Which of the following are data models used by ES? (Choose all that apply)
- A . Web
- B . Anomalies
- C . Authentication
- D . Network Traffic
A,C,D
Explanation:
Reference: https://dev.splunk.com/enterprise/docs/developapps/enterprisesecurity/datamodelsusedbyes/
In order to include an eventtype in a data model node, what is the next step after extracting the correct fields?
- A . Save the settings.
- B . Apply the correct tags.
- C . Run the correct search.
- D . Visit the CIM dashboard.
C
Explanation:
Reference: https://docs.splunk.com/Documentation/CIM/4.15.0/User/UsetheCIMtonormalizeOSSECdata
A site has a single existing search head which hosts a mix of both CIM and non-CIM compliant applications. All of the applications are mission-critical. The customer wants to carefully control cost, but wants good ES performance .
What is the best practice for installing ES?
- A . Install ES on the existing search head.
- B . Add a new search head and install ES on it.
- C . Increase the number of CPUs and amount of memory on the search head, then install ES.
- D . Delete the non-CIM-compliant apps from the search head, then install ES.
B
Explanation:
Reference: https://www.splunk.com/pdfs/technical-briefs/splunk-validated-architectures.pdf
What are adaptive responses triggered by?
- A . By correlation searches and users on the incident review dashboard.
- B . By correlation searches and custom tech add-ons.
- C . By correlation searches and users on the threat analysis dashboard.
- D . By custom tech add-ons and users on the risk analysis dashboard.
When investigating, what is the best way to store a newly-found IOC?
- A . Paste it into Notepad.
- B . Click the “Add IOC” button.
- C . Click the “Add Artifact” button.
- D . Add it in a text note to the investigation.
A security manager has been working with the executive team en long-range security goals. A primary goal for the team Is to Improve managing user risk in the organization .
Which of the following ES features can help identify users accessing inappropriate web sites?
- A . Configuring the identities lookup with user details to enrich notable event Information for forensic analysis.
- B . Make sure the Authentication data model contains up-to-date events and is properly accelerated.
- C . Configuring user and website watchlists so the User Activity dashboard will highlight unwanted user actions.
- D . Use the Access Anomalies dashboard to identify unusual protocols being used to access corporate sites.
When using distributed configuration management to create the Splunk_TA_ForIndexers package, which three files can be included?
- A . indexes.conf, props.conf, transforms.conf
- B . web.conf, props.conf, transforms.conf
- C . inputs.conf, props.conf, transforms.conf
- D . eventtypes.conf, indexes.conf, tags.conf
A
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.4.1/Install/InstallTechnologyAdd-ons
After installing Enterprise Security, the distributed configuration management tool can be used to create which app to configure indexers?
- A . Splunk_DS_ForIndexers.spl
- B . Splunk_ES_ForIndexers.spl
- C . Splunk_SA_ForIndexers.spl
- D . Splunk_TA_ForIndexers.spl
D
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.1.0/Install/InstallTechnologyAdd-ons
When creating custom correlation searches, what format is used to embed field values in the title, description, and drill-down fields of a notable event?
- A . $fieldname$
- B . “fieldname”
- C . %fieldname%
- D . _fieldname_
A
Explanation:
Reference: https://docs.splunk.com/Documentation/ITSI/4.4.2/Configure/Createcorrelationsearch
What is the first step when preparing to install ES?
- A . Install ES.
- B . Determine the data sources used.
- C . Determine the hardware required.
- D . Determine the size and scope of installation.
A newly built custom dashboard needs to be available to a team of security analysts In ES .
How is It possible to Integrate the new dashboard?
- A . Add links on the ES home page to the new dashboard.
- B . Create a new role Inherited from es_analyst, make the dashboard permissions read-only, and make this dashboard the default view for the new role.
- C . Set the dashboard permissions to allow access by es_analysts and use the navigation editor to add it to the menu.
- D . Add the dashboard to a custom add-in app and install it to ES using the Content Manager.
Which of the following is a key feature of a glass table?
- A . Rigidity.
- B . Customization.
- C . Interactive investigations.
- D . Strong data for later retrieval.
Adaptive response action history is stored in which index?
- A . cim_modactions
- B . modular_history
- C . cim_adaptiveactions
- D . modular_action_history
A
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.1.0/Install/Indexes
What kind of value is in the red box in this picture?
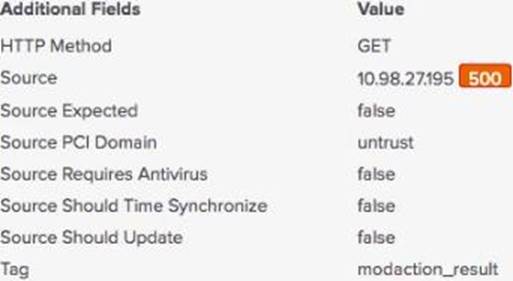
- A . A risk score.
- B . A source ranking.
- C . An event priority.
- D . An IP address rating.
A
Explanation:
Reference: https://docs.splunk.com/Documentation/Splunk/8.0.2/Data/FormateventsforHTTPEventCollector
Which indexes are searched by default for CIM data models?
- A . notable and default
- B . summary and notable
- C . _internal and summary
- D . All indexes
D
Explanation:
Reference: https://answers.splunk.com/answers/600354/indexes-searched-by-cim-data-models.html
The Add-On Builder creates Splunk Apps that start with what?
- A . DA-
- B . SA-
- C . TA-
- D . App-
C
Explanation:
Reference: https://dev.splunk.com/enterprise/docs/developapps/enterprisesecurity/abouttheessolution/
What is the bar across the bottom of any ES window?
- A . The Investigator Workbench.
- B . The Investigation Bar.
- C . The Analyst Bar.
- D . The Compliance Bar.
B
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.4.1/User/Startaninvestigation
Glass tables can display static images and text, the results of ad-hoc searches, and which of the following objects?
- A . Lookup searches.
- B . Summarized data.
- C . Security metrics.
- D . Metrics store searches.
C
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.1.0/User/CreateGlassTable
The option to create a Short ID for a notable event is located where?
- A . The Additional Fields.
- B . The Event Details.
- C . The Contributing Events.
- D . The Description.
B
Explanation:
https://docs.splunk.com/Documentation/ES/6.4.1/User/Takeactiononanotableevent
Which argument to the | tstats command restricts the search to summarized data only?
- A . summaries=t
- B . summaries=all
- C . summariesonly=t
- D . summariesonly=all
C
Explanation:
Reference: https://docs.splunk.com/Documentation/Splunk/8.0.2/Knowledge/Acceleratedatamodels
Which of the following steps will make the Threat Activity dashboard the default landing page in ES?
- A . From the Edit Navigation page, drag and drop the Threat Activity view to the top of the page.
- B . From the Preferences menu for the user, select Enterprise Security as the default application.
- C . From the Edit Navigation page, click the ‘Set this as the default view" checkmark for Threat Activity.
- D . Edit the Threat Activity view settings and checkmark the Default View option.
Where should an ES search head be installed?
- A . On a Splunk server with top level visibility.
- B . On any Splunk server.
- C . On a server with a new install of Splunk.
- D . On a Splunk server running Splunk DB Connect.
B
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.4.1/Admin/Export
Which of the following is an adaptive action that is configured by default for ES?
- A . Create notable event
- B . Create new correlation search
- C . Create investigation
- D . Create new asset
How is it possible to navigate to the ES graphical Navigation Bar editor?
- A . Configure -> Navigation Menu
- B . Configure -> General -> Navigation
- C . Settings -> User Interface -> Navigation -> Click on “Enterprise Security”
- D . Settings -> User Interface -> Navigation Menus -> Click on “default” next to SplunkEnterpriseSecuritySuite
B
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.1.0/Admin/Customizemenubar#Restore_the_default_navigation
Which setting is used in indexes.conf to specify alternate locations for accelerated storage?
- A . thawedPath
- B . tstatsHomePath
- C . summaryHomePath
- D . warmToColdScript
B
Explanation:
Reference: https://docs.splunk.com/Documentation/Splunk/8.0.2/Knowledge/Acceleratedatamodels
A customer site is experiencing poor performance. The UI response time is high and searches take a very long time to run. Some operations time out and there are errors in the scheduler logs, indicating too many concurrent searches are being started. 6 total correlation searches are scheduled and they have already been tuned to weed out false positives.
Which of the following options is most likely to help performance?
- A . Change the search heads to do local indexing of summary searches.
- B . Add heavy forwarders between the universal forwarders and indexers so inputs can be parsed before indexing.
- C . Increase memory and CPUs on the search head(s) and add additional indexers.
- D . If indexed realtime search is enabled, disable it for the notable index.
To which of the following should the ES application be uploaded?
- A . The indexer.
- B . The KV Store.
- C . The search head.
- D . The dedicated forwarder.
C
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.1.0/Install/InstallEnterpriseSecuritySHC
Which of these Is a benefit of data normalization?
- A . Reports run faster because normalized data models can be optimized for better performance.
- B . Dashboards take longer to build.
- C . Searches can be built no matter the specific source technology for a normalized data type.
- D . Forwarder-based inputs are more efficient.
If a username does not match the ‘identity’ column in the identities list, which column is checked next?
- A . Email.
- B . Nickname
- C . IP address.
- D . Combination of Last Name, First Name.
How is notable event urgency calculated?
- A . Asset priority and threat weight.
- B . Alert severity found by the correlation search.
- C . Asset or identity risk and severity found by the correlation search.
- D . Severity set by the correlation search and priority assigned to the associated asset or identity.
D
Explanation:
Reference: https://docs.splunk.com/Documentation/ES/6.1.0/User/Howurgencyisassigned