What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit.
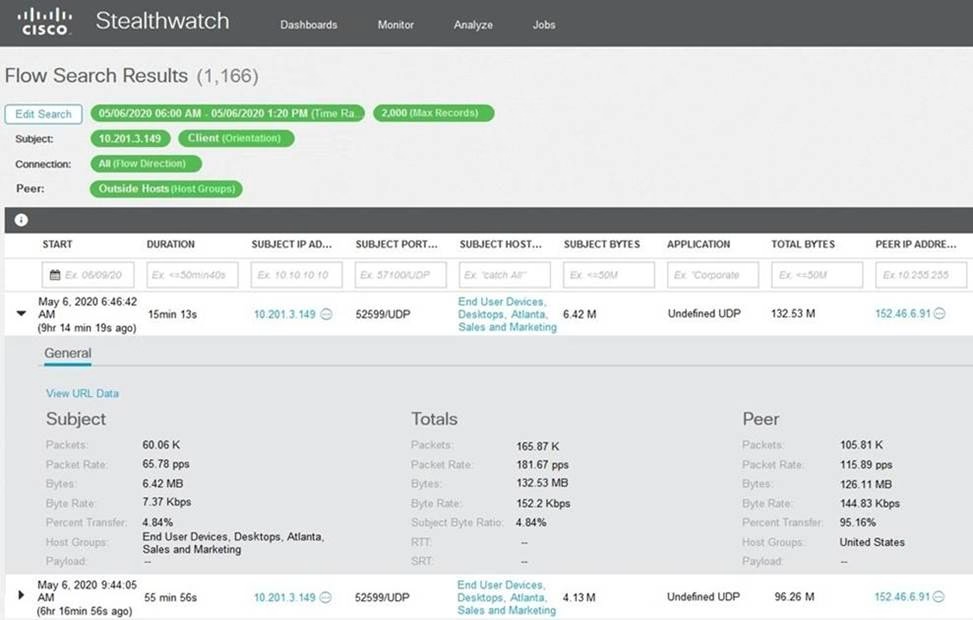
What is the potential threat identified in this Stealthwatch dashboard?
A . Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
B . Host 152.46.6.91 is being identified as a watchlist country for data transfer.
C . Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
D . Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Answer: D
Explanation:
The exhibit shows a Stealthwatch dashboard displaying information on alarming hosts, alarms by type, and today’s alarms. On the left side under “Top Alarming Hosts,” there are five host IP addresses listed with their respective categories indicating different types of alerts including ‘Data Hoarding’ and ‘Exfiltration.’ In “Alarms by Type” section at center top part of image shows bar graphs representing various alarm types including ‘Crypto Violation’ with their respective counts. On right side under “Today’s Alarms,” there’s a table showing the details of each alarm such as the host IP, the alarm type, the severity, and the time. The potential threat identified in this dashboard is that host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91, which is a sign of data exfiltration. Data exfiltration is the unauthorized transfer of data from a compromised system to an external destination, such as a command and control server or a malicious actor. This can result in data loss, breach of confidentiality, and damage to the organization’s reputation and assets.
Reference: = Cisco Cybersecurity Operations Fundamentals – Module 7: Network and Host Forensics
Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

