Which configuration change is required to allow clients connected to the Corporate SSID to print locally?
Refer to the exhibit.
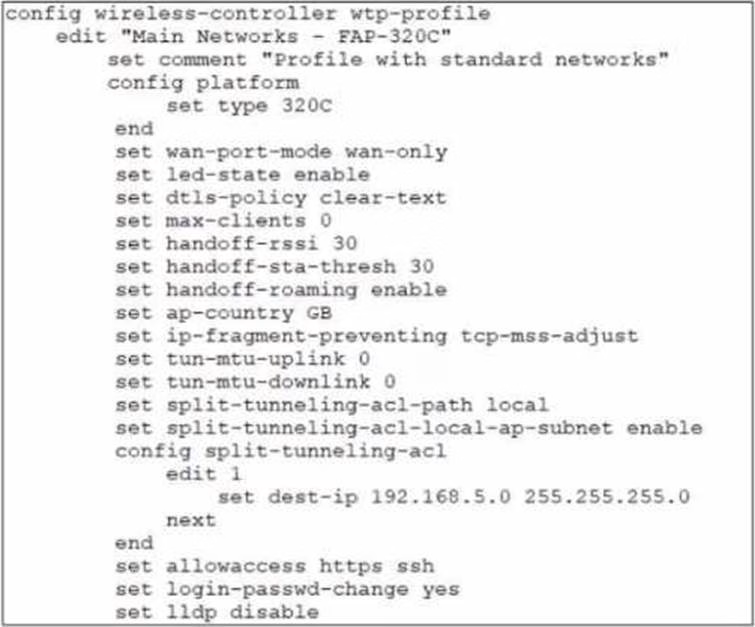
Exhibit.
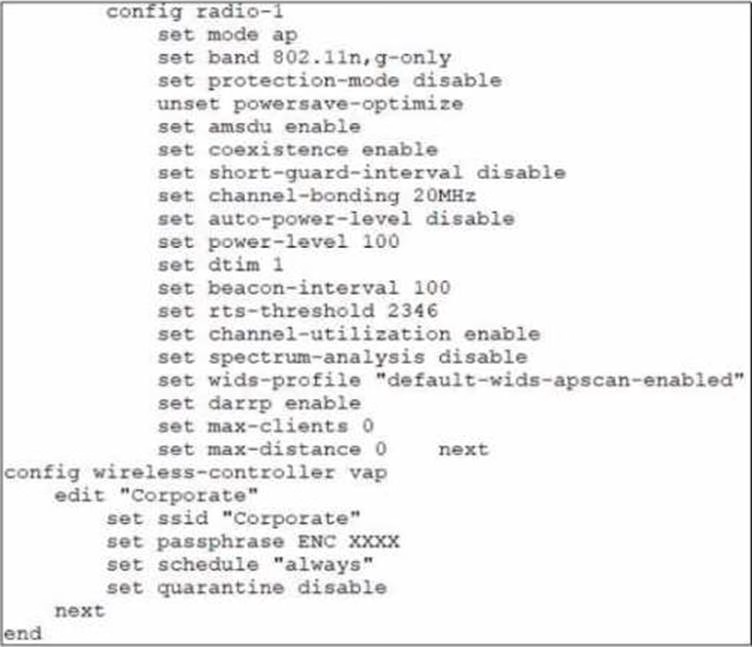
Refer to the exhibits
In the wireless configuration shown in the exhibits, an AP is deployed in a remote site and has a wireless network (VAP) called Corporate deployed to it
The network is a tunneled network however clients connecting to a wireless network require access to a local printer Clients are trying to print to a printer on the remote site but are unable to do so.
Which configuration change is required to allow clients connected to the Corporate SSID to print locally?
A . Configure split-tunneling in the vap configuration
B . Configure split-tunneling in the wtp-profile configuration
C . Disable the Block Intra-SSID Traffic (intra-vap-privacy) setting on the SSID (VAP) profile
D . Configure the printer as a wireless client on the Corporate wireless network
Answer: A
Explanation:
According to the Fortinet documentation1, “Split tunneling allows you to specify which traffic is tunneled to the FortiGate and which traffic is sent directly to the Internet. This can improve performance and reduce bandwidth usage.” Therefore, by configuring split-tunneling in the vap configuration, you can allow the clients connected to the Corporate SSID to access both the corporate network and the local printer. Option B is incorrect because split-tunneling is configured at the vap level, not the wtp-profile level. Option C is incorrect because blocking intra-SSID traffic prevents wireless clients on the same SSID from communicating with each other, which is not related
to accessing a local printer. Option D is unnecessary and impractical because the printer does not need to be a wireless client on the Corporate wireless network to be accessible by the clients.
Latest NSE7_LED-7.0 Dumps Valid Version with 37 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

