Symantec 250-437 Administration of Symantec CloudSOC Online Training
Symantec 250-437 Online Training
The questions for 250-437 were last updated at Apr 28,2025.
- Exam Code: 250-437
- Exam Name: Administration of Symantec CloudSOC
- Certification Provider: Symantec
- Latest update: Apr 28,2025
How does the Audit module get data?
- A . Firewalls and proxies
- B . Cloud application APIs
- C . CloudSOC gateway
- D . Manual uploads
Which detector will trigger if CloudSOC detects anomalously frequent sharing?
- A . Behavior based
- B . Threshold based
- C . Sequence based
- D . Threats based
Which are three (3) levels of data exposure?
- A . Public, external, and internal
- B . Public, confidential, and company confidential
- C . Public, semi-private, and private
- D . Public, confidential, and private
Refer to the exhibit.
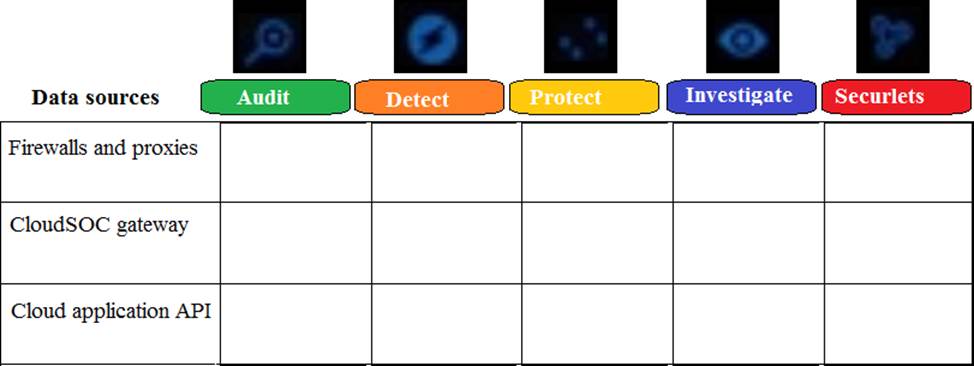
Which CloudSOC module(s) use firewalls and proxies as data sources?
- A . Detect, Protect, and Investigate
- B . Detect, Protect, Investigate, and Securlets
- C . Audit and Investigate
- D . Audit
How should an administrator handle a cloud application that fails to meet compliance requirements, but the business need outweighs the risk?
- A . Sanction
- B . Monitor
- C . Block
- D . Review
Refer to the exhibit.
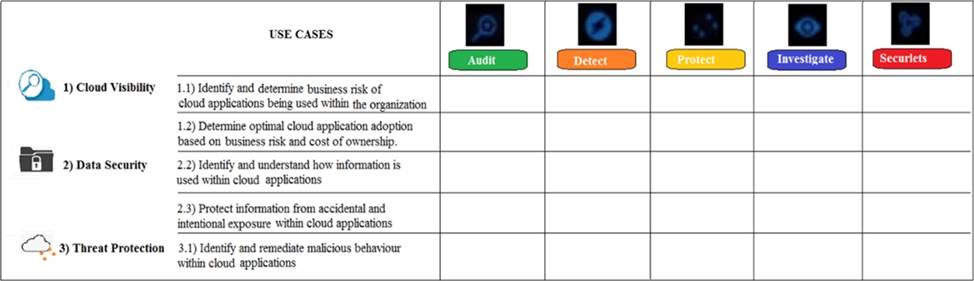
What modules are used in the use case “Protect information from accidental and intentional exposure within cloud applications”?
- A . Protect and Investigate
- B . Protect, Investigate, and Securlets
- C . Protect and Audit
- D . Protect and Securlets
What type of policy should an administrator use to prevent a user that is behaving in anomalous ways from sharing public links while you monitor them?
- A . Access monitoring
- B . File transfer
- C . Data exposure
- D . Access enforcement
What is the objective of File Sharing policies?
- A . To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
- B . To prevent users from sharing documents, either publicly, externally, or internally.
- C . To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
- D . To restrict the uploading and downloading of documents from the user’s computer to the cloud application, based both on the content of the documents, and the characteristics of the user.
Refer to the exhibit.
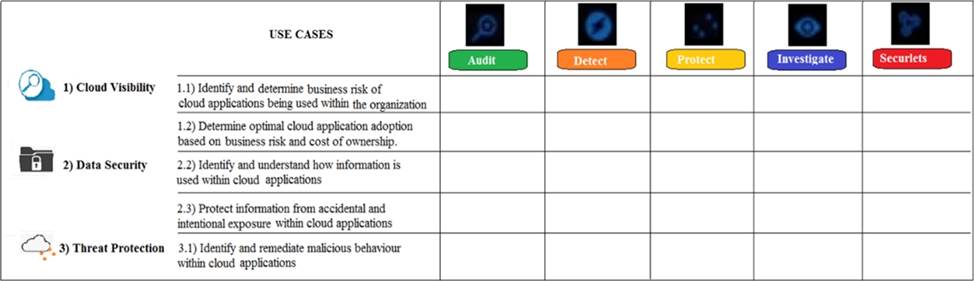
Which modules are used in the use case “Determine optimal cloud application adoption based on business risk and cost of ownership”?
- A . Audit and Protect
- B . Audit
- C . Detect, Protect, and Investigate
- D . Protect, Investigate, and Securlets
Refer to the exhibit.
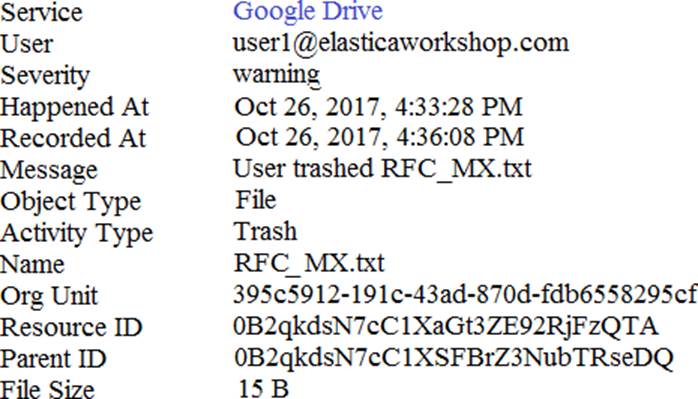
An administrator found this incident in the Investigate module.
What type of policy should an administrator create to get email notifications if the incident happens again?
- A . File sharing policy
- B . File transfer policy
- C . Access monitoring policy
- D . Data exposure policy
Latest 250-437 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

