VMware 2V0-41.23 VMware NSX 4.x Professional Online Training
VMware 2V0-41.23 Online Training
The questions for 2V0-41.23 were last updated at Dec 23,2025.
- Exam Code: 2V0-41.23
- Exam Name: VMware NSX 4.x Professional
- Certification Provider: VMware
- Latest update: Dec 23,2025
Refer to the exhibit.
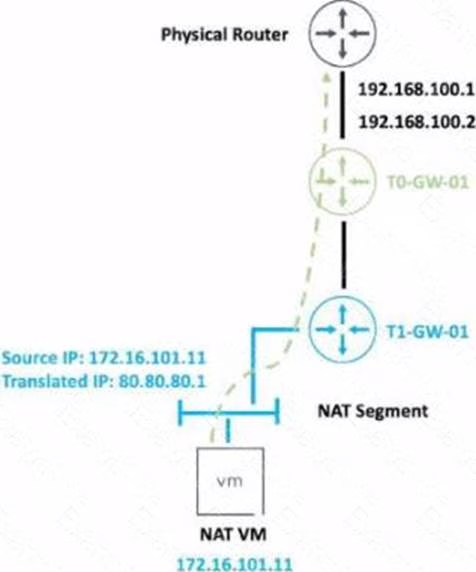
An administrator would like to change the private IP address of the NAT VM I72.l6.101.il to a public address of 80.80.80.1 as the packets leave the NAT-Segment network.
Which type of NAT solution should be implemented to achieve this?
- A . DNAT
- B . SNAT
- C . Reflexive NAT
- D . NAT64
Which two choices are solutions offered by the VMware NSX portfolio? (Choose two.)
- A . VMware Tanzu Kubernetes Grid
- B . VMware Tanzu Kubernetes Cluster
- C . VMware NSX Advanced Load Balancer
- D . VMware NSX Distributed IDS/IPS
- E . VMware Aria Automation
When a stateful service is enabled for the first lime on a Tier-0 Gateway, what happens on the NSX Edge node’
- A . SR is instantiated and automatically connected with DR.
- B . DR Is instantiated and automatically connected with SR.
- C . SR and DR Is instantiated but requites manual connection.
- D . SR and DR doesn’t need to be connected to provide any stateful services.
A company Is deploying NSX micro-segmentation in their vSphere environment to secure a simple application composed of web. app, and database tiers.
The naming convention will be:
• WKS-WEB-SRV-XXX
• WKY-APP-SRR-XXX
• WKI-DB-SRR-XXX
What is the optimal way to group them to enforce security policies from NSX?
- A . Use Edge as a firewall between tiers.
- B . Do a service insertion to accomplish the task.
- C . Group all by means of tags membership.
- D . Create an Ethernet based security policy.
When collecting support bundles through NSX Manager, which files should be excluded for potentially containing sensitive information?
- A . Controller Files
- B . Management Files
- C . Core Files
- D . Audit Files
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)
- A . Can be used as an Exterior Gateway Protocol.
- B . It supports a 4-byte autonomous system number.
- C . The network is divided into areas that are logical groups.
- D . EIGRP Is disabled by default.
- E . BGP is enabled by default.
Which three NSX Edge components are used for North-South Malware Prevention? (Choose three.)
- A . Thin Agent
- B . RAPID
- C . Security Hub
- D . IDS/IPS
- E . Security Analyzer
- F . Reputation Service
Which two statements are true about IDS Signatures? (Choose two.)
- A . Users can upload their own IDS signature definitions.
- B . An IDS signature contains data used to identify known exploits and vulnerabilities.
- C . An IDS signature contains data used to identify the creator of known exploits and vulnerabilities.
- D . IDS signatures can be High Risk, Suspicious, Low Risk and Trustworthy.
- E . An IDS signature contains a set of instructions that determine which traffic is analyzed.
Which NSX CLI command is used to change the authentication policy for local users?
- A . Set cli-timeout
- B . Get auth-policy minimum-password-length
- C . Set hardening- policy
- D . Set auth-policy
Which statement is true about an alarm in a Suppressed state?
- A . An alarm can be suppressed for a specific duration in seconds.
- B . An alarm can be suppressed for a specific duration in days.
- C . An alarm can be suppressed for a specific duration in minutes.
- D . An alarm can be suppressed for a specific duration in hours.
Latest 2V0-41.23 Dumps Valid Version with 70 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

