Which security changes should you make?
Topic 2, ADatum Corp.
This is a case study.
Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Background
ADatum Corporation provides verification and investigation services that are used by insurance companies, law firms, and other organizations in the public sector. Services include verifying an individual’s background, qualifications, and specific scenarios that require onsite visit.
The thorough work ADatum Corporation performs results in highly accurate cases with minimal critical information missing. Because of these high-quality results, ADatum Corporation is quickly proving itself as one of the best in the industry. In recent months, business has significantly increased, with most new business coming from high-profile companies and individuals.
Management has decided to create a new qualification verification (QV) role to help ensure that clients get the most accurate results. This role examines completed work to ensure that nothing is missed.
Current environment
Data storage and retention
✑ All information sent by clients for services is stored in Microsoft Dataverse with a model-driven app as the interface.
✑ Clients enter their data in a website, which then uses a service account to create the records in the Dataverse database.
✑ Team members currently have full access to all Service Request records.
Service requests
✑ The Service Request table includes header information about the individual or organization that is the subject of verification.
✑ New Service Request records are assigned to a queue. All potential users who will be performing the verifications have access to these records.
✑ A service request is assigned to a single user who will ensure that all qualifications are verified. This single user is the only one able to process Qualification records related to their own service requests.
✑ Many required tasks when performing verification services are currently done by using manual processes.
✑ To keep up with demand, ADatum Corporation identifies several processes that can be replaced by using Power Automate flows to hire fewer new staff and keep costs down.
Qualification verification
✑ The qualification table contains details about an individual school degree, professional qualifications, and other qualifications that must be verified.
✑ A service request can have one or more Qualification records associated with it.
✑ Record status is pending verification until the initial team member finishes, at
which point the member changes the status to Complete.
✑ When all qualification records related to a service request are verified either by manual or automated processes, the results are made available to ADatum Corporation’s client.
✑ In the rare event that results are questioned, a new service request is created and verified independently of the previous work that took place.
✑ To complete a service request, users perform the following actions:
Microsoft Power platform environment
✑ The following environments exist: development, testing, user acceptance testing (UAT), and production.
✑ Managed solutions are used to move customizations from the development environment to other higher-level environments. These solutions are created and maintained by the power users and provided to internal IT for deployment when they are ready.
✑ Two managed solutions, Verification Process Automation and Onsite Visit, share several components.
✑ All customizations to Power Platform components are performed by several power users who have received training and are certified as subject matter experts.
✑ Power users have been granted the System Administrator security role in the
development environment.
✑ Corporate policy prohibits power users from writing code due to lack of a formal code review process.
✑ Internal IT will not be able to supply any development resources for this project due to a lack of staff. This means that any customizations and automation created for this project must be low-code/no-code for the power users to implement them.
✑ Customizations created by power users are deployed by internal IT.
Requirements
Process automation
ADatum Corporation plans to establish a new QV department to verify completed work so that the quality of work is maintained. The new process for verifying professional qualifications must automate the following:
✑ Enter data and navigate the authority’s website. The authority website UI changes frequently because the company constantly improves the user experience.
✑ Search page contents for a specified value to determine validity.
✑ Update the corresponding Qualification record in Dataverse.
The new process for completing a service request must automate the following:
✑ Set the Service Request record status to Complete when work on all Qualification records is finished.
✑ Send an email to the client with the results when the service request is completed.
The email must list each qualification as either Valid or Not Valid, depending on the verification.
Qualification verification
Service request results will not be released to clients until all related Qualification records are set to a Complete status.
✑ To check work done by a wide array of users, 10 percent of Qualification records must be double checked.
✑ Qualification records must be automatically assigned to a queue.
✑ Qualification records must be flagged with a new status field named Assigned to ensure that records are rechecked.
✑ Ensure that only QV team members can change the status from Assigned to In Progress to Complete.
✑ Record the name of the QV team member who performed the work and the date completed.
Governance and security
✑ All components required for the verification process must be included in a new solution.
✑ Corporate security requires that deployments to non-development environments must be automated using service accounts.
✑ User security and data access must also be consistent across environments, except for the elevated access of the power users in the development environment.
✑ The Onsite Visit managed solution has a table that is not in the Verification Process Automation managed solution. This table must be upgraded prior to the go-live date without the other shared components.
✑ A VP of sales requires a test environment to demonstrate to potential clients the security policies that are included in their initial offering.
Issues
✑ More employees than are required can access individual client information and continue to have access after a service request is completed.
✑ When users go on vacation, all their outstanding Service Request records are assigned to a substitute employee. The substitute employees are unable to see all the qualifications related to their service requests.
✑ Currently, testing the new QV functionality outside the development environment is not possible due to corporate security policies requiring the same security role across all environments.
✑ Internal IT reports that the solution import to the test environment failed because of missing dependencies related to the flow for completing service requests.
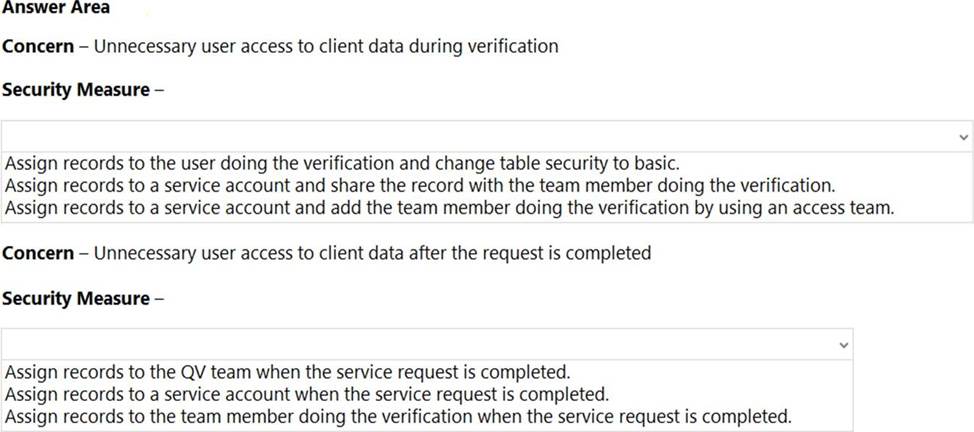
HOTSPOT
You need to address the executive’s concerns regarding unnecessary data access.
Which security changes should you make? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Answer: 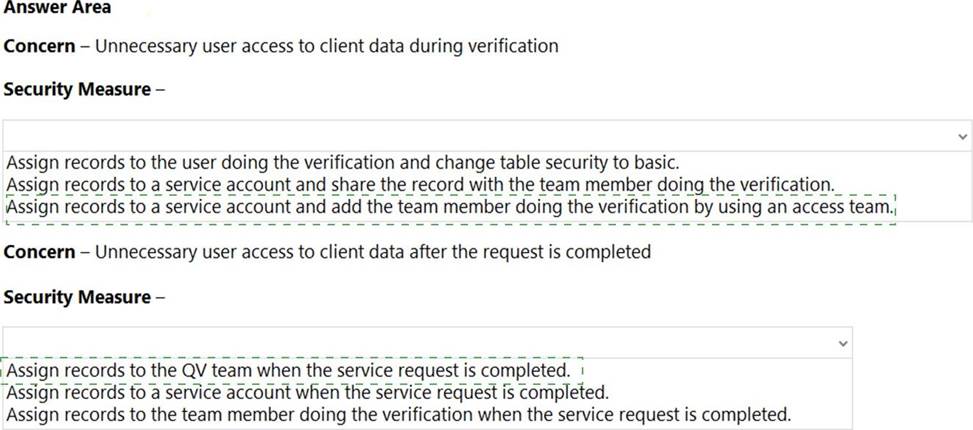
Explanation:
Box 1: Assign records to a service account and add the team member doing the verification by using an access team.
When to use access teams
* The teams are dynamically formed and dissolved. This typically happens if the clear criteria for defining the teams, such as established territory, product, or volume aren’t provided.
* The team members require different access rights on the records. You can share a record with several access teams, each team providing different access rights on the record. For example, one team is granted the Read access right on the account and another team, the Read, Write and Share access rights on the same account.
* A unique set of users requires access to a single record without having an ownership of the record.
Box 2: Assign records to the QV team when the service request is completed.
Issues: More employees than are required can access individual client information and continue to have access after a service request is completed.
Management has decided to create a new qualification verification (QV) role to help ensure that clients get the most accurate results. This role examines completed work to ensure that nothing is missed.
• When users go on vacation, all their outstanding Service Request records are assigned to a substitute employee. The substitute employees are unable to see all the qualifications related to their service requests.
Reference: https://docs.microsoft.com/en-us/power-apps/developer/data-platform/use-access-teams-owner-teams-collaborate-share-information
Latest PL-200 Dumps Valid Version with 104 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

