Symantec 250-437 Administration of Symantec CloudSOC Online Training
Symantec 250-437 Online Training
The questions for 250-437 were last updated at Apr 23,2025.
- Exam Code: 250-437
- Exam Name: Administration of Symantec CloudSOC
- Certification Provider: Symantec
- Latest update: Apr 23,2025
What type of solution should an administrator implement to secure the way users interact with cloud applications?
- A . Intrusion Detection System/Intrusion Protection System (IDS/IPS)
- B . Cloud Access Security Broker (CASB)
- C . Web application firewalls
- D . Proxies
What policy should an administrator utilize to allow users access to Office 365, but prevent the extraction of files when their ThreatScore is higher than 30?
- A . File transfer
- B . Access enforcement
- C . ThreatScore based
- D . Data exposure
What Business Readiness Rating (BRR) category does the subcategory “Password Quality Rules” belong to?
- A . Data
- B . Compliance
- C . Business
- D . Access
How does the Securlet module get data?
- A . Firewall and proxies
- B . CloudSOC gateway
- C . Cloud application APIs
- D . CloudSOC gateway and cloud application APIs
What module should an administrator use to identify anomalous user behavior such as large amounts of data being downloaded, too many files being shared, or logins from suspicious locations?
- A . Detect
- B . Protect
- C . Investigate
- D . Audit
Which detector will trigger if a user attempts a series of invalid logins within a specific time period?
- A . Threats based
- B . Sequence based
- C . Threshold based
- D . Behavior based
What module should an administrator use to view all activities in cloud applications?
- A . Protect
- B . Audit
- C . Detect
- D . Investigate
What module should an administrator use to create policies with one click, and send them to the Protect Module?
- A . Detect
- B . Investigate
- C . Audit
- D . Securlet
What module can an administrator use to connect certain cloud applications to CloudSOC via APIs, and have complete visibility into the content being shared in those cloud applications?
- A . Investigate
- B . Detect
- C . Protect
- D . Securlets
Refer to the exhibit.
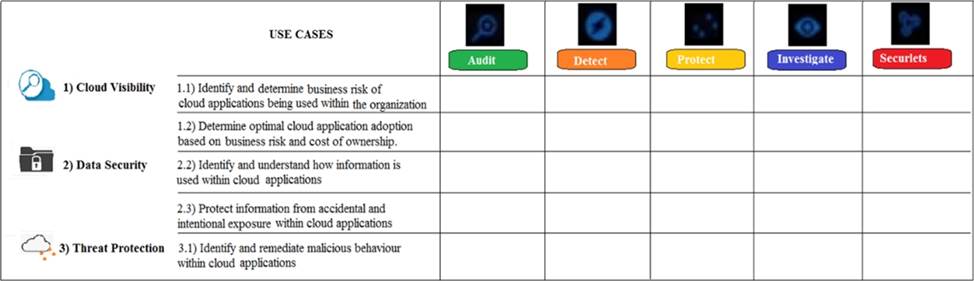
What modules are used by the use case “Identify and determine business risk of cloud applications being used within the organization”?
- A . Investigate
- B . Audit and Investigate
- C . Audit
- D . Audit and Securlets
Latest 250-437 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

