The Linux Foundation CKS Certified Kubernetes Security Specialist (CKS) Online Training
The Linux Foundation CKS Online Training
The questions for CKS were last updated at Feb 27,2026.
- Exam Code: CKS
- Exam Name: Certified Kubernetes Security Specialist (CKS)
- Certification Provider: The Linux Foundation
- Latest update: Feb 27,2026
CORRECT TEXT
a. Retrieve the content of the existing secret named default-token-xxxxx in the testing namespace.
Store the value of the token in thetoken.txt
b. Create a new secret named test-db-secret in the DB namespace with the following content:
username: mysql
password: password@123
Create the Pod name test-db-pod of image nginx in the namespace db that can accesstest-db-secret via a volume at path /etc/mysql-credentials
CORRECT TEXT
Create a RuntimeClass named untrusted using the prepared runtime handler named runsc.
Create a Pods of image alpine:3.13.2 in the Namespace default to run on the gVisor runtime class.
Verify: Exec the pods and run the dmesg, you will see output like this:-
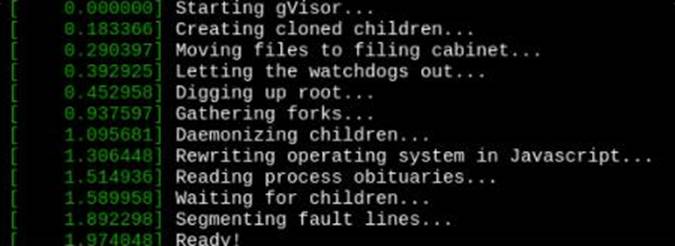
CORRECT TEXT
Create a RuntimeClass named untrusted using the prepared runtime handler named runsc.
Create a Pods of image alpine:3.13.2 in the Namespace default to run on the gVisor runtime class.
Verify: Exec the pods and run the dmesg, you will see output like this:-

CORRECT TEXT
Create a RuntimeClass named untrusted using the prepared runtime handler named runsc.
Create a Pods of image alpine:3.13.2 in the Namespace default to run on the gVisor runtime class.
Verify: Exec the pods and run the dmesg, you will see output like this:-

Pods being configured to be privileged in any way must be treated as potentially not stateless or not immutable.
CORRECT TEXT
Cluster: scanner
Master node: controlplane
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context scanner
Given:
You may use Trivy’s documentation.
Task:
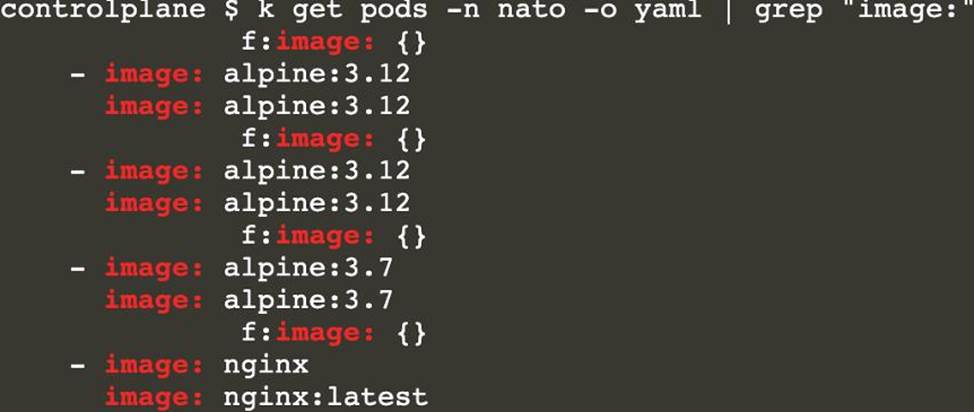
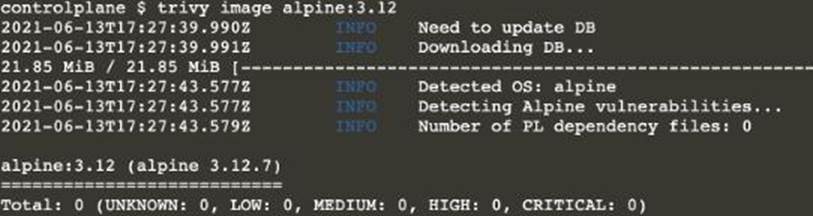
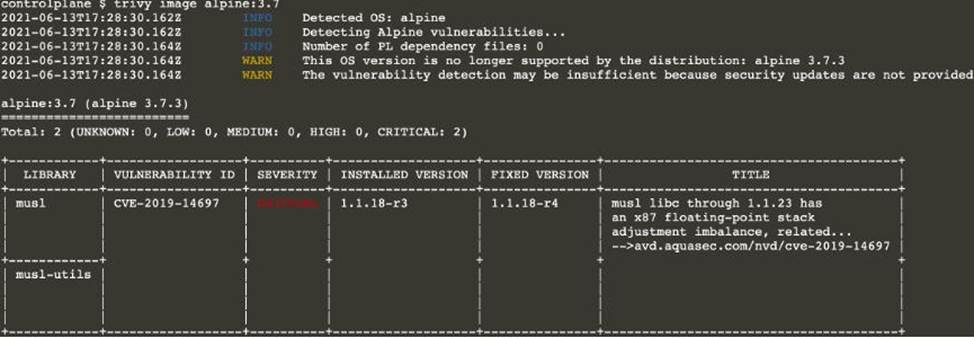
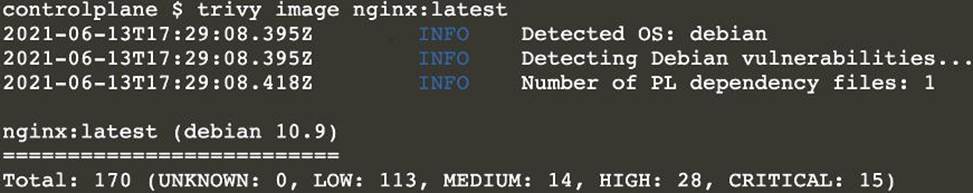
Use the Trivy open-source container scanner to detect images with severe vulnerabilities used by Pods in the namespace nato.
Look for images with High or Critical severity vulnerabilities and delete the Pods that use those images.
Trivy is pre-installed on the cluster’s master node. Use cluster’s master node to use Trivy.
CORRECT TEXT
On the Cluster worker node, enforce the prepared AppArmor profile
✑ #include<tunables/global>
✑
✑ profilenginx-deny flags=(attach_disconnected) {
✑ #include<abstractions/base>
✑
✑ file,
✑
✑ # Deny all file writes.
✑ deny/** w,
✑ }
✑ EOF’
Edit the prepared manifest file to include the AppArmor profile.
✑ apiVersion: v1
✑ kind: Pod
✑ metadata:
✑ name:apparmor-pod
✑ spec:
✑ containers:
✑ – name: apparmor-pod
✑ image: nginx
Finally, apply the manifests files and create the Pod specified on it.
Verify: Try to make a file inside the directory which is restricted.
CORRECT TEXT
On the Cluster worker node, enforce the prepared AppArmor profile
✑ #include<tunables/global>
✑
✑ profilenginx-deny flags=(attach_disconnected) {
✑ #include<abstractions/base>
✑
✑ file,
✑
✑ # Deny all file writes.
✑ deny/** w,
✑ }
✑ EOF’
Edit the prepared manifest file to include the AppArmor profile.
✑ apiVersion: v1
✑ kind: Pod
✑ metadata:
✑ name:apparmor-pod
✑ spec:
✑ containers:
✑ – name: apparmor-pod
✑ image: nginx
Finally, apply the manifests files and create the Pod specified on it.
Verify: Try to make a file inside the directory which is restricted.
CORRECT TEXT
On the Cluster worker node, enforce the prepared AppArmor profile
✑ #include<tunables/global>
✑
✑ profilenginx-deny flags=(attach_disconnected) {
✑ #include<abstractions/base>
✑
✑ file,
✑
✑ # Deny all file writes.
✑ deny/** w,
✑ }
✑ EOF’
Edit the prepared manifest file to include the AppArmor profile.
✑ apiVersion: v1
✑ kind: Pod
✑ metadata:
✑ name:apparmor-pod
✑ spec:
✑ containers:
✑ – name: apparmor-pod
✑ image: nginx
Finally, apply the manifests files and create the Pod specified on it.
Verify: Try to make a file inside the directory which is restricted.
sysdig
Tools are pre-installed on the worker1 node only.
Analyse the container’s behaviour for at least 40 seconds, using filters that detect newly spawning and executing processes.
Store an incident file at /home/cert_masters/report, in the following format:
[timestamp],[uid],[processName]
Note: Make sure to store incident file on the cluster’s worker node, don’t move it to master node.
Latest CKS Dumps Valid Version with 44 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund