VMware 5V0-91.20 VMware Carbon Black Portfolio Skills Online Training
VMware 5V0-91.20 Online Training
The questions for 5V0-91.20 were last updated at Dec 17,2025.
- Exam Code: 5V0-91.20
- Exam Name: VMware Carbon Black Portfolio Skills
- Certification Provider: VMware
- Latest update: Dec 17,2025
What is the meaning, if any, of the event Report write (removable media)?
- A . This event would never occur. App Control does not report activity on removable media.
- B . A Policy’s device control setting ‘Block writes to unapproved removable media’ is set to Report Only. The event details show the process, file name, and hash modified or deleted on the removable media.
- C . A Policy’s device control setting ‘Block writes to unapproved removable media’ is set to Report Only. The event details show the process and file name modified or deleted on the unapproved removable media.
- D . A Policy’s device control setting ‘Block writes to unapproved removable media’ is set to Enabled. The event details show the process, file name, and hash modified or deleted on the removable media.
Which statement is true when searching through the EDR server UI?
- A . The backslash is the character to escape characters.
- B . Whitespaces between search terms imply the OR operator.
- C . The percent symbol % is the character to represent a wildcard.
- D . The exclamation point ! is the character to represent negation.
An organization leverages a commonly used software distribution tool to manage deployment of enterprise software and updates. Custom rules are a suitable option to ensure the approval of files delivered by this tool.
Which other trust mechanism could the organization configure for large-scale approval of these files?
- A . Windows Update
- B . Trusted Distributor
- C . Local Approval Mode
- D . Rapid Config
An administrator receives an alert with the TTP DATA_TO_ENCRYPTION.
What is known about the alert based on this TTP even if other parts of the alert are unknown?
- A . A process attempted to delete encrypted data on the disk.
- B . A process attempted to write a file to the disk.
- C . A process attempted to modify a monitored file written by the sensor.
- D . A process attempted to transfer encrypted data on the disk over the network.
An administrator wants to find instances where the binary Is unsigned.
Which term will accomplish this search?
- A . NOT process_publisher:FILE_SIGNATURE_STATE_SIGNED
- B . NOT process_publisher_state:FILE_SIGNATURE_STATE_SIGNED
- C . process_publisher_state:FILE_SIGNATURE_STATE_NOT_SIGNED
- D . process_publisher:FILE_SIGNATURE_STATE_NOT_SIGNED
A Carbon Black administrator received an alert for an untrusted hash executing in the environment.
Which two information items are found in the alert pane? (Choose two.)
- A . Launch Live Query
- B . Launch process analysis
- C . User quarantine
- D . Add hash to banned list
- E . IOC short name
What is the maximum number of binaries (hashes) that can be banned using the web console?
- A . 500
- B . 600
- C . 300
- D . 400
Refer to the exhibit:
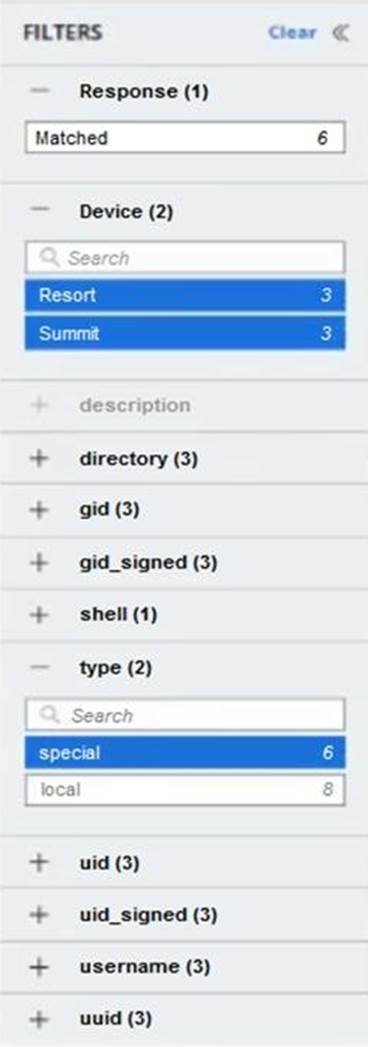
Which two logic statements correctly explain filtering within the UI? (Choose two.)
- A . Filtering between fields is a logical OR
- B . Filtering within the same field is a logical AND
- C . Filtering between fields is a logical AND
- D . Filtering between fields is a logical XOR
- E . Filtering within the same field is a logical OR
When executing a program in App Control, the notification message informs the user that the file is not approved with an option to request approval.
Which Enforcement level is currently enacted?
- A . High
- B . Low
- C . Medium
- D . Default
An alert for a device running a proprietary application is tied to a vital business operation.
Which action is appropriate to take?
- A . Add the application to the Approved List.
- B . Terminate the process.
- C . Deny the operation.
- D . Quarantine the device.
Latest 5V0-91.20 Dumps Valid Version with 116 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

