What should you do?
A customer has an Azure Virtual Network named VNet1 that contains an internal standard SKU load balancer named LB1. The backend pool for LB1 includes the following virtual machines: VM1, VM2.
The customer configures a rule named Rul1 to load balance incoming HTTPS requests for VM1 and VM2. Rule1 is associated with an HTTPS health probe. The path for the probe is set to /.
The network adapters of VM1 and VM2 are associated with a network security named NSG1 that contains the following rules:
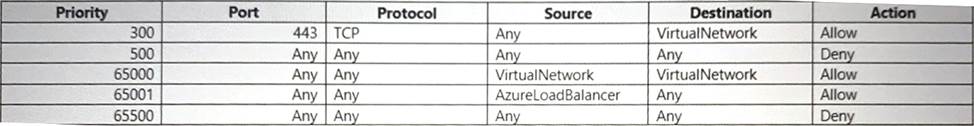
You connect to https://VM1 and https://VM2 from VNet1. Attempts to connect using the front-end IP address of LB1 are failing.
You need to resolve the issue.
What should you do?
A . Change the health probe associated with Rule1 to use HTTP.
B. Add an NSG1 rule with the source set to VirtualNetwork.
C. Change the health probe associated with Rule1 to use TCP.
D. Add an NSG1 rule with the source set to AzureLoadBalancer.
Answer: D
Explanation:
According to Microsoft, Azure Load Balancer health probes originate from the IP address 168.63.129.16 and must not be blocked for probes to mark your instance as up. The AzureLoadBalancer service tag identifies this source IP address in your network security groups and permits health probe traffic by default1. https://learn.microsoft.com/en-us/azure/load-balancer/load-balancer-custom-probe-overview
Latest AZ-720 Dumps Valid Version with 81 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


The correct answer is Change the health probe associated with Rule1 to use TCP.
since the probes are listing on 443 with TCP.