Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
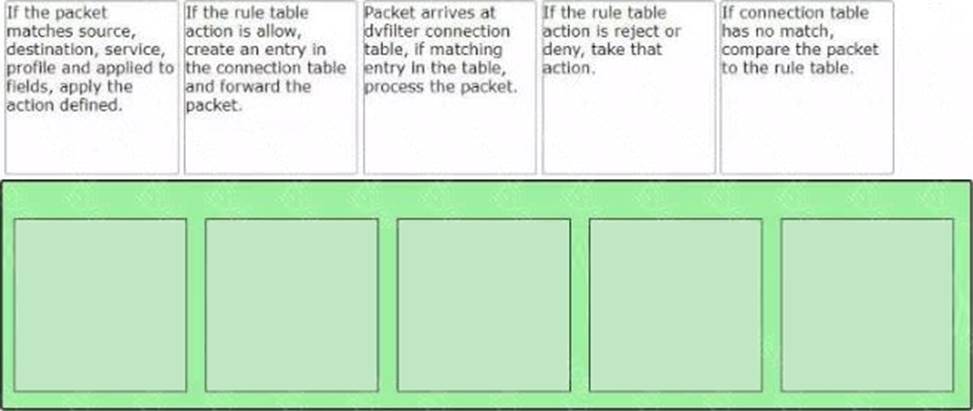
Answer: The correct order of the rule processing steps of the Distributed Firewall is as follows:
– Packet arrives at vfilter connection table. If matching entry in the table, process the packet.
– If connection table has no match, compare the packet to the rule table.
– If the packet matches source, destination, service, profile and applied to fields, apply the action defined.
– If the rule table action is allow, create an entry in the connection table and forward the packet.
– If the rule table action is reject or deny, take that action.
This order is based on the description of how the Distributed Firewall works in the web search results1. The first step is to check if there is an existing connection entry for the packet in the vfilter connection table, which is a cache of flow entries for rules with an allow action. If there is a match, the packet is processed according to the connection entry. If there is no match, the packet is compared to the rule table, which contains all the security policy rules. The rules are evaluated from top to bottom until a match is found. The match criteria include source, destination, service, profile and applied to fields. The action defined by the matching rule is applied to the packet. The action can be allow, reject or deny. If the action is allow, a new connection entry is created for the packet and the packet is forwarded to its destination. If the action is reject or deny, the packet is dropped and an ICMP message or a TCP reset message is sent back to the source.
Latest 2V0-41.23 Dumps Valid Version with 70 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

