Swift CSP Assessor Swift Customer Security Programme Assessor Certification Online Training
Swift CSP Assessor Online Training
The questions for CSP Assessor were last updated at Feb 25,2026.
- Exam Code: CSP Assessor
- Exam Name: Swift Customer Security Programme Assessor Certification
- Certification Provider: Swift
- Latest update: Feb 25,2026
A Swift user relies on a sFTP server to connect through an externally exposed connection with a service provider or a group hub.
What architecture type is the Swift user? (Choose all that apply.)

- A . A1
- B . A2
- C . A3
- D . A4
Application Hardening basically applies the following principles. (Choose all that apply.)

- A . Least Privileges
- B . Access on a need to have
- C . Reduced footprint for less potential vulnerabilities
- D . Enhanced Straight Through Processing
Using the outsourcing agent diagram.
Which components must be placed in a secure zone? (Choose all that apply.)

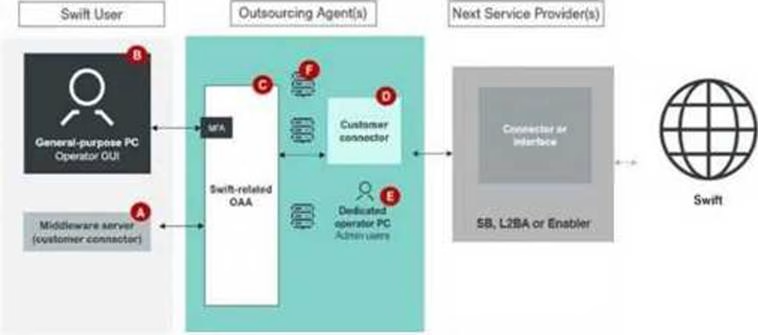
- A . Component A
- B . Component B
- C . Component C
- D . Component D
In the illustration, identify which components are in scope of the CSCF? (Choose all that apply.)


- A . Components A, B, K
- B . Components J, K, I
- C . Components F, G, H
- D . Components C, E, M
Can a Swift user choose to implement the security controls (example: logging and monitoring) in systems which are not directly in scope of the CSCE?

- A . Yes
- B . No
Select the correct statement(s) about the Swift Alliance Gateway. (Choose all that apply.)

- A . It acts as the single window to SwiftNet messaging services by concentrating your traffic flows
- B . It allows sharing of PKI profiles between application or individuals, through the use of virtual profiles
- C . It allows the creation and/or modification of some Swift messages (depending on the types &/or formats)
- D . The Alliance Gateway can only be accessed by a SWIFTNet user
The internet connectivity restriction control prevents having internet access on any CSCE m-scope components.

- A . TRUE
- B . FALSE
Select the correct statement(s).

- A . The public and private keys of a Swift certificate are stored on the Hardware Security Module
- B . The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a message
- C . The decryption operation uses the encryption private key of the receiver
- D . To verify the signature the SwiftNetLink uses the signing private key of the receiver
The Swift HSM boxes:

- A . Are located at the network partner premises and managed by Swift
- B . Are located at the Swift user premises and managed by Swift
- C . Are located at the Swift user premises and managed by the Swift user
- D . Are located at the network partner premises and managed by Swift the network partner
What type of control effectiveness needs to be validated for an independent assessment?

- A . Effectiveness is never validated only the control design
- B . An independent assessment is a point in time review with possible reviews of older evidence as appropriate
- C . Operational effectiveness needs to be validated
- D . None of the above
Latest CSP Assessor Dumps Valid Version with 57 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

