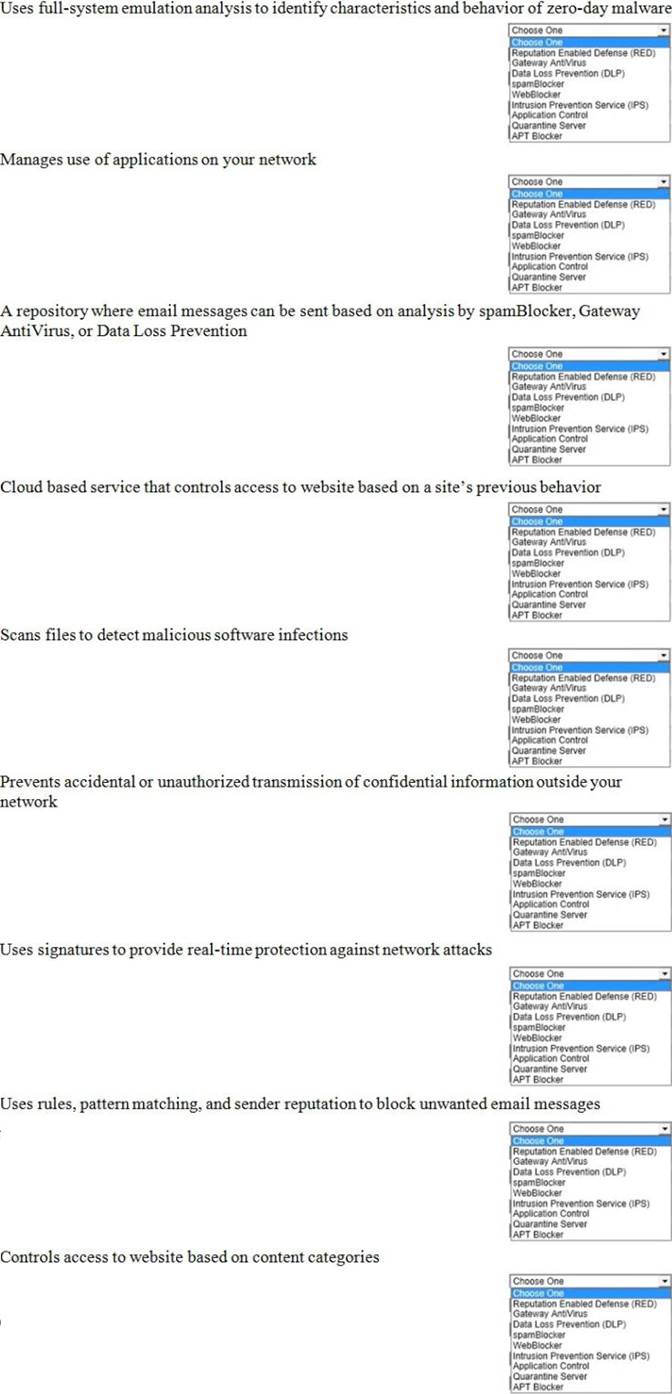
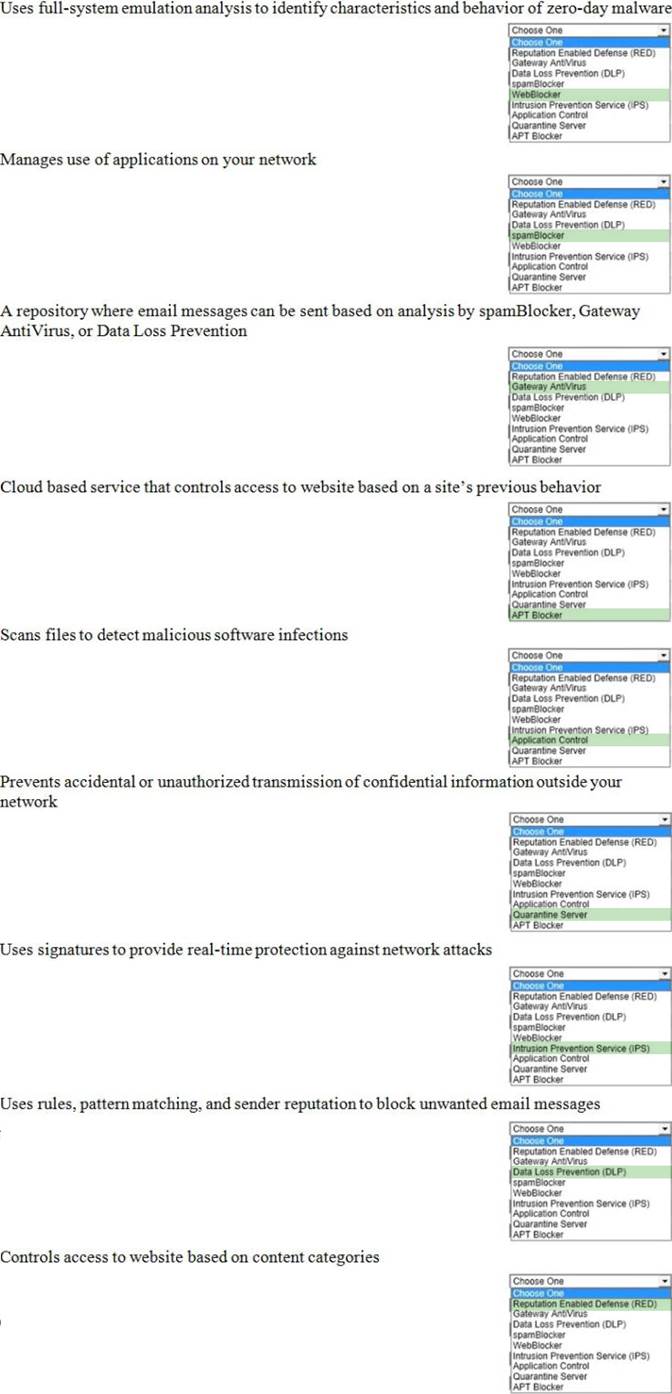
WatchGuard Essentials Fireware Essentials Exam Online Training
WatchGuard Essentials Online Training
The questions for Essentials were last updated at Feb 12,2026.
- Exam Code: Essentials
- Exam Name: Fireware Essentials Exam
- Certification Provider: WatchGuard
- Latest update: Feb 12,2026
You configured four Device Administrator user accounts for your Firebox.
To see a report of witch Device Management users have made changes to the device configuration, what must you do? (Select two.)
- A . Start Firebox System Manager for the device and review the activity for the Management Users on the Authentication List tab.
- B . Connect to Report Manager or Dimension and view the Audit Trail report for your device.
- C . Open WatchGuard Server Center and review the configuration history for managed devices.
- D . Configure your device to send audit trail log messages to your WatchGuard Log Server or Dimension Log Server.
Which takes precedence: WebBlocker category match or a WebBlocker exception?
- A . WebBlocker exception
- B . WebBlocker category match
From the Firebox System Manager >Authentication List tab, you can view all of the authenticated users connected to your Firebox and disconnect any of them.
- A . True
- B . False
Users on the trusted network cannot browse Internet websites.
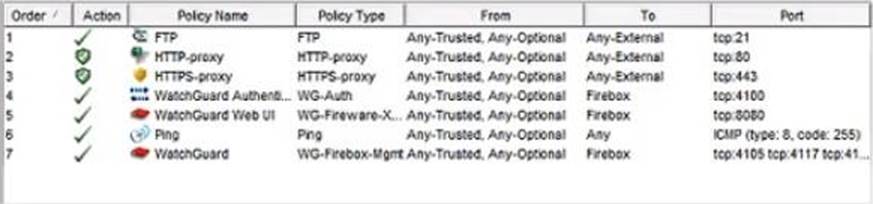
Based on the configuration shown in this image, what could be the problem with this policy configuration? (Select one.)
- A . The default Outgoing policy has been removed and there is no policy to allow DNS traffic.
- B . The HTTP-proxy policy has higher precedence than the HTTPS-proxy policy.
- C . The HTTP-proxy policy is configured for the wrong port.
- D . The HTTP-proxy allows Any-Trusted and Any-Optional to Any-External.
Which of these threats can the Firebox prevent with the default packet handling settings? (Select four.)
- A . Access to inappropriate websites
- B . Denial of service attacks
- C . Flood attacks
- D . Malware in downloaded files
- E . Port scans
- F . Viruses in email messages
- G . IP spoofing
In the network configuration in this image, which aliases is Eth2 a member of? (Select three.)
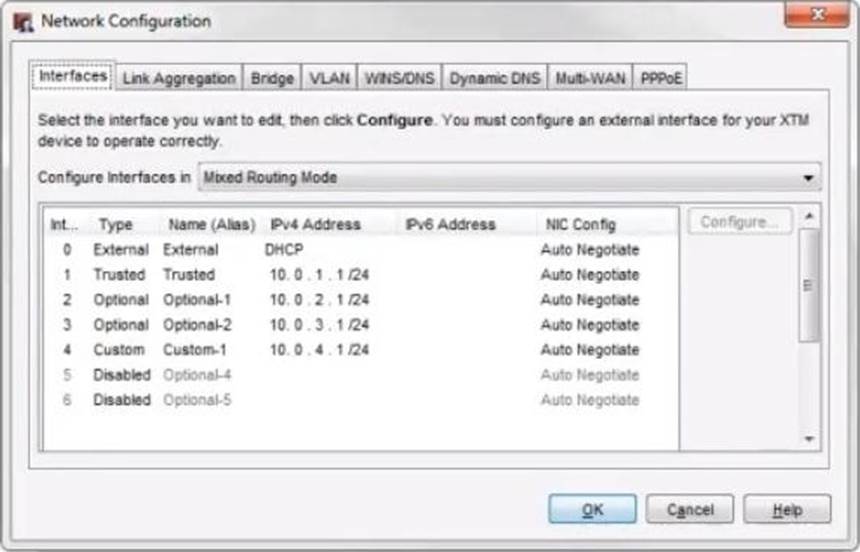
- A . Any-optional
- B . Any-External
- C . Optional-1
- D . Any
- E . Any-Trusted
To enable remote devices to send log messages to Dimension through the gateway Firebox, what must you verify is included in your gateway Firebox configuration? (Select one.)
- A . You can only send log messages to Dimension from a computer that is on the network behind your gateway Firebox.
- B . You must change the connection settings in Dimension, not on the gateway Firebox.
- C . You must add a policy to the remote device configuration file to allow traffic to a Dimension.
- D . You must make sure that either the WG-Logging packet filter policy, or another policy that allows external connections to Dimension over port 4115, is included in the configuration file.
An email newsletter about sales from an external company is sometimes blocked by spamBlocker.
What option could you choose to make sure the newsletter is delivered to your users? (Select one.)
- A . Add a spamBlocker exception based on the From field of the newsletter email.
- B . Set the spamBlocker action to quarantine the email for later retrieval.
- C . Add a spamBlocker subject tag for bulk email messages.
- D . Set the spamBlocker virus outbreak detection action to allow emails from the newsletter source.
You can use Firebox-DB authentication with any type of Mobile VPN.
- A . True
- B . False
Latest Essentials Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund