What should you do?
You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.
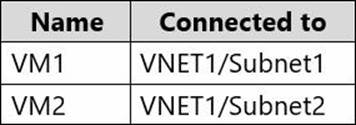
KeyVault1 has an access policy that provides several users with Create Key permissions.
You need to ensure that the users can only register secrets in KeyVault1 from VM1.
What should you do?
A . Create a network security group (NSG) that is linked to Subnet1.
B . Configure the Firewall and virtual networks settings for KeyVault1.
C . Modify the access policy for KeyVault1.
D . Configure KeyVault1 to use a hardware security module (HSM).
Answer: C
Explanation:
You grant data plane access by setting Key Vault access policies for a key vault.
Note 1: Grant our VM’s system-assigned managed identity access to the Key Vault.
✑ Select Access policies and click Add new.
✑ In Configure from template, select Secret Management.
✑ Choose Select Principal, and in the search field enter the name of the VM you created earlier. Select the VM in the result list and click Select.
✑ Click OK to finishing adding the new access policy, and OK to finish access policy selection.
Note 2: Access to a key vault is controlled through two interfaces: the management plane and the data plane. The management plane is where you manage Key Vault itself. Operations in this plane include creating and deleting key vaults, retrieving Key Vault properties, and updating access policies. The data plane is where you work with the data stored in a key vault. You can add, delete, and modify keys, secrets, and certificates.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm-access-nonaad
https://docs.microsoft.com/en-us/azure/key-vault/general/secure-your-key-vault2
Latest AZ-303 Dumps Valid Version with 206 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

