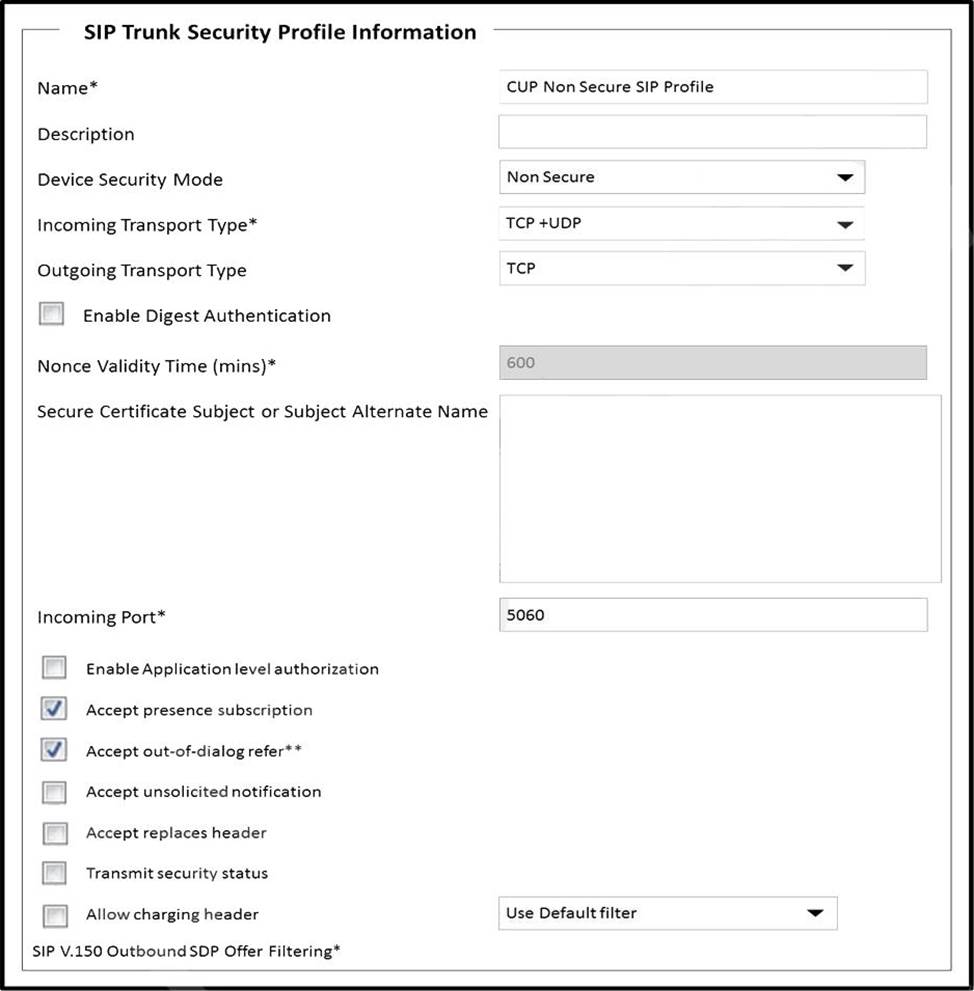
A collaboration engineer is configuring the Cisco UCM IM and Presence Service.
Which two steps complete the configuration of the SIP trunk security profile? (Choose two.)
A . Check the box to enable application-level authorization.
B. Check the box to allow charging header.
C. Check the box to accept unsolicited notification.
D. Check the box to transmit security status.
E. Check the box to accept replaces header.
Answer: C,E
Latest 350-801 Dumps Valid Version with 103 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund