QlikView QSSA2018 Qlik Sense System Administrator Certification Exam – June 2018 Release Online Training
QlikView QSSA2018 Online Training
The questions for QSSA2018 were last updated at Feb 02,2025.
- Exam Code: QSSA2018
- Exam Name: Qlik Sense System Administrator Certification Exam – June 2018 Release
- Certification Provider: QlikView
- Latest update: Feb 02,2025
A system administrator creates a custom property called “dept” and assigns it to users and apps. The value of the custom property are department names such as Accounting, Finance, and IT. Users with the same value for “dept” can see and edit each other’s apps. Users with different values for the property should NOT see each other’s apps.
Which security rule should the administrator use to meet this requirement?
- A . Resource: App_*, Stream_*
Conditions: user.@dept=app.@dept - B . Resource: App_*
Conditions: user.@dept=resource.id - C . Resource: App_*
Conditions: user.@dept=resource.@dept - D . Resource: App_*
Conditions: user.@dept=resource.description
A user owns an app that was previously published and wants to delete the app in the hub. The user is NOT able to delete the app.
What could be causing this issue?
- A . The app is open and is being accessed by another user
- B . Published apps can only be deleted from the QMC
- C . The user needs to be assigned the RootAdmin role
- D . The user needs to be assigned the ContentAdmin role
A security audit revealed problems with the newly installed multi-node environment. The environment was deployed using the default settings for the central and rim nodes. All possible services have been added to the rim node.
The audit was based on the current IT security policy when states:
– All traffic between servers should be encrypted
– 256-bit encryption is required
– Traffic between client and server should be encrypted and trusted
– iOS devices must be supported
– Password length must be at least eight characters and include at least one number and one special character
What should the system administrator deploy to meet these requirements?
- A . A reverse proxy in the DMZ
- B . A third-party trusted certificate
- C . A certificate with third-party VPN
- D . A web app firewall in the environment
A security audit revealed problems with the newly installed multi-node environment. The environment was deployed using the default settings for the central and rim nodes. All possible services have been added to the rim node.
The audit was based on the current IT security policy when states:
– All traffic between servers should be encrypted
– 256-bit encryption is required
– Traffic between client and server should be encrypted and trusted
– iOS devices must be supported
– Password length must be at least eight characters and include at least one number and one special character
What should the system administrator deploy to meet these requirements?
- A . A reverse proxy in the DMZ
- B . A third-party trusted certificate
- C . A certificate with third-party VPN
- D . A web app firewall in the environment
A security audit revealed problems with the newly installed multi-node environment. The environment was deployed using the default settings for the central and rim nodes. All possible services have been added to the rim node.
The audit was based on the current IT security policy when states:
– All traffic between servers should be encrypted
– 256-bit encryption is required
– Traffic between client and server should be encrypted and trusted
– iOS devices must be supported
– Password length must be at least eight characters and include at least one number and one special character
What should the system administrator deploy to meet these requirements?
- A . A reverse proxy in the DMZ
- B . A third-party trusted certificate
- C . A certificate with third-party VPN
- D . A web app firewall in the environment
A security audit revealed problems with the newly installed multi-node environment. The environment was deployed using the default settings for the central and rim nodes. All possible services have been added to the rim node.
The audit was based on the current IT security policy when states:
– All traffic between servers should be encrypted
– 256-bit encryption is required
– Traffic between client and server should be encrypted and trusted
– iOS devices must be supported
– Password length must be at least eight characters and include at least one number and one special character
What should the system administrator deploy to meet these requirements?
- A . A reverse proxy in the DMZ
- B . A third-party trusted certificate
- C . A certificate with third-party VPN
- D . A web app firewall in the environment
Sets the condition to ((node.name=“RIM A” or node.name=”RIM B”))
The rule is successfully verified. The system administrator has users log in to the hub and open apps to verify that they are opening on RIM B.
However, after multiple users open the same app, there is still NO report of activity on RIM B.
What is causing this issue?
- A . There is a rule overlapping the custom load balancing rule
- B . The filter should be ((node.name=“RIM A”) and (node.name=“RIM B”))
- C . A network connection problem is occurring and the load balancing is NOT working
- D . The RIM B Engine has NOT been added to the virtual proxy
Refer to the exhibit.
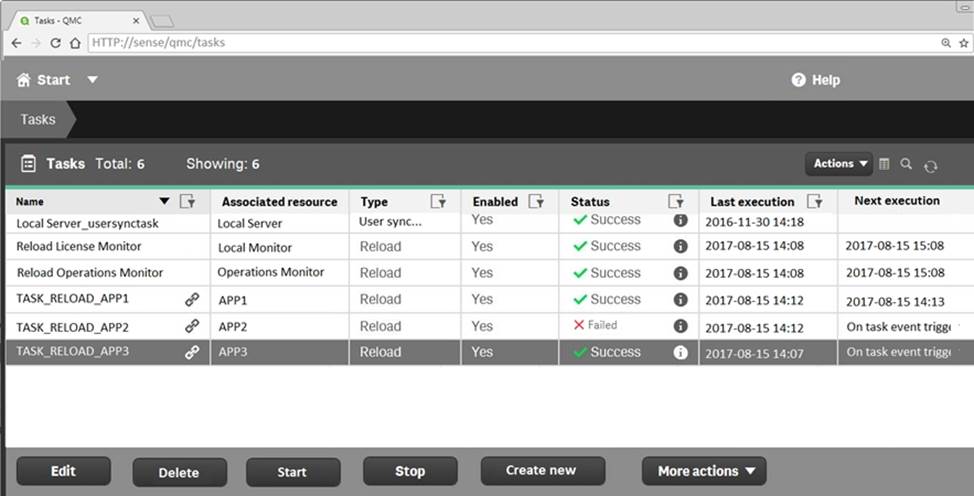
A ContentAdmin user discovers TASK_RELOAD_APP2 fails. The user double-clicks the Failed task to open the Edit reload task screen. There are NO issues found in the Edit reload task screen.
The user opens the Operations Monitor app, and finds an error message in the Task Details sheet:
Message from ReloadProvider: Reload failed in Engine. Check Engine or Scriptlogs.
The Engine log did NOT provide any reason for the failure.
Which is the most efficient method to find the cause of this issue?
- A . On the Failed task, click the information icon in the Status field, then click Download script log
- B . Navigate to C:ProgramDataQlikSenseLog, then open and review the most recent file
- C . Navigate to C:Program FilesQlikSenseLogging, then open and review the most recent file
- D . In the QMC, select Audit, select Reload Tasks under Target resource, then click Audit and review
A system administrator must design a Qlik Sense server architecture that meets the following requirements:
– Approximately 1000 users will be using apps
– Apps are reloaded outside of office hours
– The total size of data in all apps will be approximately 600 million rows
– Apps must be available 24/7
Which architecture meets these requirements in the most cost efficient way?
A)
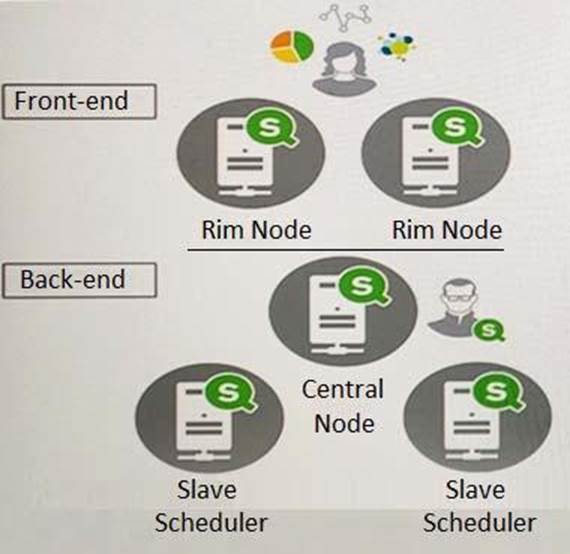
B)
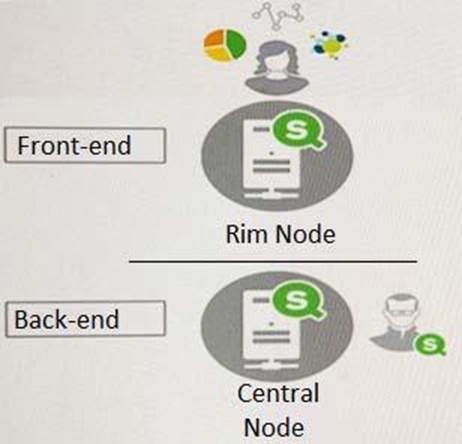
C)

D)
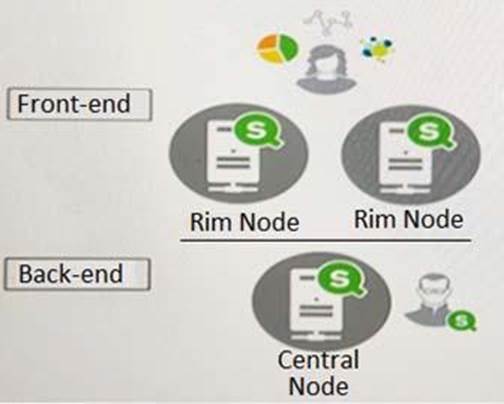
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A domain user is granted access and could successfully log into the hub yesterday.
The same domain user attempts to log in into the hub today, and receives this error message:
Your account is inactive. Contact your administrator to activate it.
The user is able to successfully log into the Windows domain network. The user did NOT change the password recently. The user has NO limited working hours in the Active Directory.
What should the system administrator investigate to determine the cause of this error message?
- A . The user properties in the QMC
- B . The Qlik Sense proxy logs
- C . The security rules which impact the user
- D . The Windows event viewer
Latest QSSA2018 Dumps Valid Version with 50 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

