autonumA penetration tester ran a simple Python-based scanner.
The following is a snippet of the code:
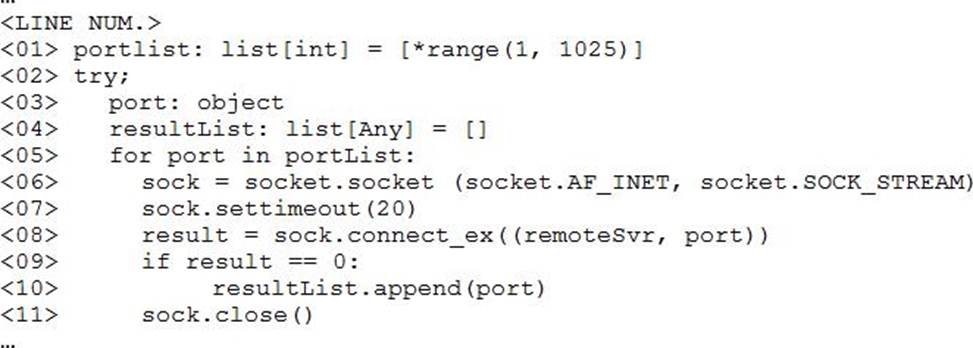
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization’s IDS?
A . sock.settimeout(20) on line 7 caused each next socket to be created every 20 milliseconds.
B . *range(1, 1025) on line 1 populated the portList list in numerical order.
C . Line 6 uses socket.SOCK_STREAM instead of socket.SOCK_DGRAM
D . The remoteSvr variable has neither been type-hinted nor initialized.
Answer: B
Explanation:
Port randomization is widely used in port scanners. By default, Nmap randomizes the scanned port order (except that certain commonly accessible ports are moved near the beginning for efficiency reasons) https://nmap.org/book/man-port-specification.html
Latest PT0-002 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund