Pegasystems PEGAPCLSA80V1_2020 Pega Certified Lead System Architect (PCLSA) 80V1 2020 – Architecture exam Online Training
Pegasystems PEGAPCLSA80V1_2020 Online Training
The questions for PEGAPCLSA80V1_2020 were last updated at Apr 14,2025.
- Exam Code: PEGAPCLSA80V1_2020
- Exam Name: Pega Certified Lead System Architect (PCLSA) 80V1 2020 - Architecture exam
- Certification Provider: Pegasystems
- Latest update: Apr 14,2025
Using the information shown in the following case structure, when option is always true?
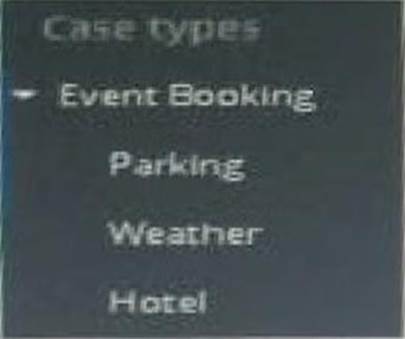
- A . The Weather case can be instantiated without a parent Event Booking case.
- B . The Parking class must inherit from the Event Booking class.
- C . Resolution of the Event Booking case requires the Parking case to be resolved.
- D . Parking, weather, and hotel cases must be Instantiated for the Event case to process correctly.
An end user of the application experienced a browser crash working on a highly available system. Crash recovery is enabled.
Does the user have to be authenticated?
- A . Yes, if the user is directed to the same node.
- B . Yes. If the authentication cookie was lost.
- C . No, if the authentication cookie was lost.
- D . No, if the user is directed to a different node.
You are designing an accessible Pega application for French and English-language users who require assistive technologies. The application must be able to run from desktop, table and mobile phone browsers.
Also, several screens require the ability to save changes and refresh the screen?
Which of the following Skin rule customization help satisfy the stated requirements?
- A . In the Skin rule, Configure the import filed for each column included in repeating layout.
- B . In the Skin rule, Configure the column Layout and specify how the sidebar appeared on tables and smart phones.
- C . In the Skin configure the style for all application filed values, paragraphs, and correspondence records.
- D . In the Skin rule, configure the Column Layout and specify the width of the sidebar on desktops.
An application contains cases which transition through different statuses through their life cycle which typically lasts 3 months.
- A . Design a reporting strategy to display the number of cases by status at the end of each month for a 12-month period.
- B . Configure a Declare index to record case data to separate table.
- C . Configure an activity to generate the data in the clipboard and report using a custom section.
- D . Configure a summary report that leverages sub reports for each month.
A developer has set the Rule security mode on the access group to deny.
Select the reason for this setting.
- A . Require Access of Role to object rules to be specified for each layer in the class hierarchy and not inherited from parent classes.
- B . Disable standard privileges providing administrator access to the application (for example AllFlows and AllFlowActions)
- C . Deny access to a rule if the privilege of the user is not defined in an access of Role to Object.
- D . Ensure that all rule with the option of specifying a privilege have a privilege. Only users with the privilege can execute the rules.
Using the information shown in the class structure, select the correct statement.
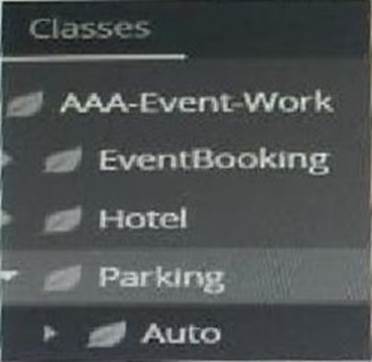
- A . Parking and Auto instances must be stored in the same table.
- B . Instance of EventBooking and Hotel can be stored In a separate table.
- C . Auto must be a subcase of Parking.
- D . EventBooking cannot be a subcase of Auto
Your team is developing a Quoting application for BigCo. The team is developing a Policy Administration application. The Quoting application is built on the Policy Administration application. The Policy Administration application requires enhancements to support other areas of the business. These enhancement take place during the same time frame as the Quoting application development.
Select the two practices for your team to follow to minimize potential development conflicts. (Choose Two.)
- A . Share rule sets between both application
- B . Switch application when modifying rules.
- C . Perform branch reviews when merging branches.
- D . Periodically rebase the policy Administrator application
Customer information is captured in an application. Corporate policy states that private information be secured and only visible to a limited users.
Which configuration do you recommend?
- A . Configure an access deny rule restricting access to the sensitive information.
- B . Use a visible when rule for the properties displaying sensitive information.
- C . Create an access control policy restricting access to the sensitive information.
- D . Move sensitive information to separate sections and apply a privilege to the sections.
XYZ Corporate wants to perform extensive analysis on work party information across various case types in real time at any time of the day. At the same time, xyz wants to minimize the impact this analysis has case worker using Pega applications.
Which solution do you recommend?
- A . Invoke BIX to export Index-WorkPartyUri data to the report database.
- B . Impalement a REST Service that persists index-WorkPartyUri data within the report database.
- C . Define additional database indexes against index-WorlParyUri.
- D . Configure the Index-WorkpartyUri Data_admin_DB_table record to write to the reports database.
CORRECT TEXT
A company wants to run the same pega application in its eastern US office as well as its india office. The eastern united states server runs in the eastern united states time zone. The india server runs in the india time zon. The company wants a process to run in both offices at the same time world-wide once a day regardless of the server’s location.
How do you efficiently meet this requirement?
- A . Define two advanced agents that call the same activity. one agent is scheduled to run at a time in the eastern united states time zone and the other agents is scheduled to run at a time in the india time zone. The activity checks both the local time zone and the local time. if the local time is close to the expected time the activity should run it continues otherwise it exits
- B . Define two advanced agent that call the same parameterzied activity. One agent passes eastern united states time zone to the activity, and the other agent passes india time zone. The activity checks the local time zone. if the parameter matches the local time zone, the activity continues. otherwise it exits
- C . Define a single adavanced agent that is scheduled to run in any desired time zone. in the Eastern us server modify the agaent schedule to run in the eastern united states time zone. For the india server, specify the india time zone within the agent schedule
- D . Define a single advanced agent that is scheduled to run in either the eastern united states zone or the india time zone. Ensure that the clocks with the servers in both offices are synchronized using the simple Network time protocal
Latest PEGAPCLSA80V1_2020 Dumps Valid Version with 78 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

