What requires configuration of both a key store and a trust store for an HTTP Listener?
What requires configuration of both a key store and a trust store for an HTTP Listener?
A . Support for TLS mutual (two-way) authentication with HTTP clients
B . Encryption of requests to both subdomains and API resource endpoints fhttPs://aDi.customer.com/ and https://customer.com/api)
C . Encryption of both HTTP request and HTTP response bodies for all HTTP clients
D . Encryption of both HTTP request header and HTTP request body for all HTTP clients
Answer: A
Explanation:
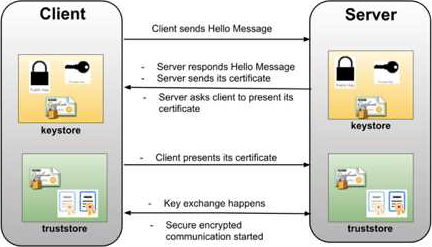
1 way SSL: The server presents its certificate to the client and the client adds it to its list of trusted certificate. And so, the client can talk to the server.
2-way SSL: The same principle but both ways. i.e. both the client and the server has to establish trust between themselves using a trusted certificate. In this way of a digital handshake, the server needs to present a certificate to authenticate itself to client and client has to present its certificate to server.
* TLS is a cryptographic protocol that provides communications security for your Mule app.
* TLS offers many different ways of exchanging keys for authentication, encrypting data, and guaranteeing message integrity Keystores and Truststores Truststore and keystore contents differ depending on whether they are used for clients or servers:
For servers: the truststore contains certificates of the trusted clients, the keystore contains the
private and public key of the server. For clients: the truststore contains certificates of the trusted servers, the keystore contains the private and public key of the client.
Adding both a keystore and a truststore to the configuration implements two-way TLS authentication also known as mutual authentication.
* in this case, correct answer is Support for TLS mutual (two-way) authentication with HTTP clients.
Latest MuleSoft Integration Architect I Dumps Valid Version with 244 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

