Which of the following protocols Is used by Bella?
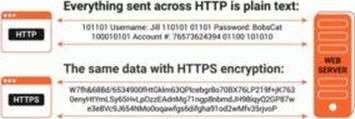
Bella, a security professional working at an it firm, finds that a security breach has occurred while transferring important files. Sensitive data, employee usernames. and passwords are shared In plaintext, paving the way for hackers 10 perform successful session hijacking. To address this situation. Bella Implemented a protocol that sends data using encryption and digital certificates.
Which of the following protocols Is used by Bella?
A . FTP
B . HTTPS
C . FTPS
D . IP
Answer: B
Explanation:
HTTPS is the shortening for hypertext move convention secure, or secure hypertext move convention in the event that you are not a fanatic for semantics.
How Does HTTPS Work?Dissimilar to HTTP, HTTPS utilizes a protected testament from an outsider seller to make sure about an association and confirm that the site is genuine. This safe authentication is known as a SSL Certificate (or “cert”).
SSL is a truncation for “secure attachments layer”. This is the thing that makes a safe, encoded association between a program and a worker, which secures the layer of correspondence between the two.
This declaration encodes an association with a degree of insurance that is assigned at your season of the acquisition of a SSL endorsement.
A SSL endorsement gives an additional layer of security for touchy information that you
don’t need outsider aggressors to get to. This extra security can be critical with regards to
running online business sites.
A few Examples:
✑ When you need to make sure about the transmission of Mastercard information or other delicate data, (for example, somebody’s genuine location and actual personality).
✑ When you run a lead age site that depends on somebody’s genuine data, wherein case you need to utilize HTTPS to protect against malevolent assaults on the client’s information.
There are numerous advantages to HTTPS that merit the slight expense. Keep in mind, if the declaration is absent, an outsider could undoubtedly check the association for delicate information.
What is TLS? How it Applies to HTTPSTLS represents transport layer security. It encodes HTTPS and can be utilized to make sure about email and different conventions. It utilizes cryptographic methods that guarantee information has not been altered since it was sent, that interchanges are with the real individual the correspondence came from, and to keep private information from being seen.
Things kick off with a TLS handshake, the cycle that commences a correspondence meeting that utilizes TLS encryption. This is the place where verification happens, and meeting keys are made. Shiny new meeting keys are produced when two gadgets impart, from the two unique keys cooperating. The consequence of this is more profound, more encoded correspondence.
A Critical Step for HTTPS ― Authenticating the Web ServerThe most basic advance for a HTTPS secure association is guaranteeing that a web worker is who they say they are. That is the reason the SSL authentication is the main piece of this arrangement; it guarantees the proprietor of the webserver is who they say the declaration says it is. It working correspondingly to how a driver’s permit functions ― it affirms the character of the proprietor of the worker.
A layer of assurance from specific kinds of assaults exists when you actualize HTTPS, making this an important staple of your site.
Latest 312-50v11 Dumps Valid Version with 432 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Answer is C:
Approaches Causing Vulnerability to Session Hijacking and their Preventative Solutions
FTP, use FTPS. Implementing these protocols reduces the chance of a successful hijack by sending data using encryption and digital certificates. (P.1458/1442)