Which two settings must the customer add to correct the issue?
Refer to the exhibit
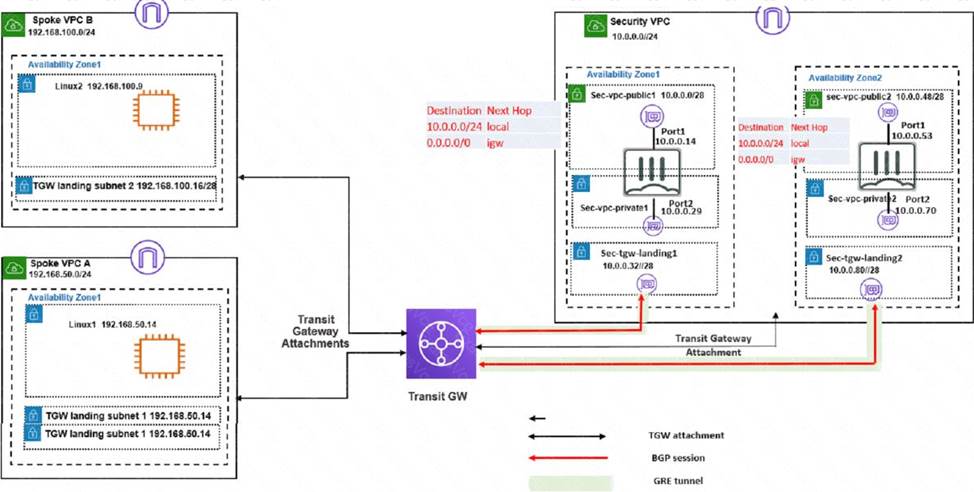
A customer has deployed an environment in Amazon Web Services (AWS) and is now trying to send outbound traffic from the Linux1 and Linux2 instances to the internet through the security VPC (virtual private cloud). The FortiGate policies are configured to allow all outbound
traffic; however, the traffic is not reaching the FortiGate internal interface. Assume there are no issues with the Transit Gateway (TGW) configuration
Which two settings must the customer add to correct the issue? (Choose two.)
A . Both landing subnets in the spoke VPCs must have a 0.0.0.0/0 traffic route to the Internet Gateway (IOW).
B . Both landing subnets in the spoke VPCs must have a 0.0 00/0 traffic route to the TGW
C . Both landing subnets in the security VPC must have a 0.0.0.0/0 traffic route to the FortiGate port2.
D . The four landing subnets in all the VPCs must have a 0.0 0 0/0 traffic route to the TGW
Answer: BC
Explanation:
The correct answer is B and C. Both landing subnets in the spoke VPCs must have a 0.0.0.0/0 traffic route to the TGW. Both landing subnets in the security VPC must have a 0.0.0.0/0 traffic route to the FortiGate port2.
According to the AWS documentation for Transit Gateway, a transit gateway is a network transit hub that connects VPCs and on-premises networks. To send outbound traffic from the Linux instances to the internet through the security VPC, you need to do the following steps:
In the main subnet routing table in the spoke VPCs, add a new route with destination 0.0.0.0/0, next hop TGW. This route directs all traffic from the Linux instances to the TGW, which can then forward it to the appropriate destination based on the TGW route table.
In the main subnet routing table in the security VPC, add a new route with destination 0.0.0.0/0, next hop FortiGate port2. This route directs all traffic from the TGW to the FortiGate internal interface, where it can be inspected and allowed by the FortiGate policies.
The other options are incorrect because:
Adding a 0.0.0.0/0 traffic route to the Internet Gateway (IGW) in the spoke VPCs is not correct, as this would bypass the TGW and the security VPC and send all traffic directly to the internet.
Adding a 0.0.0.0/0 traffic route to the TGW in all the VPCs is not necessary, as only the spoke VPCs need to send traffic to the TGW. The security VPC needs to send traffic to the FortiGate port2.
: Transit Gateways – Amazon Virtual Private Cloud: Fortinet Documentation Library – Deploying FortiGate VMs on AWS
Latest NSE7_PBC-7.2 Dumps Valid Version with 37 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

