Which security changes should you make?
HOTSPOT
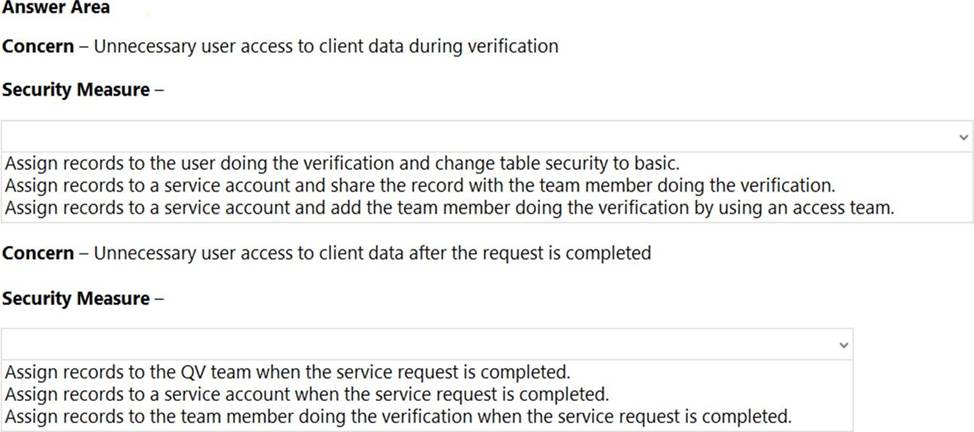
You need to address the executive’s concerns regarding unnecessary data access.
Which security changes should you make? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Answer: 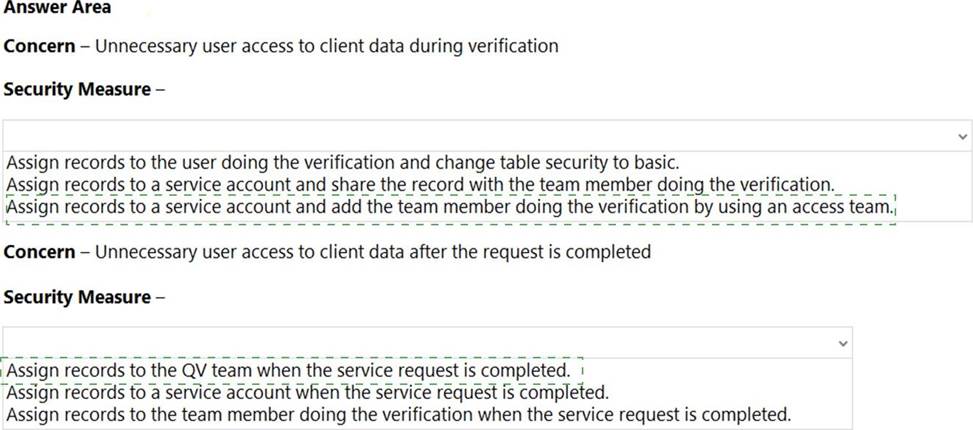
Explanation:
Box 1: Assign records to a service account and add the team member doing the verification by using an access team.
When to use access teams
* The teams are dynamically formed and dissolved. This typically happens if the clear criteria for defining the teams, such as established territory, product, or volume aren’t provided.
* The team members require different access rights on the records. You can share a record with several access teams, each team providing different access rights on the record. For example, one team is granted the Read access right on the account and another team, the Read, Write and Share access rights on the same account.
* A unique set of users requires access to a single record without having an ownership of the record.
Box 2: Assign records to the QV team when the service request is completed.
Issues: More employees than are required can access individual client information and continue to have access after a service request is completed.
Management has decided to create a new qualification verification (QV) role to help ensure that clients get the most accurate results. This role examines completed work to ensure that nothing is missed.
• When users go on vacation, all their outstanding Service Request records are assigned to a substitute employee. The substitute employees are unable to see all the qualifications related to their service requests.
Latest PL-200 Dumps Valid Version with 104 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

