Trend Deep Security Professional Trend Micro Certified Professional for Deep Security Exam Online Training
Trend Deep Security Professional Online Training
The questions for Deep Security Professional were last updated at Apr 09,2025.
- Exam Code: Deep Security Professional
- Exam Name: Trend Micro Certified Professional for Deep Security Exam
- Certification Provider: Trend
- Latest update: Apr 09,2025
Question #21
The maximum disk space limit for the Identified Files folder is reached.
What is the expected Deep Security Agent behavior in this scenario?
- A . Any existing files are in the folder are compressed and forwarded to Deep Security Manager to free up disk space.
- B . Deep Security Agents will delete any files that have been in the folder for more than 60 days.
- C . Files will no longer be able to be quarantined. Any new files due to be quarantined will be deleted instead.
- D . Deep Security Agents will delete the oldest files in this folder until 20% of the allocated space is available.
Question #22
The details for an event are displayed in the exhibit. Based on these details, which Protection Module generated the event?
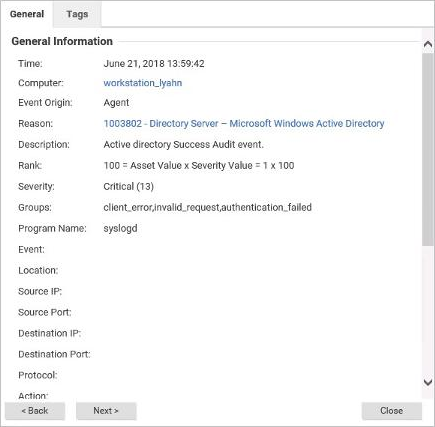
- A . Firewall
- B . Intrusion Prevention
- C . Log Inspection
- D . Integrity Monitoring
Question #23
Which of the following statements is true regarding Deep Security Manager-todatabase com-munication?
- A . Deep Security Manager-to-database traffic is not encrypted by default, but can be en-abled by modifying settings in the ssl.properties file.
- B . Deep Security Manager-to-database traffic is encrypted by default, but can be disabled by modifying settings in the dsm.properties file.
- C . Deep Security Manager-to-database traffic is encrypted by default but can be disabled by modifying settings in the db.properties file.
- D . Deep Security Manager-to-database traffic is not encrypted by default, but can be en-abled by modifying settings in the dsm.properties file.
Question #24
Which of the following statements is true regarding the use of the Firewall Protection Module in Deep Security?
- A . The Firewall Protection Module can check files for certain characteristics such as compression and known exploit code.
- B . The Firewall Protection Module can identify suspicious byte sequences in packets.
- C . The Firewall Protection Module can detect and block Cross Site Scripting and SQL In-jection attacks.
- D . The Firewall Protection Module can prevent DoS attacks coming from multiple systems.
Question #25
Which of the following statements is false regarding the Log Inspection Protection Module?
- A . Custom Log Inspections rules can be created using the Open Source Security (OSSEC) standard.
- B . Deep Security Manager collects Log Inspection Events from Deep Security Agents at every heartbeat.
- C . The Log Inspection Protection Module is supported in both agent-based and agentless environments.
- D . Scan for Recommendations identifies Log Inspection rules that Deep Security should implement.
Latest Deep Security Professional Dumps Valid Version with 80 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments

