Which RQL detected the vulnerability?
One of the resources on the network has triggered an alert for a Default Config policy.
Given the following resource JSON snippet:
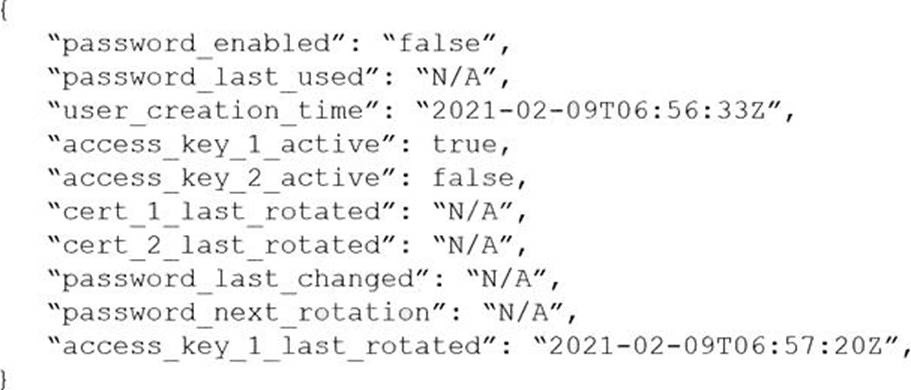
Which RQL detected the vulnerability?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
A . Option A
B . Option B
C . Option C
D . Option D
Answer: B
Explanation:
The correct RQL (Resource Query Language) that detected the vulnerability is:
config from cloud.resource where cloud.type = ‘aws’ and api.name = ‘aws-iam-get-credential-report’ AND json.rule = ‘(access_key_1_active is true and access_key_1_last_rotated != N/A and DateTime. ageInDays (access_key_1_last_rotated) > 90) or (access_key_2_active is true and access_key_2_last_rotated != N/A and _DateTime. ageInDays (access_key_2_last_rotated) > 90)’ This RQL is designed to check the age of the AWS IAM user’s access keys to ensure that they are rotated within a recommended period, typically 90 days. If the access keys have not been rotated within this timeframe, it would be considered a security risk or vulnerability, as old keys may potentially be compromised. By enforcing access key rotation, it minimizes the risk of unauthorized access.
The reference for this type of policy check can be seen in cloud security best practices that advocate for regular rotation of access keys to minimize the potential impact of key compromise. CSPM tools like Prisma Cloud include such checks to automate compliance with these best practices.
Latest PCCSE Dumps Valid Version with 85 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

