Which of the following is the BEST action for the security analyst to take?
While conducting a network infrastructure review, a security analyst discovers a laptop that is plugged into a core switch and hidden behind a desk.
The analyst sees the following on the laptop’s screen:
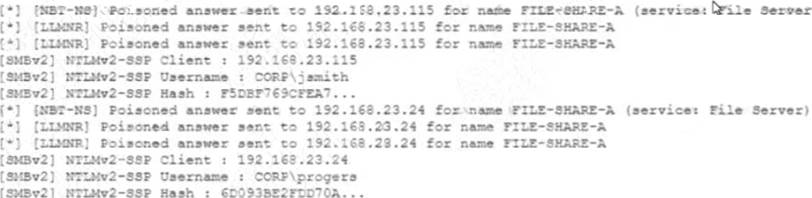
Which of the following is the BEST action for the security analyst to take?
A . Initiate a scan of devices on the network to find password-cracking tools.
B . Disconnect the laptop and ask the users jsmith and progers to log out.
C . Force all users in the domain to change their passwords at the next login.
D . Take the FILE-SHARE-A server offline and scan it for viruses.
Answer: D
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

