VMware 2V0-41.23 VMware NSX 4.x Professional Online Training
VMware 2V0-41.23 Online Training
The questions for 2V0-41.23 were last updated at Dec 15,2025.
- Exam Code: 2V0-41.23
- Exam Name: VMware NSX 4.x Professional
- Certification Provider: VMware
- Latest update: Dec 15,2025
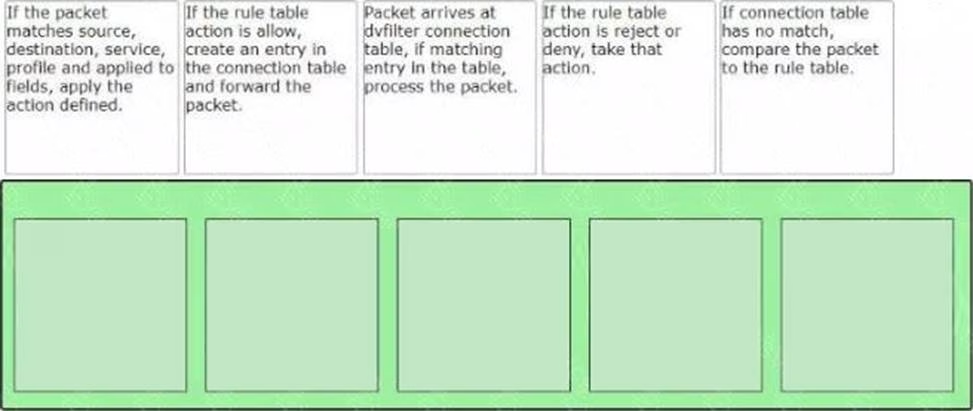
DRAG DROP
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
Which VMware GUI tool is used to identify problems in a physical network?
- A . VMware Aria Automation
- B . VMware Aria Orchestrator
- C . VMware Site Recovery Manager
- D . VMware Aria Operations Networks
DRAG DROP
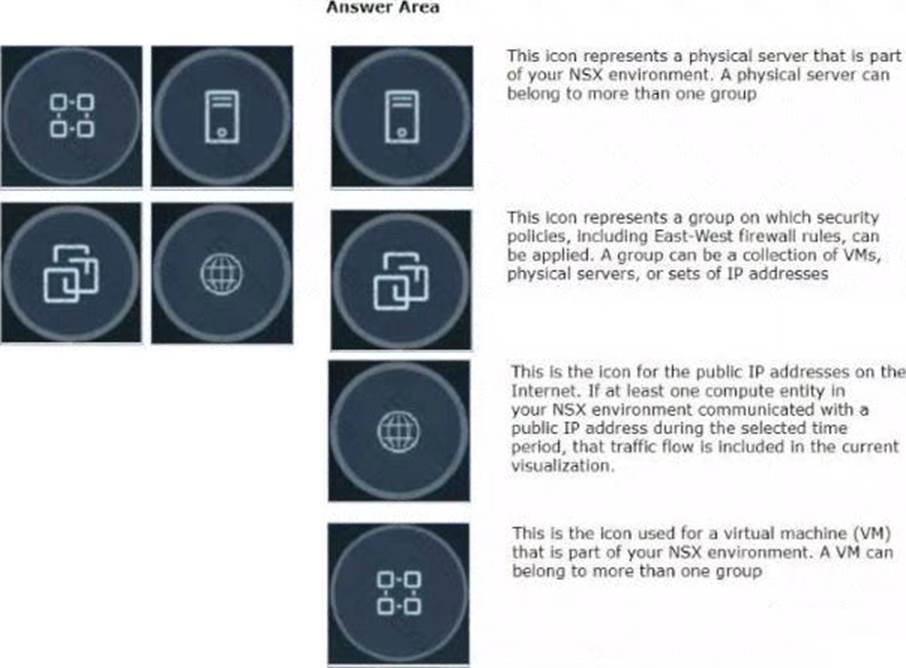
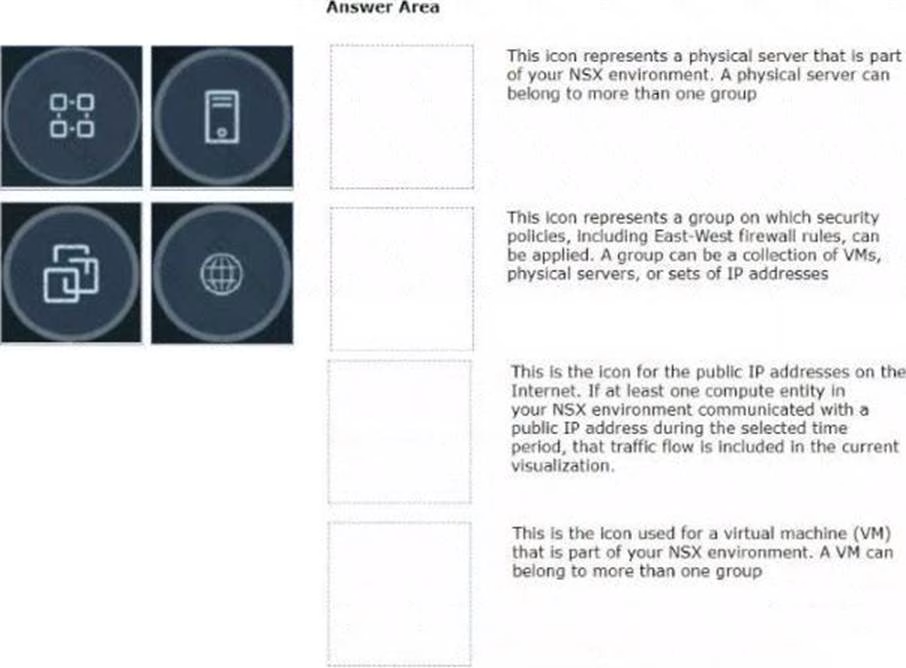
Refer to the exhibits.
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.
An NSX administrator has deployed a single NSX Manager node and will be adding two additional nodes to form a 3-node NSX Management Cluster for a production environment. The administrator will deploy these two additional nodes and Cluster VIP using the NSX UI.
What two are the prerequisites for this configuration? (Choose two.)
- A . All nodes must be in separate subnets.
- B . The cluster configuration must be completed using API.
- C . NSX Manager must reside on a Windows Server.
- D . All nodes must be in the same subnet.
- E . A compute manager must be configured.
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
- A . Use agentless antivirus with Guest Introspection.
- B . Quarantine workloads based on vulnerabilities.
- C . Identify risk and reputation of accessed websites.
- D . Gain Insight about micro-segmentation traffic flows.
- E . Identify security vulnerabilities in the workloads.
When configuring OSPF on a Tler-0 Gateway, which three of the following must match in order to establish a neighbor relationship with an upstream router? (Choose three.)
- A . Naming convention
- B . MTU of the Uplink
- C . Subnet mask
- D . Address of the neighbor
- E . Protocol and Port
- F . Area ID
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
- A . NSX Intrusion Detection and Prevention
- B . NSX Intelligence
- C . NSX Network Detection and Response
- D . NSX Malware Prevention Metrics
- E . NSX Intrinsic Security
What needs to be configured on a Tler-0 Gateway lo make NSX Edge Services available to a VM on a VLAN-backed logical switch?
- A . Downlink Interface
- B . VLAN Uplink
- C . Loopback Router Port
- D . Service Interface
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
- A . Reinstalling the NSX VIBs on the ESXi host.
- B . Restarting the NTPservice on the ESXi host.
- C . Changing the lime zone on the ESXi host.
- D . Reconfiguring the ESXI host with a local NTP server.
NSX improves the security of today’s modern workloads by preventing lateral movement, which feature of NSX can be used to achieve this?
- A . Network Segmentation
- B . Virtual Security Zones
- C . Edge Firewalling
- D . Dynamic Routing
Latest 2V0-41.23 Dumps Valid Version with 70 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund