VMware 2V0-21.23 VMware vSphere 8.x Professional Online Training
VMware 2V0-21.23 Online Training
The questions for 2V0-21.23 were last updated at Jul 26,2025.
- Exam Code: 2V0-21.23
- Exam Name: VMware vSphere 8.x Professional
- Certification Provider: VMware
- Latest update: Jul 26,2025
An administrator manually configures a reference ESXi host that meets company security standards for vSphere environments. The administrator now needs to apply all of the security standards to every identically configured host across multiple vSphere clusters within a single VMware vCenter instance.
Which four steps would the administrator complete to meet this requirement? (Choose four.)
- A . Extract the host profile from the reference host.
- B . Export the host profile from vCenter.
- C . Import host customization on the reference host.
- D . Attach the host profile to each cluster that requires the secure configuration.
- E . Check the compliance of each host against the host profile.
- F . Reset host customization on the reference host.
- G . Remediate all non-compliant hosts.
After a recent unexplained peak in virtual machine (VM) CPU usage, an administrator is asked to monitor the VM performance for a recurrence of the issue.
Which two tools can the administrator use? (Choose two.)
- A . vCenter Management Interface
- B . Direct Console User Interface (DCUI)
- C . vSphere Performance Charts
- D . vCenter Command Line Interface
- E . ESXi Shell
An administrator is tasked with configuring vSphere Trust Authority.
The administrator has completed the following steps:
Set up the workstation –
Enabled the Trust Authority Administrator
Enabled the Trust Authority State
Collected information about the ESXi hosts and vCenter to be trusted
Which step does the administrator need to complete next?
- A . Import the Trusted Host information to the Trust Authority Cluster
- B . Import the Trusted Cluster information to the Trusted Hosts
- C . Create the Key Provider on the Trusted Cluster
- D . Import the Trusted Host information to the Trusted Cluster
Refer to the exhibit.
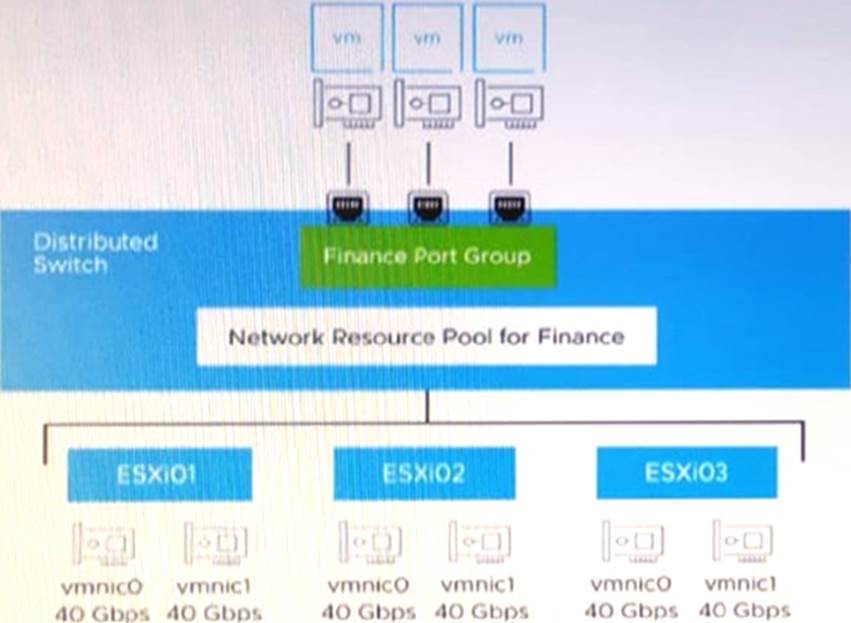
An administrator set up the following configuration:
The distributed switch has three ESXi hosts, and each host has two 40 Gbps NICs.
The amount of bandwidth reserved for virtual machine (VM) traffic is 6 Gbps.
The administrator wants to guarantee that VMs in the Finance distributed port group can access 50 percent of the available reserved bandwidth for VM traffic.
Given this scenario, what should the size (in Gbps) of the Finance network resource pool be?
- A . 18
- B . 80
- C . 36
- D . 120
A vSphere environment is experiencing intermittent short bursts of CPU contention, causing brief production outages for some of the virtual machines (VMs). To understand the cause of the issue, the administrator wants to observe near real-time statistics tor all VMs.
Which two vSphere reporting tools could the administrator use? (Choose two.)
- A . Advanced Performance Charts
- B . esxcli
- C . resxtop
- D . Overview Performance Charts
- E . esxtop
An administrator is performing maintenance activities and discovers that a Virtual Machine File System (VMFS) datastore has a lot more used capacity than expected. The datastore contains 10 virtual machines (VMs) and, when the administrator reviews the contents of the associated datastore, discovers that five virtual machines have a snapshot file (-delta.vmdk files) that has not been modified in over 12 months. The administrator checks the Snapshot Manager within the vSphere Client and confirms that there are no snapshots visible.
Which task should the administrator complete on the virtual machines to free up datastore space?
- A . Consolidate the snapshots for each VM.
- B . Inflate the disk files for each VM.
- C . Delete all snapshots for each VM.
- D . Storage vMotion each VM to another datastore.
An administrator is attempting to configure Storage I/O Control (SIOC) on five datastores within a vSphere environment. The administrator is being asked to determine why SIOC configuration completed successfully on only four of the datastores.
What are two possible reasons why the configuration was not successful? (Choose two.)
- A . The datastore contains Raw Device Mappings (RDMs).
- B . SAS disks are used for the datastore.
- C . The datastore has multiple extents.
- D . The datastore is using ISCSI.
- E . The administrator is using NFS storage.
An administrator has mapped three vSphere zones to three vSphere clusters.
Which two statements are true for this vSphere with Tanzu zonal Supervisor enablement? (Choose two.)
- A . One Supervisor will be created in a specific zone.
- B . One Supervisor will be created across all zones.
- C . Three Supervisors will be created in Linked Mode.
- D . Individual vSphere Namespaces will be placed into a specific zone.
- E . Individual vSphere Namespaces will be spread across all zones.
An administrator is investigating reports of users experiencing difficulties logging into a VMware vCenter instance using LDAP accounts.
Which service should the administrator check as part of troubleshooting?
- A . vSphere Authentication Proxy Service
- B . Lookup Service
- C . Identity Management Service
- D . VMware Authentication Framework Daemon
An administrator is looking to deploy a new VMware vCenter instance. The current environment consists of 75 hosts and is expected to grow up to 100 hosts over the next three years.
Which deployment size should the administrator select?
- A . Medium
- B . Tiny
- C . Large
- D . Small
Latest 2V0-21.23 Dumps Valid Version with 70 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

