Which of the following is the most effective solution that should be implemented?
A company plans to conduct a network security audit. The web application is hosted on an Auto Scaling group of EC2 Instances with an Application Load Balancer in front to evenly distribute the incoming traffic. A Solutions Architect has been tasked to enhance the security posture of the company’s cloud infrastructure and minimize the impact of DDoS attacks on its resources.
Which of the following is the most effective solution that should be implemented?
A . Configure Amazon CloudFront distribution and set a Network Load Balancer as the origin. Use Amazon GuardDuty to block suspicious hosts based on its security findings. Set up a custom AWS Lambda function that processes the security logs and invokes Amazon SNS for notification.
B . Configure Amazon CloudFront distribution and set Application Load Balancer as the origin. Create a rate-based web ACL rule using AWS WAF and associate it with Amazon CloudFront.
C . Configure Amazon CloudFront distribution and set a Network Load Balancer as the origin. Use VPC Flow Logs to monitor abnormal traffic patterns. Set up a custom AWS Lambda function that processes the flow logs and invokes Amazon SNS for notification.
D . Configure Amazon CloudFront distribution and set an Application Load Balancer as the origin.
Create a security group rule and deny all the suspicious addresses. Use Amazon SNS for notification.
Answer: B
Explanation:
AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources. AWS WAF gives you control over how traffic reaches your applications by enabling you to create security rules that block common attack patterns, such as SQL injection or cross-site scripting, and rules that filter out specific traffic patterns you define. You can deploy AWS WAF on Amazon CloudFront as part of your CDN solution, the Application Load Balancer that fronts your web servers or origin servers running on EC2, or Amazon API Gateway for your APIs.
To detect and mitigate DDoS attacks, you can use AWS WAF in addition to AWS Shield. AWS WAF is a web application firewall that helps detect and mitigate web application layer DDoS attacks by inspecting traffic inline. Application layer DDoS attacks use well-formed but malicious requests to evade mitigation and consume application resources. You can define custom security rules that contain a set of conditions, rules, and actions to block attacking traffic. After you define web ACLs, you can apply them to CloudFront distributions, and web ACLs are evaluated in the priority order you specified when you configured them.
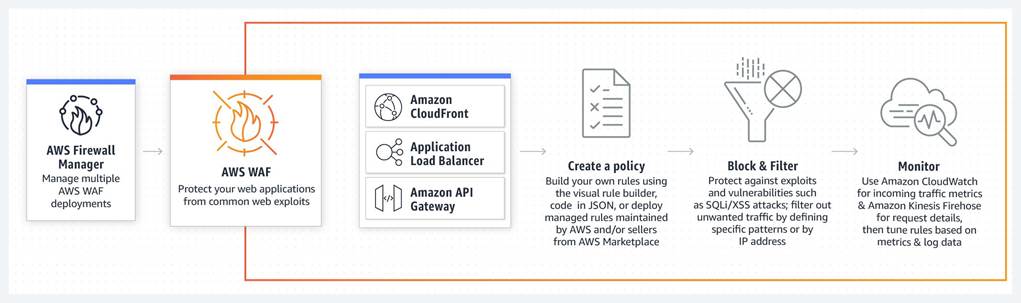
By using AWS WAF, you can configure web access control lists (Web ACLs) on your CloudFront
distributions or Application Load Balancers to filter and block requests based on request signatures.
Each Web ACL consists of rules that you can configure to string match or regex match one or more
request attributes, such as the URI, query-string, HTTP method, or header key. In addition, by using
AWS WAF’s rate-based rules, you can automatically block the IP addresses of bad actors when requests
matching a rule exceed a threshold that you define. Requests from offending client IP addresses will
receive 403 Forbidden error responses and will remain blocked until request rates drop below the
threshold. This is useful for mitigating HTTP flood attacks that are disguised as regular web traffic.
It is recommended that you add web ACLs with rate-based rules as part of your AWS Shield Advanced protection. These rules can alert you to sudden spikes in traffic that might indicate a potential DDoS event. A rate-based rule counts the requests that arrive from any individual address in any five-minute period. If the number of requests exceeds the limit that you define, the rule can trigger an action such as sending you a notification.
Hence, the correct answer is: Configure Amazon CloudFront distribution and set Application Load Balancer as the origin. Create a rate-based web ACL rule using AWS WAF and associate it with Amazon CloudFront.
The option that says: Configure Amazon CloudFront distribution and set a Network Load Balancer as the origin. Use VPC Flow Logs to monitor abnormal traffic patterns. Set up a custom AWS Lambda function that processes the flow logs and invokes Amazon SNS for notification is incorrect because this option only allows you to monitor the traffic that is reaching your instance. You can’t use VPC Flow Logs to mitigate DDoS attacks.
The option that says: Configure Amazon CloudFront distribution and set an Application Load Balancer as the origin. Create a security group rule and deny all the suspicious addresses. Use Amazon SNS for notification is incorrect. To deny suspicious addresses, you must manually insert the IP addresses of these hosts. This is a manual task which is not a sustainable solution. Take note that attackers generate large volumes of packets or requests to overwhelm the target system. Using a security group in this scenario won’t help you mitigate DDoS attacks.
The option that says: Configure Amazon CloudFront distribution and set a Network Load Balancer as the
origin. Use Amazon GuardDuty to block suspicious hosts based on its security findings. Set up a custom
AWS Lambda function that processes the security logs and invokes Amazon SNS for notification is
incorrect because Amazon GuardDuty is just a threat detection service. You should use AWS WAF and
create your own AWS WAF rate-based rules for mitigating HTTP flood attacks that are disguised as
regular web traffic.
References:
https://docs.aws.amazon.com/waf/latest/developerguide/ddos-overview.html
https://docs.aws.amazon.com/waf/latest/developerguide/ddos-get-started-rate-based-rules.html
https://d0.awsstatic.com/whitepapers/Security/DDoS_White_Paper.pdf
Check out this AWS WAF Cheat Sheet:
https://tutorialsdojo.com/aws-waf/
AWS Security Services Overview – WAF, Shield, CloudHSM, KMS:
https://www.youtube.com/watch?v=-1S-RdeAmMo
Latest SAA-C03 Dumps Valid Version with 400 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

