ServiceNow CIS-SIR Certified Implementation Specialist – Security Incident Response Exam Online Training
ServiceNow CIS-SIR Online Training
The questions for CIS-SIR were last updated at Feb 18,2025.
- Exam Code: CIS-SIR
- Exam Name: Certified Implementation Specialist - Security Incident Response Exam
- Certification Provider: ServiceNow
- Latest update: Feb 18,2025
Using the KB articles for Playbooks tasks also gives you which of these advantages?
- A . Automated activities to run scans and enrich Security Incidents with real time data
- B . Automated activities to resolve security Incidents through patching
- C . Improved visibility to threats and vulnerabilities
- D . Enhanced ability to create and present concise, descriptive tasks
What specific role is required in order to use the REST API Explorer?
- A . admin
- B . sn_si.admin
- C . rest_api_explorer
- D . security_admin
The EmailUserReportedPhishing script include processes inbound emails and creates a record in which table?
- A . ar_sn_si_phishing_email
- B . sn_si_incident
- C . sn_si_phishing_email_header
- D . sn_si_phishing_email
What field is used to distinguish Security events from other IT events?
- A . Type
- B . Source
- C . Classification
- D . Description
What plugin must be activated to see the New Security Analyst UI?
- A . Security Analyst UI Plugin
- B . Security Incident Response UI plugin
- C . Security Operations UI plugin
- D . Security Agent UI Plugin
Which Table would be commonly used for Security Incident Response?
- A . sysapproval_approver
- B . sec_ops_incident
- C . cmdb_rel_ci
- D . sn_si_incident
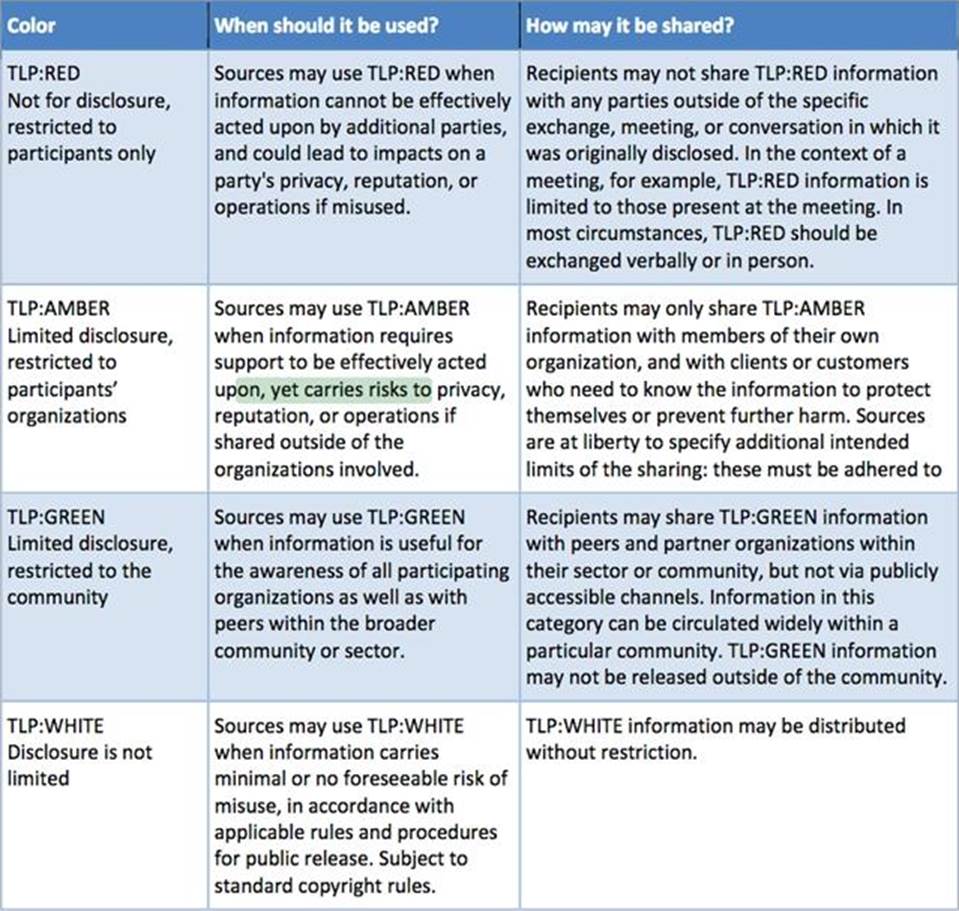
Security tag used when a piece of information requires support to be effectively acted upon, yet carries risks to privacy, reputation, or operations if shared outside of the organizations involved.
- A . TLP: GREEN
- B . TLP: AMBER
- C . TLP: RED
- D . TLP: WHITE
Knowledge articles that describe steps an analyst needs to follow to complete Security incident tasks might be associated to those tasks through which of the following?
- A . Work Instruction Playbook
- B . Flow
- C . Workflow
- D . Runbook
- E . Flow Designer
The benefits of improved Security Incident Response are expressed.
- A . as desirable outcomes with clear, measurable Key Performance Indicators
- B . differently depending upon 3 stages: Process Improvement, Process Design, and Post Go-Live
- C . as a series of states with consistent, clear metrics
- D . as a value on a scale of 1-10 based on specific outcomes
When the Security Phishing Email record is created what types of observables are stored in the record? (Choose three.)
- A . URLs, domains, or IP addresses appearing in the body
- B . Who reported the phishing attempt
- C . State of the phishing email
- D . IP addresses from the header
- E . Hashes and/or file names found in the EML attachment
- F . Type of Ingestion Rule used to identify this email as a phishing attempt
Latest CIS-SIR Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund