Which of the following methods should the tester use to visualize the authorization information being transmitted?
A penetration tester captured the following traffic during a web-application test:
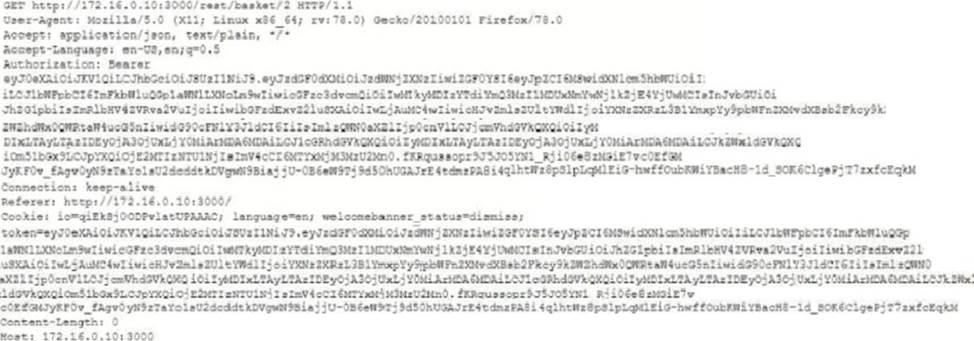
Which of the following methods should the tester use to visualize the authorization information being transmitted?
A . Decode the authorization header using UTF-8.
B. Decrypt the authorization header using bcrypt.
C. Decode the authorization header using Base64.
D. Decrypt the authorization header using AES.
Answer: C
Latest PT0-002 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

