PECB ISO-IEC-27001 Lead Auditor PECB Certified ISO/IEC 27001 Lead Auditor exam Online Training
PECB ISO-IEC-27001 Lead Auditor Online Training
The questions for ISO-IEC-27001 Lead Auditor were last updated at Feb 21,2025.
- Exam Code: ISO-IEC-27001 Lead Auditor
- Exam Name: PECB Certified ISO/IEC 27001 Lead Auditor exam
- Certification Provider: PECB
- Latest update: Feb 21,2025
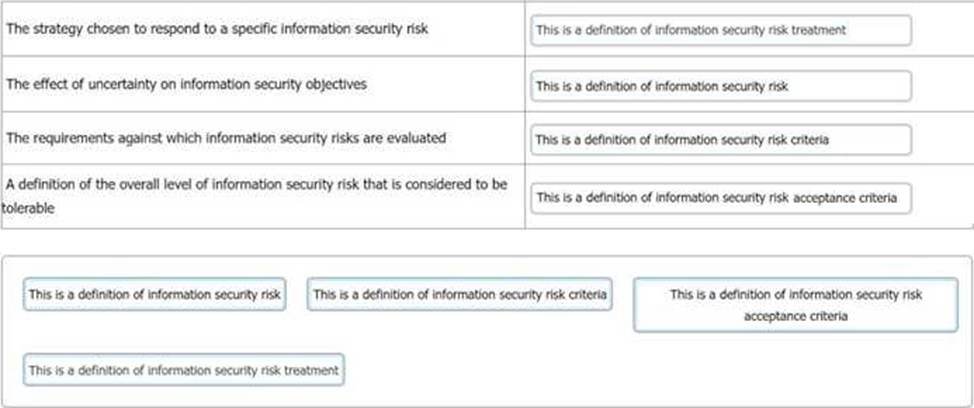
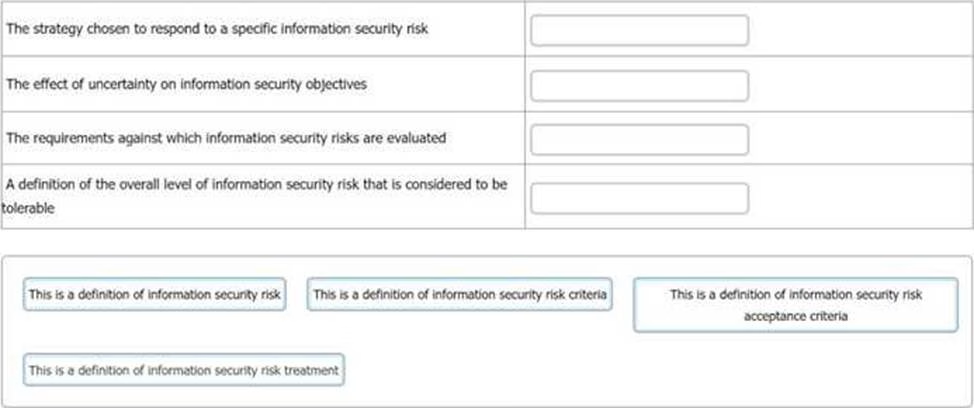
DRAG DROP
You have just completed a scheduled information security audit of your organisation when the IT Manager approaches you and asks for your assistance in the revision of the company’s risk management process.
He is attempting to update the current documentation to make it easier for other managers to understand, however, it is clear from your discussion he is confusing several key terms.
You ask him to match each of the descriptions with the appropriate risk term.
What should the correct answers be?
You ask the IT Manager why the organisation still uses the mobile app while personal data encryption and pseudonymisation tests failed. Also, whether the Service Manager is authorised to approve the test.
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymisation functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That’s why the Service Manager signed the approval. You are preparing the audit findings. Select the correct option.
- A . There is a nonconformity (NC). The organisation and developer do not perform acceptance tests. (Relevant to clause 8.1, control A.8.29)
- B . There is a nonconformity (NC). The Service Manager does not comply with the software security management procedure. (Relevant to clause 8.1, control A.8.30)
- C . There is a nonconformity (NC). The organisation and developer perform security tests that fail. (Relevant to clause 8.1, control A.8.29)
- D . There is NO nonconformity (NC). The Service Manager makes a good decision to continue the service. (Relevant to clause 8.1, control A.8.30)
You ask the IT Manager why the organisation still uses the mobile app while personal data encryption and pseudonymization tests failed. Also, whether the Service Manager is authorized to approve the test.
The IT Manager explains the test results should be approved by him according to the software security management procedure. The reason why the encryption and pseudonymization functions failed is that these functions heavily slowed down the system and service performance. An extra 150% of resources are needed to cover this. The Service Manager agreed that access control is good enough and acceptable. That’s why the Service Manager signed the approval.
You sample one of the medical staff’s mobile and found that ABC’s healthcare mobile app, version 1.01 is installed. You found that version 1.01 has no test record.
The IT Manager explains that because of frequent ransomware attacks, the outsourced mobile app development company gave a free minor update on the tested software, performed an emergency release of the updated software, and gave a verbal guarantee that there will be no impact on any security functions. Based on his 20 years of information security experience, there is no need to re-test.
You are preparing the audit findings Select two options that are correct.
- A . There is NO nonconformity (NC). The IT Manager demonstrates he is fully competent. (Relevant to clause 7.2)
- B . There is a nonconformity (NC). The IT Manager does not comply with the software security management procedure. (Relevant to clause 8.1, control A.8.30)
- C . There is a nonconformity (NC). The organisation does not control planned changes and review the consequences of unintended changes. (Relevant to clause 8.1)
- D . There is an opportunity for improvement (OI). The organisation selects an external service provider based on the extent of free services it will provide. (Relevant to clause 8.1, control A.5.21)
- E . There is NO nonconformity (NC). The IT Manager demonstrates good leadership. (Relevant to clause 5.1, control 5.4)
- F . There is an opportunity for improvement (OI). The IT Manager should make the decision to continue the service based on appropriate testing. (Relevant to clause 8.1, control A.8.30)
During a third-party certification audit, you are presented with a list of issues by an auditee.
Which four of the following constitute ‘internal’ issues in the context of a management system to ISO 27001:2022?
- A . Higher labour costs as a result of an aging population
- B . A rise in interest rates in response to high inflation
- C . Poor levels of staff competence as a result of cuts in training expenditure
- D . Poor morale as a result of staff holidays being reduced
- E . Increased absenteeism as a result of poor management
- F . A reduction in grants as a result of a change in government policy
- G . A fall in productivity linked to outdated production equipment
- H . Inability to source raw materials due to government sanctions
You are an experienced ISMS audit team leader. During the conducting of a third-party surveillance audit, you decide to test your auditee’s knowledge of ISO/IEC 27001’s risk management requirements.
You ask her a series of questions to which the answer is either ‘that is true’ or ‘that is false’.
Which four of the following should she answer ‘that is true’?
- A . The results of risk assessments must be maintained
- B . Risk identification is used to determine the severity of an information security risk
- C . ISO/IEC 27001 provides an outline approach for the management of risk
- D . The organisation must produce a risk treatment plan for every business risk identified
- E . The organisation must operate a risk treatment process to eliminate it’s information security risks
- F . The initial phase in an organisation’s risk management process should be information security risk assessment
- G . Risks assessments should be undertaken at monthly intervals
- H . Risk assessments should be undertaken following significant changes
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services. You find all nursing home residents wear an electronic wristband for monitoring their location, heartbeat, and blood pressure always. You learned that the electronic wristband automatically uploads all data to the artificial intelligence (AI) cloud server for healthcare monitoring and analysis by healthcare staff.
To verify the scope of ISMS, you interview the management system representative (MSR) who explains that the ISMS scope covers an outsourced data center.
Select three options for the audit evidence you need to find to verify the scope of the ISMS.
- A . The auditee has identified the resident’s needs and expectations on the facility and environmental safety
- B . The auditee has ISO 9001 certification
- C . The auditee has identified the governmental authorities’ needs and expectations on healthcare services and patient data handling
- D . The auditee has identified the resident’s needs and expectations on how they should protect the resident’s personal data
- E . The auditee has identified the resident’s needs and expectations on the comfort facility, medical professional’s competence, and clean environment
- F . The auditee has identified the resident’s needs and expectations on healthcare medical treatment services
- G . The IT service agreement with the data center where the artificial intelligence (AI) cloud server is located
- H . The auditee is considering the purchase of a healthcare monitoring app from an external software company
You are an experienced ISMS audit team leader providing guidance to an ISMS auditor in training. They have been asked to carry out an assessment of external providers and have prepared a checklist containing the following activities. They have asked you to review their checklist to confirm that the actions they are proposing are appropriate.
The audit they have been invited to participate in is a third-party surveillance audit of a data centre. The data centre agent is part of a wider telecommunication group. Each data centre within the group operates its own ISMS and holds its own certificate.
Select three options that relate to ISO/IEC 27001:2022’s requirements regarding external providers.
- A . I will check the other data centres are treated as external providers, even though they are part of the same telecommunication group
- B . I will ensure external providers have a documented process in place to notify the organisation of any risks arising from the use of its products or services
- C . I will ensure that the organisation has a reserve external provider for each process it has identified as critical to preservation of the confidentiality, integrity and accessibility of its information
- D . I will limit my audit activity to externally provided processes as there is no need to audit externally provided products of services
- E . I will ensure the organization is regularly monitoring, reviewing and evaluating external provider performance
- F . I will ensure the organization is has determined the need to communicate with external providers regarding the ISMS
- G . I will ensure that top management have assigned roles and responsibilities for those providing external ISMS processes as well as internal ISMS processes
- H . I will ensure that the organisation ranks its external providers and allocates the majority of its work to those providers who are rated the highest
You are an experienced ISMS audit team leader providing guidance to an ISMS auditor in training. They have been asked to carry out an assessment of external providers and have prepared a checklist containing the following activities. They have asked you to review their checklist to confirm that the actions they are proposing are appropriate.
The audit they have been invited to participate in is a third-party surveillance audit of a data centre. The data centre agent is part of a wider telecommunication group. Each data centre within the group operates its own ISMS and holds its own certificate.
Select three options that relate to ISO/IEC 27001:2022’s requirements regarding external providers.
- A . I will check the other data centres are treated as external providers, even though they are part of the same telecommunication group
- B . I will ensure external providers have a documented process in place to notify the organisation of any risks arising from the use of its products or services
- C . I will ensure that the organisation has a reserve external provider for each process it has identified as critical to preservation of the confidentiality, integrity and accessibility of its information
- D . I will limit my audit activity to externally provided processes as there is no need to audit externally provided products of services
- E . I will ensure the organization is regularly monitoring, reviewing and evaluating external provider performance
- F . I will ensure the organization is has determined the need to communicate with external providers regarding the ISMS
- G . I will ensure that top management have assigned roles and responsibilities for those providing external ISMS processes as well as internal ISMS processes
- H . I will ensure that the organisation ranks its external providers and allocates the majority of its work to those providers who are rated the highest
You are an experienced ISMS auditor conducting a third-party surveillance audit at an organisation which offers ICT reclamation services. ICT equipment which companies no longer require is processed by the organisation. It Is either recommissioned and reused or is securely destroyed. You notice two servers on a bench in the corner of the room. Both have stickers on item with the server’s name, IP address and admin password. You ask the ICT Manager about them, and he tells you they were part of a shipment received yesterday from a regular customer.
Which one action should you take?
- A . Ask the ICT Manager to record an information security incident and initiate the information security incident management process
- B . Note the audit finding and check the process for dealing with incoming shipments relating to customer IT security
- C . Record what you have seen in your audit findings, but take no further action
- D . Raise a nonconformity against control 5.31 Legal, staturary, regulatory and contractual requirements’
- E . Raise a nonconformity against control 8.20 ‘network security’ (networks and network devices shall be secured, managed and controlled to protect information in systems and applications)
- F . Ask the auditee to remove the labels, then carry on with the audit
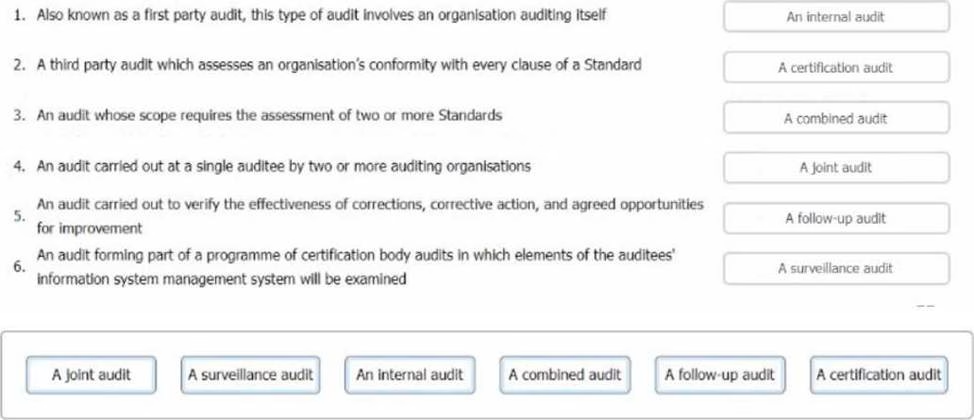
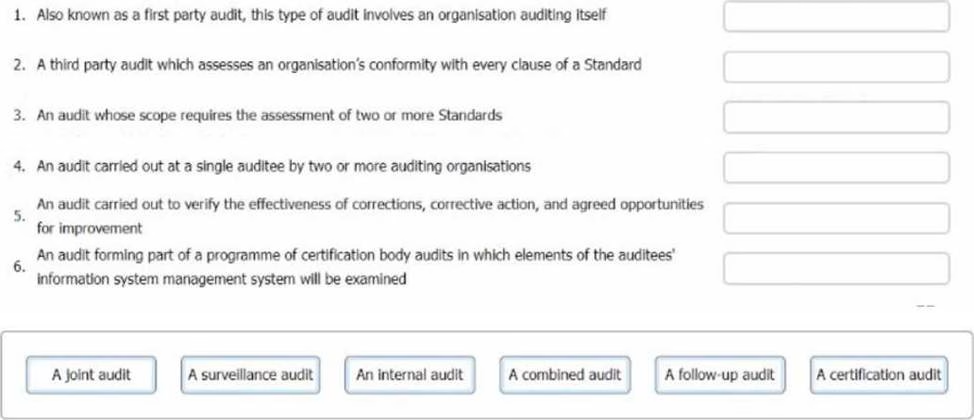
DRAG DROP
You are an experienced ISMS audit team leader. An auditor in training has approached you to ask you to clarify the different types of audits she may be required to undertake. Match the following audit types to the descriptions.
To complete the table click on the blank section you want to complete so that It is highlighted In fed, and then click on the applicable text from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.
Latest ISO-IEC-27001 Lead Auditor Dumps Valid Version with 100 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund