VMware 5V0-91.20 VMware Carbon Black Portfolio Skills Online Training
VMware 5V0-91.20 Online Training
The questions for 5V0-91.20 were last updated at Apr 24,2025.
- Exam Code: 5V0-91.20
- Exam Name: VMware Carbon Black Portfolio Skills
- Certification Provider: VMware
- Latest update: Apr 24,2025
Which ID in Endpoint Standard is associated with one specific action, involves up to three different hashes (Parent, Process, Target), and occurs on a single device at a specific time?
- A . Threat ID
- B . Process ID
- C . Alert ID
- D . Event ID
There is a requirement to block ransomware when a sensor is offline.
Which blocking and isolation rule fulfills this requirement?
- A . Known Malware ―> Performs ransomware-like behavior ―> Terminate process
- B . Not Listed Application ―> Performs ransomware-like behavior ―> Deny operation
- C . Suspect Malware ―> Performs ransomware-like behavior ―> Deny operation
- D . Unknown Application ―> Performs ransomware-like behavior ―> Terminate process
Carbon Black App Control maintains an inventory of all interesting (executable) files on endpoints where the agent is installed.
What is the initial inventory procedure called, and how can this process be triggered?
- A . Inventorying; enable Discovery mode
- B . Baselining; install the agent
- C . Discovery; place agent into Disabled mode
- D . Initialization; move agent out of Disabled mode
Review the following query:
path:c:program files (x86)microsoft
How would this query input term be interpreted?
- A . c:program files x86microsoft
- B . c:rogram files (x86)icrosoft
- C . c:rogramfilesx86icrosoft
- D . c:program files (x86)microsoft
Which action is only available for the “Performs any operation” and “Performs any API Operation” operation attempts?
- A . Bypass
- B . Allow & Log
- C . Runs or is Running
- D . Allow
An incorrectly constructed watchlist generates 10,000 incorrect alerts.
How should an administrator resolve this issue?
- A . Delete the watchlist to automatically clear the alerts, and then create a new watchlist with the correct criteria.
- B . From the Triage Alerts Page, use the facets to select the watchlist, click the Wrench button to “Mark all as Resolved False Positive”, and then update the watchlist with the correct criteria.
- C . Update the Triage Alerts Page to show 200 alerts, click the Select All Checkbox, click the “Dismiss Alert(s)” button for each page, and then update the watchlist with the correct criteria.
- D . From the Watchlists Page, select the offending watchlist, click “Clear Alerts” from the Action menu, and then update the watchlist with the correct criteria.
A process has created a number of interesting (executable) files in one sequence.
In addition to the event Subtype ‘New Unapproved File to Computer’, what other event subtype is likely to be associated with this sequence?
- A . File Upload Completed
- B . New File Discovered on Startup
- C . File Group Created
- D . File Properties Modified
CORRECT TEXT
Why would a sensor have a status of "Inactive"?
- A . The sensor has not checked in within the last 30 days.
- B . The sensor has been uninstalled from the endpoint for more than 30 days.
- C . The device has been put in bypass for the last 30 days.
- D . The sensor has been in disabled mode for more than 30 days.
An Endpoint Standard analyst runs the query in the graphic below:
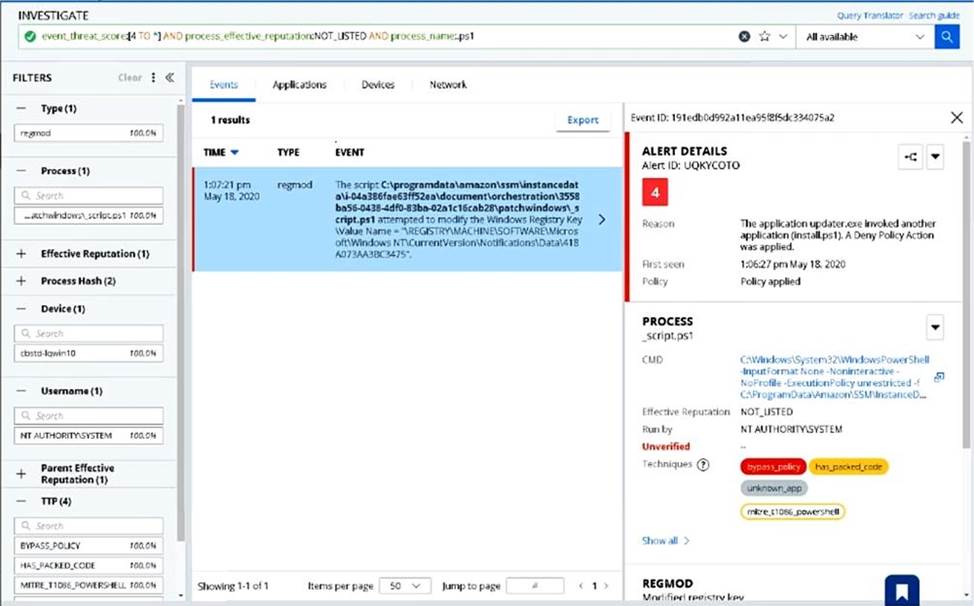
Which three statements are true from the results shown? (Choose three.)
- A . The process is a PowerShell process running a script with a .ps1 extension.
- B . The process has a threat score greater than 4.
- C . The process made a network connection to another system.
- D . The process had a NOT_LISTED reputation at the time the event occurred.
- E . The process was run under the NT_AUTHORITYSYSTEM user context.
- F . The process was able to inject code into another process.
A process wrote an executable file as detailed in the following event:
![]()
Which rule type should be used to ensure that files of the same name and path, written by that process in the future, will not be blocked when they execute?
- A . Trusted Path
- B . File Creation Control
- C . Advances (Write-Ignore)
- D . Trusted Publisher
Latest 5V0-91.20 Dumps Valid Version with 116 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

