The Linux Foundation CKS Certified Kubernetes Security Specialist (CKS) Online Training
The Linux Foundation CKS Online Training
The questions for CKS were last updated at Dec 23,2025.
- Exam Code: CKS
- Exam Name: Certified Kubernetes Security Specialist (CKS)
- Certification Provider: The Linux Foundation
- Latest update: Dec 23,2025
CORRECT TEXT
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:-
✑ a. Ensure that the RotateKubeletServerCertificate argumentissettotrue.
✑ b. Ensure that the admission control plugin PodSecurityPolicyisset.
✑ c. Ensure that the –kubelet-certificate-authority argumentissetasappropriate.
Fix all of the following violations that were found against the Kubelet:-
✑ a. Ensure the –anonymous-auth argumentissettofalse.
✑ b. Ensure that the –authorization-mode argumentissetto Webhook.
Fix all of the following violations that were found against the ETCD:-
✑ a. Ensure that the –auto-tls argumentisnotsettotrue
✑ b. Ensure that the –peer-auto-tls argumentisnotsettotrue
Hint: Take the use of Tool Kube-Bench
CORRECT TEXT
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:-
✑ a. Ensure that the RotateKubeletServerCertificate argumentissettotrue.
✑ b. Ensure that the admission control plugin PodSecurityPolicyisset.
✑ c. Ensure that the –kubelet-certificate-authority argumentissetasappropriate.
Fix all of the following violations that were found against the Kubelet:-
✑ a. Ensure the –anonymous-auth argumentissettofalse.
✑ b. Ensure that the –authorization-mode argumentissetto Webhook.
Fix all of the following violations that were found against the ETCD:-
✑ a. Ensure that the –auto-tls argumentisnotsettotrue
✑ b. Ensure that the –peer-auto-tls argumentisnotsettotrue
Hint: Take the use of Tool Kube-Bench
CORRECT TEXT
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:-
✑ a. Ensure that the RotateKubeletServerCertificate argumentissettotrue.
✑ b. Ensure that the admission control plugin PodSecurityPolicyisset.
✑ c. Ensure that the –kubelet-certificate-authority argumentissetasappropriate.
Fix all of the following violations that were found against the Kubelet:-
✑ a. Ensure the –anonymous-auth argumentissettofalse.
✑ b. Ensure that the –authorization-mode argumentissetto Webhook.
Fix all of the following violations that were found against the ETCD:-
✑ a. Ensure that the –auto-tls argumentisnotsettotrue
✑ b. Ensure that the –peer-auto-tls argumentisnotsettotrue
Hint: Take the use of Tool Kube-Bench
CORRECT TEXT
Fix all issues via configuration and restart the affected components to ensure the new setting takes effect.
Fix all of the following violations that were found against the API server:-
✑ a. Ensure that the RotateKubeletServerCertificate argumentissettotrue.
✑ b. Ensure that the admission control plugin PodSecurityPolicyisset.
✑ c. Ensure that the –kubelet-certificate-authority argumentissetasappropriate.
Fix all of the following violations that were found against the Kubelet:-
✑ a. Ensure the –anonymous-auth argumentissettofalse.
✑ b. Ensure that the –authorization-mode argumentissetto Webhook.
Fix all of the following violations that were found against the ETCD:-
✑ a. Ensure that the –auto-tls argumentisnotsettotrue
✑ b. Ensure that the –peer-auto-tls argumentisnotsettotrue
Hint: Take the use of Tool Kube-Bench
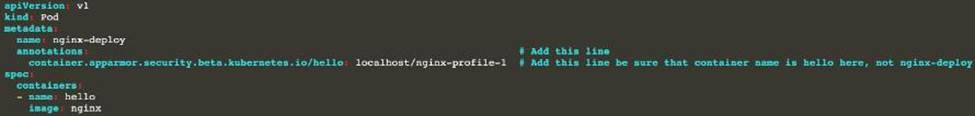
Create the Pod using this manifest
CORRECT TEXT
Using the runtime detection tool Falco, Analyse the container behavior for at least 30 seconds, using filters that detect newly spawning and executing processes store the incident file art /opt/falco-incident.txt, containing the detected incidents. one per line, in the format
[timestamp],[uid],[user-name],[processName]
CORRECT TEXT
Create a new ServiceAccount named backend-sa in the existing namespace default, which has the capability to list the pods inside thenamespace default.
Create a new Pod named backend-pod in the namespace default, mount the newly created sa backend-sa to the pod, and Verify that the pod is able to list pods.
Ensure that the Pod is running.
Latest CKS Dumps Valid Version with 44 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund