The following descriptions are about the packet 1 and the packet 2 fields, which is correct?
Man-in-the-middle attack means that the middleman completes the data exchange between the server and the client. In the server’s view, all the messages are from or sent to the client; in the client’s view, all the messages are also from or sent to the server side. If a hacker uses a man-in-the-middle attack, the hacker will send at least two packets as shown to implement the attack.
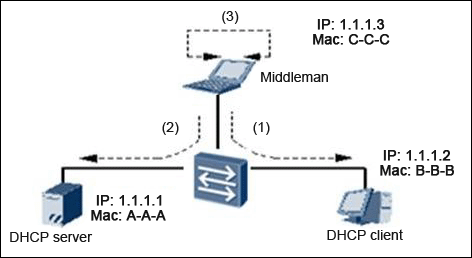
The following descriptions are about the packet 1 and the packet 2 fields, which is correct? (Choose 2 Answers)
A . Data Package 1 :
Source IP 1.1.1.1
Source MAC C-C-C
Destination IP 1.1.1.2
Destination Mac B-B-B
B . Data Package 1 :
Source IP 1.1.1.3
Source MAC C-C-C
Destination IP 1.1.1.2
Destination Mac B-B-B
C . Data Package 2 :
Source IP 1.1.1.2
Source MAC C-C-C
Destination IP 1.1.1.1
Destination Mac A-A-A
D . Data Package 2 :
Source IP 1.1.1.3
Source MAC C-C-C
Destination IP 1.1.1.1
Destination Mac A-A-A
Answer: AC
Latest H12-721-ENU Dumps Valid Version with 342 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

