Which three steps should an administrator take to protect the OT network?
Refer to the exhibit, which shows a non-protected OT environment.
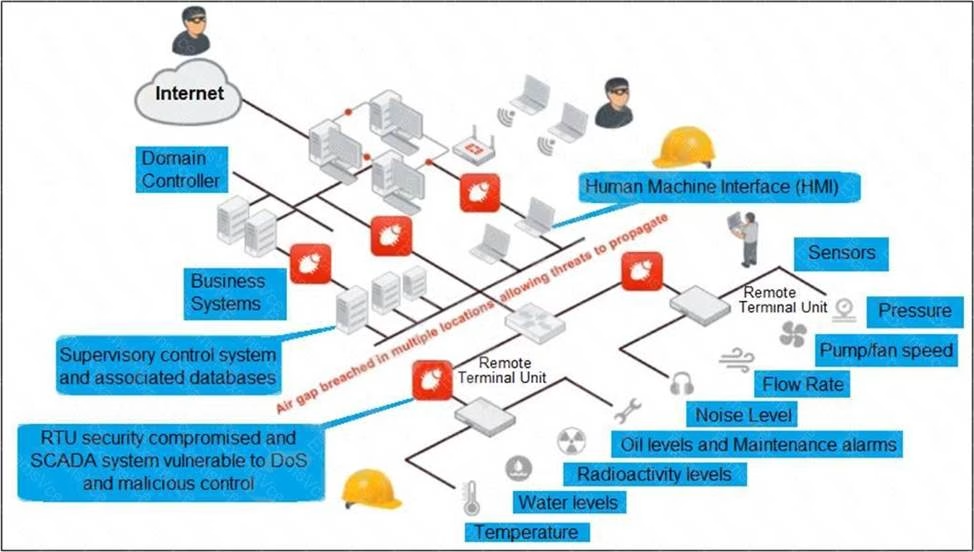
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
A . Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
B . Deploy a FortiGate device within each ICS network.
C . Configure firewall policies with web filter to protect the different ICS networks.
D . Configure firewall policies with industrial protocol sensors
E . Use segmentation
Answer: A, C, D
Latest NSE7_OTS-7.2 Dumps Valid Version with 49 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

