Review the current identity model and scenario below.
Scenario
John Doe requests "Sales" access on Salesforce for himself. In the approval process, John Doe’s manager approves. The access request is tils the expected provisioning action sent to the source connectors?
Solution: Expected Provisioning No provisioning is sent out.
- A . Yes
- B . No
B
Explanation:
In SailPoint IdentityNow, provisioning is the process of granting or revoking access to systems and applications based on access requests or changes in user identity attributes. The scenario describes John Doe requesting access to the "Sales" profile in Salesforce, which is approved by his manager.
However, simply approving an access request does not automatically trigger provisioning unless specific conditions are met:
Provisioning Policy: For the access to be provisioned, SailPoint IdentityNow requires a provisioning policy that defines the action to be taken after the approval process. This policy is often configured to specify whether access should be granted or denied after approval. If no provisioning policy is linked to the requested access, no action will be triggered.
Source Configuration: The Salesforce source (connector) in SailPoint IdentityNow must also be properly configured to handle provisioning tasks. Without proper configuration of the Salesforce source, no provisioning action will be sent even if the request is approved.
Manual Provisioning Workflow: In some cases, IdentityNow might be configured to require manual intervention after approval (e.g., triggering a manual provisioning workflow or an additional step) to enforce the provisioning action. If this configuration is missing, the approved request will not lead to automatic provisioning.
Since the scenario does not explicitly state that a provisioning policy or source configuration exists to handle the access request, the correct conclusion is that no provisioning would be sent out.
Key Reference from SailPoint Documentation:
Provisioning Concepts in IdentityNow: Documentation emphasizes that provisioning is triggered by defined workflows and provisioning policies that link the request to the connector source. Without these, the approval does not lead to actual provisioning.
Is this statement true?
Solution: IdentifyNow allow HTML editing of an email template.
- A . Yes
- B . No
A
Explanation:
SailPoint IdentityNow allows HTML editing of email templates to customize the look, feel, and content of notifications. Administrators can modify email templates using HTML to include company branding, custom messages, and specific formatting based on their organization’s communication needs.
SailPoint provides out-of-the-box email templates for common scenarios such as access requests, password resets, or provisioning notifications. Administrators can enhance these templates using HTML and inline CSS to personalize the messages for their users.
Key Reference from SailPoint Documentation:
Email Template Customization in IdentityNow: SailPoint supports the editing of email templates via HTML to meet specific organizational requirements. Administrators can navigate to the email templates section within the admin interface and update the HTML content as needed.
Is this statement true?
Solution: All emails generated from a tenant go to the intended recipient by default.
- A . Yes
- B . No
B
Explanation:
By default, not all emails generated from a SailPoint IdentityNow tenant are sent directly to the intended recipient. SailPoint IdentityNow provides an email testing mode (sandbox mode) where emails generated from the platform, such as access request notifications or password reset messages, can be routed to a specified test recipient instead of the actual intended users. This feature is commonly used during implementation or testing phases to verify email content and delivery without impacting real users.
Once the system is out of the testing phase and the email routing rules are removed, emails will be sent directly to their intended recipients. This ensures that email communications during testing do not reach end users prematurely.
Key Reference from SailPoint Documentation:
Testing Mode for Email Routing in IdentityNow: IdentityNow allows administrators to configure an email routing setting where all emails can be sent to a test inbox to ensure that email communications are functioning properly before going live to end users.
Is this statement true about using the IdentityNow APIs?
Solution: API documentation is located at https://docs.sailpoint.com
- A . Yes
- B . No
A
Explanation:
SailPoint IdentityNow API documentation is indeed located at https://docs.sailpoint.com. This official documentation site contains all the information developers need to interact with IdentityNow through APIs. It includes guidelines on how to authenticate, make requests, and use the API endpoints to automate and integrate with other systems.
Key Reference from SailPoint Documentation:
SailPoint API Documentation: The site docs.sailpoint.com hosts the official API documentation for SailPoint IdentityNow, covering all aspects of using IdentityNow’s APIs.
Is this statement true about using the IdentityNow APIs?
Solution: The APIs can be used by additional clients like cURL or Postman.
- A . Yes
- B . No
A
Explanation:
Yes, SailPoint IdentityNow APIs can be accessed and utilized by external clients such as cURL or Postman. These tools are commonly used for testing and interacting with RESTful APIs, and they work seamlessly with IdentityNow’s API framework. For example, developers can use Postman or cURL to make API calls for various actions like managing identities, querying data, and triggering provisioning events.
Key Reference from SailPoint Documentation:
API Integration with Tools: SailPoint IdentityNow supports third-party tools like cURL and Postman for API interaction, as these clients can handle HTTP requests, which is how IdentityNow’s APIs communicate.
Is this statement true about using the IdentityNow APIs? Solution: The APIs are authenticated using a client-certificate.
- A . Yes
- B . No
B
Explanation:
SailPoint IdentityNow APIs are not authenticated using client certificates. Instead, they use OAuth 2.0 for secure authentication and authorization. API consumers are required to obtain an access token, which is used to authenticate requests made to the IdentityNow API. The token is typically obtained by sending client credentials (client ID and client secret) to the IdentityNow authorization server, which grants the token for API access.
Key Reference from SailPoint Documentation:
API Authentication: SailPoint IdentityNow uses OAuth 2.0 for API authentication rather than client certificates. Detailed steps on how to implement OAuth-based authentication are available in SailPoint’s API documentation.
Is this statement true about using the IdentityNow APIs? Solution: IdentityNow’s versioned APIs are fully supported.
- A . Yes
- B . No
A
Explanation:
Yes, SailPoint IdentityNow’s versioned APIs are fully supported. SailPoint uses versioning in their APIs to ensure backward compatibility, allowing clients to continue using older API versions while newer versions are introduced with additional features and improvements. Versioning helps maintain stability for applications that depend on the APIs.
Key Reference from SailPoint Documentation:
API Versioning: SailPoint IdentityNow provides support for versioned APIs, allowing developers to choose specific versions of the API, which are fully maintained and supported, to prevent breaking
changes in integrations.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Turn off the virtual appliance’s (VA) internal firewall.
- A . Yes
- B . No
B
Explanation:
Turning off the Virtual Appliance’s (VA) internal firewall is not recommended as a standard troubleshooting step in SailPoint IdentityNow. The VA’s firewall is crucial for maintaining the security of the environment, and disabling it can expose the system to unnecessary risks. Instead, an IdentityNow engineer should verify the VA’s network configuration and ensure that the required ports are open for communication between the VA and the source.
Key Reference from SailPoint Documentation:
VA Configuration and Network Troubleshooting: Troubleshooting connection issues typically involves checking network connectivity and firewall rules, not turning off the internal firewall.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Clear the Authentication checkbox for the source in identityNow.
- A . Yes
- B . No
B
Explanation:
Clearing the authentication checkbox for a source in SailPoint IdentityNow is not a typical troubleshooting step for a timeout error. This option is related to whether or not authentication is required for the source connection. A timeout error typically points to a network issue (e.g., port, firewall, or network latency), not authentication problems. The engineer should instead focus on network-related configurations such as checking port access or firewall settings.
Key Reference from SailPoint Documentation:
Source Connectivity Troubleshooting: Timeout errors are generally caused by network issues rather than authentication problems, so adjusting authentication settings is not recommended for resolving such errors.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Check that port values configured on the identityNow source are connected for the source.
- A . Yes
- B . No
A
Explanation:
Yes, checking that the port values configured on the source in SailPoint IdentityNow are correct and accessible is an essential troubleshooting step. A timeout error can occur if the virtual appliance (VA) cannot reach the source due to incorrect port configuration or network issues blocking communication. Verifying the correct port numbers and ensuring that the necessary ports are open on both the VA and the source’s firewall is critical.
Key Reference from SailPoint Documentation:
Port Configuration for Source Connectivity: Ensuring that the proper port values are configured and accessible is one of the primary troubleshooting steps when facing timeout errors in IdentityNow.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Test connectivity from the virtual appliance (VA) to the source.
- A . Yes
- B . No
A
Explanation:
Testing connectivity from the virtual appliance (VA) to the source is a crucial troubleshooting step when dealing with connection issues such as timeouts. This can be done by accessing the VA and performing network tests (e.g., ping, telnet, or curl commands) to verify that the VA can communicate with the source over the required network paths. Ensuring that the VA has network access to the source can help identify if the problem is related to network configuration or firewall restrictions.
Key Reference from SailPoint Documentation:
VA to Source Connectivity Testing: Verifying network connectivity between the VA and the source is a fundamental step in diagnosing connection issues, as outlined in SailPoint’s troubleshooting guidelines.
Is this statement true about the purpose of a tenant?
Solution: A non-production tenant is for demonstrating functionality.
- A . Yes
- B . No
A
Explanation:
A non-production tenant is commonly used for demonstrating functionality, as well as for testing and development purposes. In a SailPoint IdentityNow environment, non-production tenants provide a sandbox environment where customers and engineers can safely explore the system, simulate use cases, and demonstrate functionality without impacting the live production environment.
Key Reference from SailPoint Documentation:
Non-Production Tenant Usage: SailPoint recommends non-production tenants for testing, demonstrating functionality, and conducting proofs of concept, ensuring that the production environment remains unaffected.
Is this statement true about the purpose of a tenant?
Solution: All customers are allowed a maximum of one non-production tenant.
- A . Yes
- B . No
B
Explanation:
Not all customers are restricted to a maximum of one non-production tenant. The number of non-production tenants that a customer can have depends on their specific licensing agreement with SailPoint. Some customers may be allowed multiple non-production tenants for various purposes like testing, development, and staging.
Key Reference from SailPoint Documentation:
Tenant Provisioning Guidelines: SailPoint provides flexibility in the number of non-production tenants based on customer agreements, allowing for multiple environments when needed.
Is this statement true about the purpose of a tenant?
Solution: A non-production tenant is used for testing new features.
- A . Yes
- B . No
A
Explanation:
Yes, a non-production tenant is typically used for testing new features before they are deployed to the production environment. This allows administrators to validate functionality, identify potential issues, and ensure the features work as expected without affecting the live users and operations.
Key Reference from SailPoint Documentation:
Testing New Features in Non-Production: SailPoint advises using non-production environments for testing new functionalities to safeguard production environments from untested changes.
Is this statement true about the purpose of a tenant?
Solution: The default non-production tenant has full performance scalability.
- A . Yes
- B . No
B
Explanation:
The default non-production tenant does not have the same full performance scalability as a production tenant. Non-production environments are typically configured with reduced resources since they are intended for testing, development, or demonstration rather than handling large-scale, live workloads.
Key Reference from SailPoint Documentation:
Performance Differences Between Tenants: SailPoint non-production tenants are generally scaled down compared to production environments to reflect their testing and demonstration purposes, not for high-performance or large-scale operations.
Is this statement true about the purpose of a tenant?
Solution: Live access reviews should be performed in a production environment.
- A . Yes
- B . No
A
Explanation:
Live access reviews, which involve reviewing and certifying user access to various resources, should be performed in a production environment. This is because access reviews are directly related to active identities and entitlements in a live system, ensuring compliance and security in real-time operations.
Key Reference from SailPoint Documentation:
Access Reviews in Production: SailPoint recommends conducting live access reviews in production environments to ensure that the access being reviewed reflects the actual, current access of users in the system.
Is this an example of a vanity URL?
Solution: https://my.example.com
- A . Yes
- B . No
A
Explanation:
Yes, https://my.example.com is an example of a vanity URL. Vanity URLs are customized, branded URLs designed to be easily recognizable, memorable, and aligned with a company’s branding. In this case, the subdomain my and the domain example.com create a branded, user-friendly URL. Vanity URLs are often used for simplifying access to services like IdentityNow and for improving user experience.
Key Reference from SailPoint Documentation:
Vanity URL Usage in IdentityNow: SailPoint allows customers to configure vanity URLs to provide a more personalized and branded login experience for their users.
Is this an example of a vanity URL?
Solution: https://identityNowacme.com
- A . Yes
- B . No
B
Explanation:
https://identityNowacme.com is not typically considered a vanity URL. While it includes the "identityNow" term, it does not appear to follow the format of a vanity URL, which generally includes a company-specific subdomain (like my) and a custom domain (example.com). In this case, the URL is more generic and lacks the branding or simplicity typically associated with vanity URLs.
Key Reference from SailPoint Documentation:
Vanity URL Structure in IdentityNow: Vanity URLs typically feature a customized subdomain that reflects the organization’s branding, and identityNowacme.com does not fit this pattern.
An IdentityNow engineer needs to review logs to diagnose when the secure tunnel fails to allow communication. Could reviewing thi9 log file help diagnose the issue?
Solution: /home/sailpoint/log/relay.log
- A . Yes
- B . No
A
Explanation:
Yes, reviewing the /home/sailpoint/log/relay.log file can help diagnose issues related to the secure tunnel in SailPoint IdentityNow. The relay.log file captures information about the communication between the IdentityNow Virtual Appliance (VA) and the SailPoint cloud. This secure tunnel is responsible for ensuring encrypted communication, and any issues with establishing or maintaining the connection can often be found in this log.
Key Reference from SailPoint Documentation:
Relay Log for Troubleshooting: The relay.log is the primary log file to review for communication issues between the Virtual Appliance and SailPoint IdentityNow cloud, including secure tunnel failures.
An IdentityNow engineer needs to review logs to diagnose when the secure tunnel fails to allow communication. Could reviewing thi9 log file help diagnose the issue?
Solution: /home/sailpoint/log/vs_agent.log
- A . Yes
- B . No
B
Explanation:
No, the vs_agent.log file is not typically used to diagnose secure tunnel communication issues. The vs_agent.log file is related to virtual appliance services and tasks but does not provide detailed information about the secure tunnel or communication errors. For troubleshooting the secure tunnel, the relay.log file is more appropriate.
Key Reference from SailPoint Documentation:
Log File Purposes: The vs_agent.log does not capture information about secure tunnel communication issues. Instead, the relay.log is the correct log file for such issues.
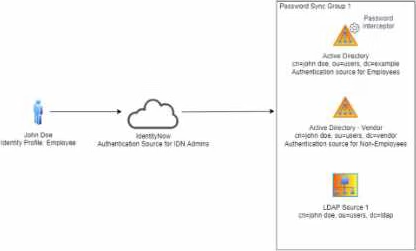
Is this statement correct about identityNow components?
Solution: Password interception is available for the Active Directory source.
- A . Yes
- B . No
A
Explanation:
Yes, password interception is available for the Active Directory (AD) source in SailPoint IdentityNow. Password interception allows IdentityNow to capture password changes made on the AD source so that it can synchronize the new passwords across other connected systems and applications. This feature ensures password consistency and compliance across the organization’s identity infrastructure.
Key Reference from SailPoint Documentation:
Password Interceptor for AD: SailPoint supports password interception for Active Directory, enabling the platform to capture and synchronize password changes from AD to other systems in real time.
When an engineer goes to Global > System Settings and clicks on System Notifications, the following page opens:
What email notifications are enabled if the engineer selects Sources?
Solution: A notification is immediately sent after successful
- A . Yes
- B . No
B
Explanation:
In SailPoint IdentityNow, email notifications related to source events (such as successful connections or other operational states) are not automatically sent immediately after a successful source connection. The system focuses on error conditions or alerts based on source status changes or failures. While successful source operations may be logged, notifications are not configured by default to trigger upon every successful action.
Key Reference from SailPoint Documentation:
Source Event Notifications: SailPoint’s notifications for source-related events primarily focus on error handling rather than successful operations, which are generally logged for reference but do not trigger immediate notifications.
When an engineer goes to Global > System Settings and clicks on System Notifications, the following page opens:
What email notifications are enabled if the engineer selects Sources?
Solution: A notification is sent when a source has been in an error state for fifteen minutes.
- A . Yes
- B . No
A
Explanation:
Yes, SailPoint IdentityNow sends a notification if a source has been in an error state for a sustained period, typically after fifteen minutes. This type of alert helps administrators to be aware of prolonged connection or operational issues with a source, so they can take corrective action promptly. The notification system is designed to escalate issues that may impact synchronization, provisioning, or access-related processes.
Key Reference from SailPoint Documentation:
Error State Notifications: SailPoint IdentityNow sends alerts for sources in error states, including when the error persists for a predefined period such as 15 minutes, helping administrators to respond to ongoing issues.
Exhibit.
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect.
Where would the virtual appliances (VAs) reside In this scenario?
Solution: B
- A . Yes
- B . No
B
Explanation:
In this scenario, the Virtual Appliances (VAs) should not reside in the DMZ (B), which is typically used for hosting services that need to be exposed to both internal and external networks, like web servers or email gateways. However, VAs require more direct and secure access to internal resources like Active Directory and databases. The VA needs to reside where it has secure and reliable connectivity to internal resources like Active Directory and database servers, which would be in the internal network.
Key Reference from SailPoint Documentation:
VA Placement Guidance: Virtual Appliances are placed within the internal network, where they can securely connect to Active Directory, databases, and other internal applications for synchronization and provisioning tasks.
Exhibit.
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect.
Where would the virtual appliances (VAs) reside In this scenario?
Solution: C
- A . Yes
- B . No
A
Explanation:
Yes, the Virtual Appliances (VAs) should reside in C, which represents the on-premise network. In this scenario, the engineer has an Active Directory, a database server, and cloud applications. The VA needs to reside inside the internal on-premises network (C) to securely communicate with the Active Directory and database server. The VA will manage the secure connection to these internal resources and can also interact with cloud applications via SailPoint IdentityNow.
Key Reference from SailPoint Documentation:
VA Deployment in On-Prem Network: SailPoint advises deploying Virtual Appliances within the internal on-premises network where they can securely access identity sources like Active Directory and internal databases.
Exhibit.
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect.
Where would the virtual appliances (VAs) reside In this scenario?
Solution: A
- A . Yes
- B . No
B
Explanation:
No, the Virtual Appliances (VAs) should not reside in A, which represents the SailPoint cloud environment. VAs are typically deployed in the on-premises network to interface directly with internal resources like Active Directory, databases, and applications. The cloud environment is where IdentityNow services are hosted, but the VAs need to be positioned closer to on-premise resources to manage identity synchronization and provisioning tasks.
Key Reference from SailPoint Documentation:
VA Placement Recommendations: Virtual Appliances are deployed in the on-premise network rather than the cloud, to ensure they have direct and secure access to internal resources.
Review the following transform:
Can the following output of this transform be expected, based on the input provided in the option?
Solution:
- A . Yes
- B . No
A
Explanation:
The provided transform is of type "Concat", which means it concatenates values from multiple sources. In this case, it appears to be concatenating the "cn" value with the "displayName" attribute of an identity. The "type": "IdentityAttribute" section specifies that the transform is pulling the "displayName" attribute from the identity object.
Given the input where the displayName is "Thomas Miller", the expected output is in the format cn=Thomas Miller,ou=users,dc=example, which aligns with the displayed output in the example. The transformation concatenates the displayName value with the rest of the distinguished name (DN), which is a common use case for generating a DN from user attributes.
Key Reference from SailPoint Documentation:
Concat Transform in IdentityNow: The concat transform is used to join multiple attribute values, and in this example, it successfully creates the expected DN string using the provided displayName input.
An IdentityNow engineer has the following problem:
IdentityNow shows status failed on a virtual appliance (VA).
Is this one of the steps that should be taken troubleshoot the issue?
Solution: Log in to the console of the VA and verify that the VA has connectivity to the internet.
- A . Yes
- B . No
A
Explanation:
Yes, verifying that the Virtual Appliance (VA) has connectivity to the internet is a critical step when
troubleshooting a "failed" status in IdentityNow. The VA requires internet connectivity to communicate with SailPoint IdentityNow’s cloud services for synchronization, updates, and other key functions. If the VA is unable to reach the internet, it can lead to a failed status. Logging in to the VA’s console to test network connectivity (e.g., using ping or curl commands) is an important step in diagnosing the issue.
Key Reference from SailPoint Documentation:
VA Internet Connectivity Troubleshooting: SailPoint recommends checking the network connectivity as one of the first steps when the VA shows a failed status.
An IdentityNow engineer has the following problem:
IdentityNow shows status failed on a virtual appliance (VA).
Is this one of the steps that should be taken troubleshoot the issue?
Solution: Review the log files in /home/sailpoint/log for errors.
- A . Yes
- B . No
A
Explanation:
Yes, reviewing the log files in the /home/sailpoint/log directory is a standard troubleshooting step for diagnosing a failed VA. The log files, such as relay.log, vs_agent.log, and others, can provide detailed error messages and insights into what might be causing the VA failure, such as connectivity issues, service failures, or configuration problems.
Key Reference from SailPoint Documentation:
Log Files for VA Troubleshooting: SailPoint’s best practices for troubleshooting VA issues involve reviewing log files to check for error messages or warnings that can help identify the root cause of the failure.
An IdentityNow engineer has the following problem:
IdentityNow shows status failed on a virtual appliance (VA).
Is this one of the steps that should be taken troubleshoot the issue?
Solution: Verify that the VA is configured for automatic updates by setting ‘autoupdate=true’ in the config.yaml file.
- A . Yes
- B . No
B
Explanation:
No, verifying that the VA is configured for automatic updates by setting autoupdate=true in the config.yaml file is not directly related to troubleshooting a failed status on the VA. While keeping the VA updated is important for long-term stability and functionality, the configuration for automatic updates does not resolve immediate connection or service failure issues. The troubleshooting focus should be on network connectivity, service status, and log reviews.
Key Reference from SailPoint Documentation:
VA Autoupdate Configuration: Configuring the VA for automatic updates is a best practice for maintaining up-to-date software but is not a direct troubleshooting step for addressing an immediate VA failure.
Is the following statement accurate regarding Separation of Duties (SoD)?
Solution: An SoD policy must define control matrix.
- A . Yes
- B . No
B
Explanation:
No, an SoD (Separation of Duties) policy does not require a control matrix to be defined. While a control matrix can be a useful tool for organizations to visualize and enforce SoD policies by mapping roles to potential conflicting access rights, it is not a mandatory component of an SoD policy. An SoD policy primarily focuses on preventing conflicts of interest by ensuring that no individual has access to perform conflicting tasks within a business process (e.g., approving and processing payments). The control matrix is a recommended method for managing SoD but not a requirement.
Key Reference from SailPoint Documentation:
SoD Policy Overview: SailPoint recommends structuring SoD policies to focus on preventing conflicting access but does not mandate the use of a control matrix, which is an optional best practice for visualizing these controls.
Is the following statement accurate regarding Separation of Duties (SoD)?
Solution: An SoD policy can define mitigating controls.
- A . Yes
- B . No
A
Explanation:
Yes, an SoD policy can define mitigating controls. Mitigating controls are measures put in place to reduce the risk of having conflicting duties. For example, if it’s not possible to completely segregate duties due to resource constraints or other business factors, mitigating controls such as enhanced auditing, periodic reviews, or dual approvals can be defined to manage the risk. SailPoint IdentityNow allows for the creation of SoD policies that include such mitigating controls to ensure compliance with security and governance requirements.
Key Reference from SailPoint Documentation:
Mitigating Controls in SoD Policies: SailPoint supports the definition of mitigating controls within SoD policies to manage and reduce risks when full separation of duties cannot be achieved.
An IdentityNow engineer has the following problem:
An identity is listed under Identities with Errors.
Is this one of the steps that should be taken to troubleshoot the issue?
Solution: Check for missing lastname, email, or uid attributes.
- A . Yes
- B . No
A
Explanation:
Yes, checking for missing critical attributes like lastname, email, or uid is a valid step when troubleshooting an identity listed under "Identities with Errors" in SailPoint IdentityNow. These attributes are often required for proper identity processing, synchronization, and provisioning. If any of these attributes are missing or incorrectly configured, it could result in errors, preventing the identity from being fully processed by the system.
Key Reference from SailPoint Documentation:
Identity Attributes and Error Handling: SailPoint IdentityNow requires certain core identity attributes (such as lastname, email, uid) to be present and correctly populated. Missing or invalid values for these attributes can lead to errors and prevent identity synchronization or provisioning.
Does this correctly describe Manager Correlation?
Solution: Linking the manager of a given identity based on the value of an account or identify attribute
- A . Yes
- B . No
A
Explanation:
Yes, this correctly describes Manager Correlation in SailPoint IdentityNow. Manager Correlation is the process of linking the manager of a given identity based on the value of an attribute in an account or identity profile, such as an employee’s manager attribute. This allows the system to automatically identify and associate the correct manager for an identity, which can be important for tasks like access approvals and certification reviews.
Key Reference from SailPoint Documentation:
Manager Correlation Process: Manager correlation involves linking an identity to its manager based on specific attributes in the identity or account, such as the managerId or similar fields.
Does this correctly describe Manager Correlation?
Solution: an approval process by which identifies assigned as manager must periodically review and approve all access assigned to their employees.
- A . Yes
- B . No
B
Explanation:
No, this statement describes Manager Certification rather than Manager Correlation. Manager Certification refers to an approval process in which managers are required to periodically review and approve the access rights of their direct reports. This is a governance feature used to ensure that employees only have the access they need, and it helps managers validate their team’s access periodically. Manager Correlation, on the other hand, is about linking identities to their managers based on attributes.
Key Reference from SailPoint Documentation:
Manager Certification vs. Manager Correlation: While Manager Certification involves periodic review and approval of access by managers, Manager Correlation is strictly about linking identities to their respective managers based on defined attributes.
Is this statement true about deploying and configuring IdentityNow’s virtual appliance (VA)?
Solution: When using the AWS deployment option, the identityNow engineer needs to convert the VA image in order to deploy it.
- A . Yes
- B . No
B
Explanation:
No, when deploying the Virtual Appliance (VA) using the AWS deployment option, the IdentityNow engineer does not need to convert the VA image. SailPoint provides an AWS-compatible Amazon Machine Image (AMI) that can be directly used to deploy the VA in AWS without any additional conversion steps. The AMI is shared with the customer’s AWS account, allowing for a streamlined deployment process.
Key Reference from SailPoint Documentation:
VA Deployment in AWS: SailPoint provides a ready-to-use AMI for AWS deployments, and no image conversion is necessary for this deployment method.
Is this statement true about deploying and configuring IdentityNow’s virtual appliance (VA)?
Solution: When deploying the VA in Azure, the identityNow engineer will need to utilize the Azure command Cline interface (CLI) to deploy the VA image.
- A . Yes
- B . No
B
Explanation:
No, when deploying the Virtual Appliance (VA) in Azure, the IdentityNow engineer does not necessarily need to use the Azure CLI to deploy the VA image. While using the Azure CLI is one option, SailPoint provides multiple ways to deploy the VA in Azure, including using the Azure portal or ARM (Azure Resource Manager) templates. The process does not mandate using the CLI specifically.
Key Reference from SailPoint Documentation:
Azure VA Deployment Methods: SailPoint supports multiple methods for deploying the VA in Azure, including through the Azure portal or ARM templates, without requiring the CLI.
Is this statement true about deploying and configuring IdentityNow’s virtual appliance (VA)?
Solution: When using the AWS deployment option, SailPoint shares an AWS Amazon Machine image (AMI) with the customer’s AWS account on a region they select.
- A . Yes
- B . No
A
Explanation:
Yes, when using the AWS deployment option, SailPoint shares an Amazon Machine Image (AMI) with the customer’s AWS account in the selected region. This AMI contains the pre-configured Virtual Appliance (VA) image that the customer can use to deploy within their own AWS environment, simplifying the deployment process and ensuring compatibility with AWS services.
Key Reference from SailPoint Documentation:
AWS AMI for VA Deployment: SailPoint provides a dedicated AMI that is shared with customers in their chosen AWS region to facilitate the deployment of the Virtual Appliance.
An IdentityNow engineer needs to find identities with disabled AD accounts by using IdentityNow’s search features. Is this the correct search syntax to perform this task?
Solution:
- A . Yes
- B . No
B
Explanation:
The search syntax @accounts( source.name:"AD" AND disabled:false ) is not correct for finding disabled AD accounts. This query would return accounts that are not disabled because it is filtering for disabled:false. To find disabled accounts, the filter should specify disabled:true.
Key Reference from SailPoint Documentation:
Search Syntax for Disabled Accounts: To search for disabled accounts, the condition should check for disabled:true.
An IdentityNow engineer needs to find identities with disabled AD accounts by using IdentityNow’s search features.
Is this the correct search syntax to perform this task?
Solution:
- A . Yes
- B . No
A
Explanation:
Yes, the search syntax @accounts( source.name:"AD" AND state:"disabled" ) is correct for finding identities with disabled AD accounts. In this case, the query filters accounts based on the state being "disabled," which is valid and effective for identifying disabled accounts.
Key Reference from SailPoint Documentation:
Search by Account State: Using state:"disabled" is an accurate way to search for disabled accounts in SailPoint IdentityNow.
