What should you recommend?
HOTSPOT
You need to ensure that security policies for the unauthorized detection system are met.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
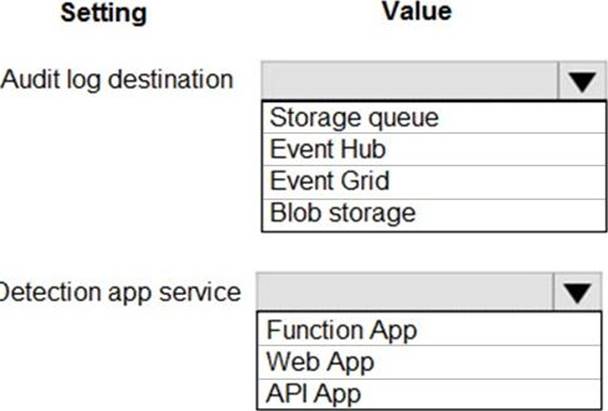
Answer: 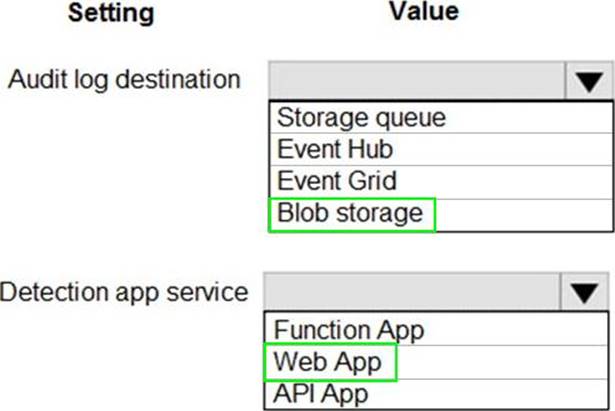
Explanation:
Box 1: Blob storage
Configure blob storage for audit logs.
Scenario: Unauthorized usage of the Planning Assistance data must be detected as quickly as possible. Unauthorized usage is determined by looking for an unusual pattern of usage. Data used for Planning Assistance must be stored in a sharded Azure SQL Database.
Box 2: Web Apps
SQL Advanced Threat Protection (ATP) is to be used.
One of Azure’s most popular service is App Service which enables customers to build and host web applications in the programming language of their choice without managing infrastructure. App Service offers auto-scaling and high availability, supports both Windows and Linux. It also supports automated deployments from GitHub, Visual Studio Team Services or any Git repository. At RSA, we announced that Azure Security Center leverages the scale of the cloud to identify attacks targeting App Service applications.
References: https://azure.microsoft.com/sv-se/blog/azure-security-center-can-identify-attacks-targeting-azureapp-service-applications/
Latest DP-201 Dumps Valid Version with 208 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

