Trend Deep Security Professional Trend Micro Certified Professional for Deep Security Exam Online Training
Trend Deep Security Professional Online Training
The questions for Deep Security Professional were last updated at Dec 29,2025.
- Exam Code: Deep Security Professional
- Exam Name: Trend Micro Certified Professional for Deep Security Exam
- Certification Provider: Trend
- Latest update: Dec 29,2025
Which of the following correctly identifies the order of the steps used by the Web Reputation Protection Module to determine if access to a web site should be allowed?
- A . Checks the cache. 2. Checks the Deny list. 3. Checks the Approved list. 4. If not found in any of the above, retrieves the credibility score from Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
- B . Checks the cache. 2. Checks the Approved list. 3. Checks the Deny list. 4. If not found in any of the above, retrieves the credibility score from the Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
- C . Checks the Deny list. 2. Checks the Approved list. 3. Checks the cache. 4. If not found in any of the above, retrieves the credibility score from Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
- D . Checks the Approved list. 2. Checks the Deny list. 3. Checks the cache. 4. If not found in any of the above, retrieves the credibility score from the Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
The "Protection Source when in Combined Mode" settings are configured for a virtual machine as in the exhibit. You would like to enable Application Control on this virtual machine, but there is no corresponding setting displayed.
Why?
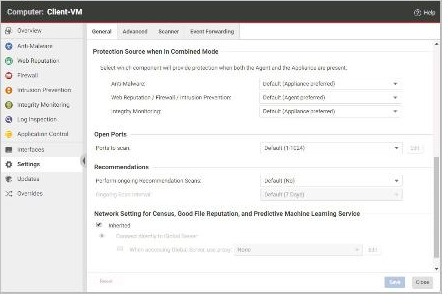
- A . In the example displayed in the exhibit, no activation code was entered for Application Control. Since the Protection Module is not licensed, the corresponding settings are not displayed.
- B . These settings are used when both an host-based agent and agentless protection are available for the virtual machine. Since Application Control is not supported in agentless installations, there is no need for the setting.
- C . In the example displayed in the exhibit, the Application Control Protection Module has not yet been enabled. Once it is enabled for this virtual machine, the corresponding settings are displayed.
- D . In the example displayed in the exhibit, the VMware Guest Introspection Service has not yet been installed. This service is required to enable Application Control in agentless installations.
What is the purpose of the Deep Security Relay?
- A . Deep Security Relays distribute load to the Deep Security Manager nodes in a high-availability implementation.
- B . Deep Security Relays forward policy details to Deep Security Agents and Virtual Ap-pliances immediately after changes to the policy are applied.
- C . Deep Security Relays maintain the caches of policies applied to Deep Security Agents on protected computers to improve performance.
- D . Deep Security Relays are responsible for retrieving security and software updates and distributing them to Deep Security Manager, Agents and Virtual Appliances.
As the administrator in a multi-tenant environment, you would like to monitor the usage of security services by tenants? Which of the following are valid methods for monitoring the usage of the system by the tenants?
- A . Generate a Chargeback report in Deep Security manager Web console.
- B . All the choices listed here are valid.
- C . Use the Representational State Transfer (REST) API to collect usage data from the tenants.
- D . Monitor usage by the tenants from the Statistics tab in the tenant Properties window.
Recommendation scans can detect applications and/or vulnerabilities on servers on the network.
Which of the following Protection Modules make use of Recommendation scans?
- A . Firewall, Application Control, and Integrity Monitoring
- B . Intrusion Prevention, Firewall, Integrity Monitoring and Log Inspection
- C . Log Inspection, Application Control, and Intrusion Prevention
- D . Intrusion Prevention, Integrity Monitoring, and Log Inspection
How can you prevent a file from being scanned for malware?
- A . Enable "File Types scanned by IntelliScan" in the Malware Scan Configuration prop-erties in the Deep Security Manager Web console. Click "Scan All Except" and type the filename to exclude from the scan.
- B . Edit the "Scan Exclusions" section of the dsa.properties configuration file on the Deep Security Agent computer to include the file name. Save the configuration file and restart the Deep Security Agent service.
- C . Add the file to the Exclusions list in the Malware Scan Configuration.
- D . Add the file to the Exclusions list in the "Allowed Spyware/Grayware Configuration".
Which of the following Firewall rule actions will allow data packets to pass through the Firewall Protection Module without being subjected to analysis by the Intrusion Prevention Protection Module?
- A . Deny
- B . Bypass
- C . Allow
- D . Force Allow
Which of the following statements is true regarding the Log Inspection Protection Module?
- A . Deep Security Agents forward Log Inspection Event details to Deep Security Manager in real time.
- B . Log Inspection can only examine new Events and cannot examine logs entries created before the Protection Module was enabled.
- C . Log Inspection can only examine Deep Security log information.
- D . The Log Inspection Protection Module is supported in both Agent-based and Agentless implementations.
Which of the following statements is true regarding the Intrusion Prevention Protection Module?
- A . The Intrusion Prevention Protection Module blocks or allows traffic based on header information within data packets.
- B . The Intrusion Prevention Protection Module analyzes the payload within incoming and outgoing data packets to identify content that can signal an attack.
- C . The Intrusion Prevention Protection Module can identify changes applied to protected objects, such as the Hosts file, or the Windows Registry.
- D . The Intrusion Prevention Protection Module can prevent applications from executing, allowing an organization to block unallowed software.
Based on the policy configuration displayed in the exhibit, which of the following statements is true?
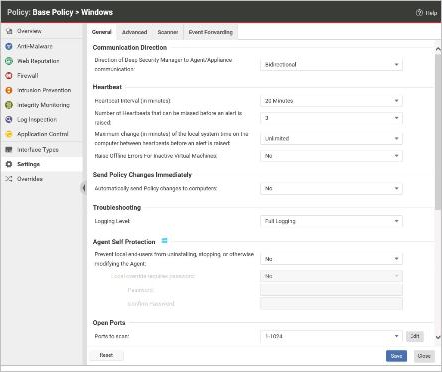
- A . Changes to any of the Deep Security policies will be send to the Deep Security Agents as soon as the changes are saved.
- B . Administrators with access to the protected Server will be able to uninstall the Deep Security Agent through Windows Control Panel.
- C . Deep Security Agents will send event information to Deep Security Manager every 10 minutes.
- D . If the Deep Security Manager does not receive a message from the Deep Security agent every 20 minutes, an alert will be raised.
Latest Deep Security Professional Dumps Valid Version with 80 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

