Topic 3, Litware inc
Topic 3, Litware inc
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking
these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.
Overview
General Overview
Litware, Inc. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
Environment
Existing Environment
The network contains an on-premises Active Directory domain named litware.com.
The domain contains the computers shown in the following table.
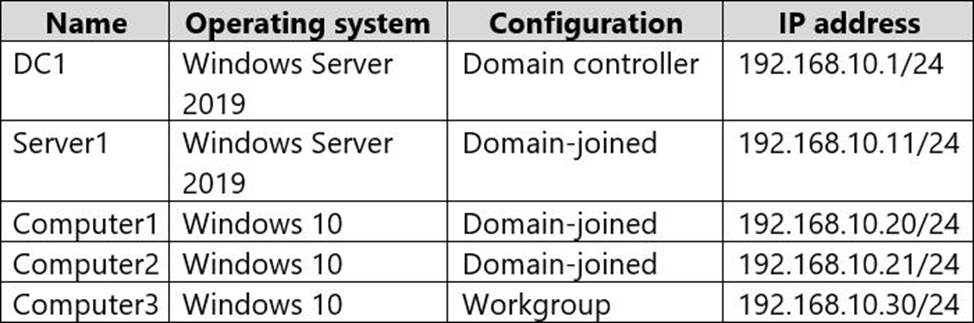
The network that uses 192.168.10.0/24 connects to the internet by using a Network Address Translation (NAT) device.
Windows Admin Center is installed on Server1.
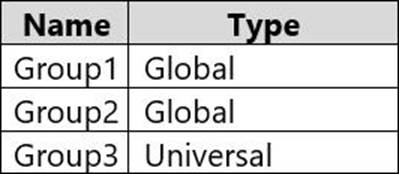
The domain contains the groups shown in the following table.
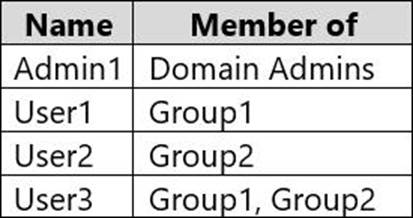
The domain contains the users shown in the following table.
Computer1 Configuration
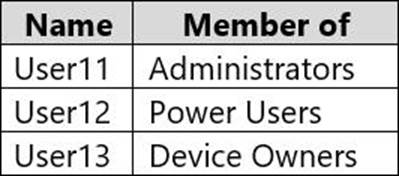
Computer1 contains the local user accounts shown in the following table.
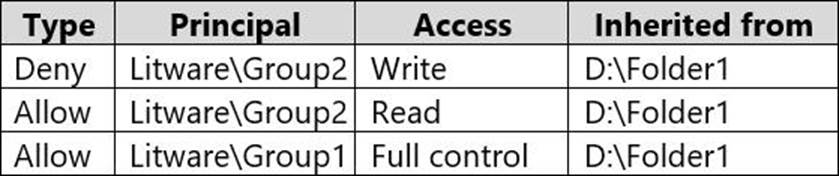
Computer1 contains a folder named D:Folder1 that has permission inheritance disabled.
Computer1 contains a file named D:Folder1Report.docx that has the permissions shown in the following table.
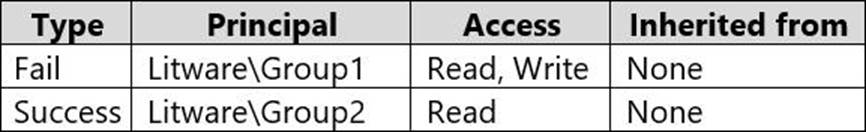
D:Folder1Report.docx has auditing configured as shown in the following table.
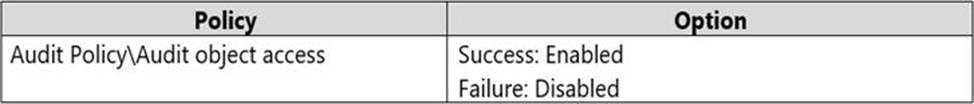
The Local Computer Policy for Computer1 is configured as shown in the following table.
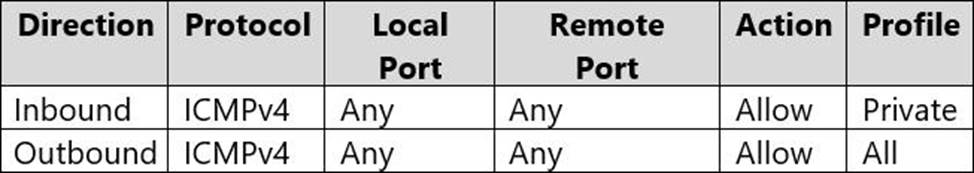
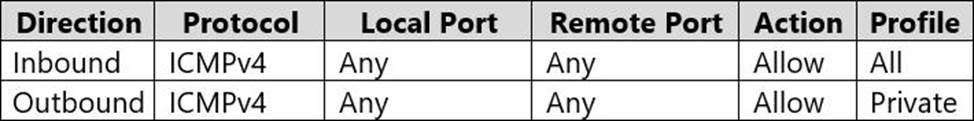
Windows Defender Firewall for Computer1 has the rules shown in the following table.
Computer2 Configuration
Computer2 contains the local user accounts shown in the following table.
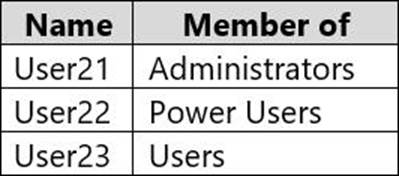
Group1 and Group2 are members of the Remote Desktop Users group.
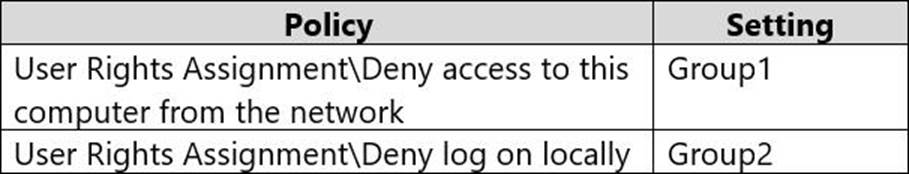
The Local Computer Policy for Computer2 is configured as shown in the following table.
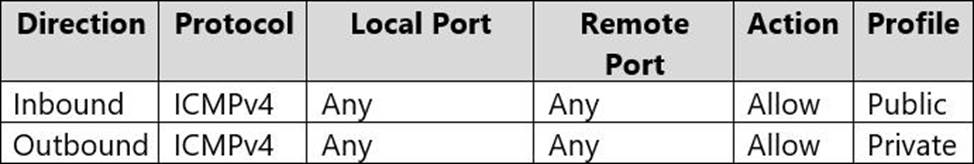
Windows Defender Firewall for Computer2 has the rules shown in the following table.
Computer3 Configuration
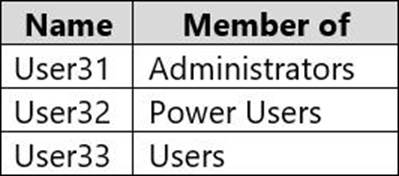
Computer3 contains the local user accounts shown in the following table.
Windows Defender Firewall for Computer3 has the rules shown in the following table.
Requirements and Planned Changes
Planned Changes
Litware plans to make the following changes on Computer1:
✑ Grant User1 Allow Full control permissions to D:Folder1Report.docx.
✑ Grant User2 Allow Full control permissions to D:Folder1Report.docx.
✑ Grant User3 Allow Full control permissions to D:Folder1.
Technical Requirements
Litware identifies the following technical requirements:
✑ Configure custom Visual Effect performance settings for Computer1.
✑ Manage Computer2 by using Windows Admin Center.
✑ Minimize administrative effort.
Delivery Optimization on the computers that run Windows 10 must be configured to meet the following requirements:
✑ Content must be downloaded only from an original source.
✑ Downloading content from peer cache clients must be prevented.
✑ Downloads must be optimized by using the Delivery Optimization cloud service.
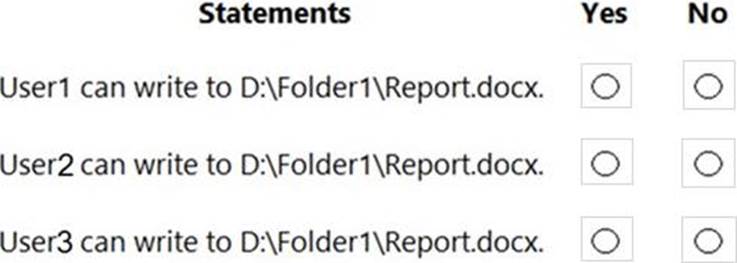
HOTSPOT
You implement the planned changes for Computer1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Answer: 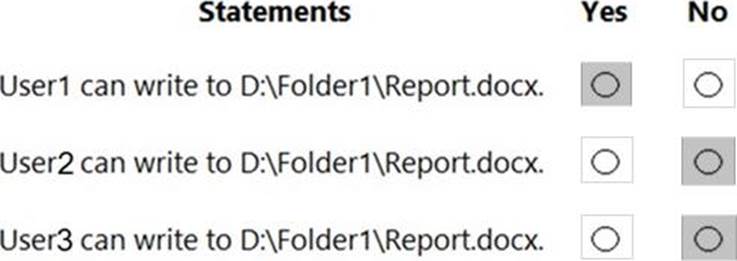
Explanation:
A screenshot of a computer
Description automatically generated with low confidence
Box 1: Yes
User1 already has full control access through membership of Group1. Therefore, User1 can write to the file.
Box 2: No
The planned changes will grant User2 full control access to the file. However, User2 is a member of Group2 which has Deny/Write access. The Deny permission will always take precedence. Therefore, User2 will not be able to write to the file.
Box 3: No
The planned changes will grant User3 full control access to the folder. That permission will be inherited by the file. However, User3 is a member of Group2 which has Deny/Write access. The Deny permission will always take precedence. Therefore, User3 will not be able to write to the file.
Latest MD-100 Dumps Valid Version with 272 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

