PECB ISO-IEC-27001 Lead Auditor PECB Certified ISO/IEC 27001 Lead Auditor exam Online Training
PECB ISO-IEC-27001 Lead Auditor Online Training
The questions for ISO-IEC-27001 Lead Auditor were last updated at Jul 09,2025.
- Exam Code: ISO-IEC-27001 Lead Auditor
- Exam Name: PECB Certified ISO/IEC 27001 Lead Auditor exam
- Certification Provider: PECB
- Latest update: Jul 09,2025
You are preparing the audit findings. Select two options that are correct.
- A . There is an opportunity for improvement (OFI). The iLiirmation security incident training effectiveness can be improved. This is relevant to clause 7.2 and control A.6.3.
- B . There is no nonconformance. The information security weaknesses, events, and incidents are reported. This conforms with clause 9.1 and control A.5.24.
- C . There is no nonconformance. The information security handling training has performed, and its effectiveness was evaluated. This conforms with clause 7.2 and control A.6.3.
- D . There is a nonconformity (NC). Based on sampling interview results, none of the interviewees were able to describe the incident management procedure reporting process including the role and responsibilities of personnel. This is not conforming with clause 9.1 and control A.5.24.
- E . There is a nonconformity (NC). The information security incident training has failed. This is not conforming with clause 7.2 and control A.6.3.
- F . There is an opportunity for improvement (OFI). The information security weaknesses, events, and madents are reported. This is relevant to clause 9.1 and control A.5.24.
You are an experienced ISMS auditor, currently providing support to an ISMS auditor in training who is carrying out her first initial certification audit. She asks you what she should be verifying when auditing an organisation’s Information Security objectives. You ask her what she has included in her audit checklist and she provides the following replies.
Which three of these responses would you cause you concern in relation to conformity with ISO/IEC 27001:2022?
- A . I am going to check how each Information Security objective has been communicated to those who need to be aware of it in order for the objective to be achieved
- B . I am going to check that top management have determined the Information Security objectives for the current year. If not, I will check that this task has been programmed to be completed
- C . I am going to check that the Information Security objectives are written down on paper so that everyone is clear on what needs to be achieved, how it will be achieved, and by when it will be achieved
- D . I am going to check that there is a process in place to periodically revisit Information Security objectives, with a view to amending or cancelling them if circumstances necessitate this
- E . I am going to check that a completion date has been set for each objective and that there are no objectives with missing ‘achieve by’ dates
- F . I am going to check that the necessary budget, manpower and materials to achieve each objective has been determined
- G . I am going to check that all the Information Security objectives are measurable. If they are not measurable the organisation will not be able to track progress against them
You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leader. You are presently in the auditee’s data centre with another member of your audit team.
Your colleague seems unsure as to the difference between an information security event and an information security incident. You attempt to explain the difference by providing examples.
Which three of the following scenarios can be defined as information security incidents?
- A . The organisation’s malware protection software prevents a virus
- B . A hard drive is used after its recommended replacement date
- C . The organisation receives a phishing email
- D . An employee fails to clear their desk at the end of their shift
- E . A contractor who has not been paid deletes top management ICT accounts
- F . An unhappy employee changes payroll records without permission
- G . The organisation fails a third-party penetration test
- H . The organisation’s marketing data is copied by hackers and sold to a competitor
You are performing an ISMS audit at a nursing home where residents always wear an electronic wristband for monitoring their location, heartbeat, and blood pressure. The wristband automatically uploads this data to a cloud server for healthcare monitoring and analysis by staff.
You now wish to verify that the information security policy and objectives have been established by top management. You are sampling the mobile device policy and identify a security objective of this policy is "to ensure the security of teleworking and use of mobile devices" The policy states the following controls will be applied in order to achieve this.
Personal mobile devices are prohibited from connecting to the nursing home network, processing, and storing residents’ data.
The company’s mobile devices within the ISMS scope shall be registered in the asset register. The company’s mobile devices shall implement or enable physical protection, i.e., pin-code protected screen lock/unlock, facial or fingerprint to unlock the device.
The company’s mobile devices shall have a regular backup.
To verify that the mobile device policy and objectives are implemented and effective, select three options for your audit trail.
- A . Interview the reception personnel to make sure all visitor and employee bags are checked before entering the nursing home
- B . Review visitors’ register book to make sure no visitor can have their personal mobile phone in the nursing home
- C . Review the internal audit report to make sure the IT department has been audited
- D . Review the asset register to make sure all personal mobile devices are registered
- E . Sampling some mobile devices from on-duty medical staff and validate the mobile device information with the asset register
- F . Review the asset register to make sure all company’s mobile devices are registered
- G . Interview the supplier of the devices to make sure they are aware of the ISMS policy
- H . Interview top management to verify their involvement in establishing the information security policy and the information security objectives
The data center at which you work is currently seeking ISO/IEC27001:2022 certification. In preparation for your initial certification visit a number of internal audits have been carried out by a colleague working at another data centre within your Group. They secured their ISO/IEC 27001:2022 certificate earlier in the year.
You have just qualified as an Internal ISMS auditor and your manager has asked you to review the audit process and audit findings as a final check before the external Certrfication Body arrives.
Which six of the following would cause you concern in respect of conformity to ISO/IEC 27001:2022 requirements?
- A . The audit programme shows management reviews taking place at irregular intervals during the year
- B . Audit reports are not held in hardcopy (i.e. on paper). They are only stored as ".POF documents on the organisation’s intranet
- C . The audit programme does not take into account the relative importance of information security processes
- D . The audit programme mandates auditors must be independent of the areas they audit in order to satisfy the requirements of ISO/IEC 27001:2022
- E . Although the scope for each internal audit has been defined, there are no audit criteria defined for the audits carried out to date
- F . Audit reports to date have used key performance indicator information to focus solely on the efficiency of ISMS processes
- G . The audit programme does not reference audit methods or audit responsibilities
- H . The audit programme does not take into account the results of previous audits
- I . Top management commitment to the ISMS will not be audited before the certification visit, according to the audit programme
- J . The audit process states the results of audits will be made available to ‘relevant’ managers, not top management
The data center at which you work is currently seeking ISO/IEC27001:2022 certification. In preparation for your initial certification visit a number of internal audits have been carried out by a colleague working at another data centre within your Group. They secured their ISO/IEC 27001:2022 certificate earlier in the year.
You have just qualified as an Internal ISMS auditor and your manager has asked you to review the audit process and audit findings as a final check before the external Certrfication Body arrives.
Which six of the following would cause you concern in respect of conformity to ISO/IEC 27001:2022 requirements?
- A . The audit programme shows management reviews taking place at irregular intervals during the year
- B . Audit reports are not held in hardcopy (i.e. on paper). They are only stored as ".POF documents on the organisation’s intranet
- C . The audit programme does not take into account the relative importance of information security processes
- D . The audit programme mandates auditors must be independent of the areas they audit in order to satisfy the requirements of ISO/IEC 27001:2022
- E . Although the scope for each internal audit has been defined, there are no audit criteria defined for the audits carried out to date
- F . Audit reports to date have used key performance indicator information to focus solely on the efficiency of ISMS processes
- G . The audit programme does not reference audit methods or audit responsibilities
- H . The audit programme does not take into account the results of previous audits
- I . Top management commitment to the ISMS will not be audited before the certification visit, according to the audit programme
- J . The audit process states the results of audits will be made available to ‘relevant’ managers, not top management
You are conducting a third-party surveillance audit when another member of the audit team approaches you seeking clarification. They have been asked to assess the organisation’s application of control 5.7 – Threat Intelligence. They are aware that this is one of the new controls introduced in the 2022 edition of ISO/IEC 27001, and they want to make sure they audit the control correctly. They have prepared a checklist to assist them with their audit and want you to confirm that their planned activities are aligned with the control’s requirements.
Which three of the following options represent valid audit trails?
- A . I will review the organisation’s threat intelligence process and will ensure that this is fully documented
- B . I will speak to top management to make sure all staff are aware of the importance of reporting threats
- C . I will ensure that the task of producing threat intelligence is assigned to the organisation s internal audit team
- D . I will check that threat intelligence is actively used to protect the confidentiality, integrity and availability of the organisation’s information assets
- E . I will ensure that the organisation’s risk assessment process begins with effective threat intelligence
- F . I will determine whether internal and external sources of information are used in the production of threat intelligence
- G . I will review how information relating to information security threats is collected and evaluated to produce threat intelligence
- H . I will ensure that appropriate measures have been introduced to inform top management as to the effectiveness of current threat intelligence arrangements
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security of the business continuity management process. During the audit, you learned that the organisation activated one of the business continuity plans (BCPs) to make sure the nursing service continued during the recent pandemic. You ask Service Manager to explain how the organisation manages information security during the business continuity management process.
The Service Manager presents the nursing service continuity plan for a pandemic and summarises the process as follows:
Stop the admission of any NEW residents.
70% of administration staff and 30% of medical staff will work from home.
Regular staff self-testing including submitting a negative test report 1 day BEFORE they come to the office.
Install ABC’s healthcare mobile app, tracking their footprint and presenting a GREEN Health Status QR-Code for checking on the spot.
You ask the Service Manager how to prevent non-relevant family members or interested parties from accessing residents’ personal data when staff work from home. The Service Manager cannot answer and suggests the n" Security Manager should help with that.
You would like to further investigate other areas to collect more audit evidence Select three options that will be in your audit trail.
- A . Collect more evidence on how the organisation manages information security on mobile devices and during teleworking (Relevant to control A.6.7)
- B . Collect more evidence by interviewing more staff about their feeling about working from home. (Relevant to clause 4.2)
- C . Collect more evidence on what resources the organisation provides to support the staff working from home. (Relevant to clause 7.1)
- D . Collect more evidence on how the organisation performs a business risk assessment to evaluate how fast the existing residents can be discharged from the nursing home. (Relevant to clause 6)
- E . Collect more evidence on how and when the Business Continuity Wan has been tested. (Relevant to control A.5.29)
- F . Collect more evidence on how the organisation makes sure only staff with a negative test result can enter the organisation (Relevant to control A.7.2)
You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leader. You are presently in the auditee’s data centre with another member of your audit team.
You are currently in a large room that is subdivided into several smaller rooms, each of which has a numeric combination lock and swipe card reader on the door. You notice two external contractors using a swipe card and combination number provided by the centre’s reception desk to gain access to a client’s suite to carry out authorised electrical repairs.
You go to reception and ask to see the door access record for the client’s suite. This indicates only one card was swiped. You ask the receptionist and they reply, "yes it’s a common problem. We ask everyone to swipe their cards but with contractors especially, one tends to swipe and the rest simply ‘tailgate’ their way in" but we know who they are from the reception sign-in.
Based on the scenario above which one of the following actions would you now take?
- A . Take no action. Irrespective of any recommendations, contractors will always act in this way
- B . Raise a nonconformity against control A.5.20 ‘addressing information security in supplier relationships’ as information security requirements have not been agreed upon with the supplier
- C . Raise a nonconformity against control A.7.6 ‘working in secure areas’ as security measures for working in secure areas have not been defined
- D . Determine whether any additional effective arrangements are in place to verify individual access to secure areas e.g. CCTV
- E . Raise an opportunity for improvement that contractors must be accompanied at all times when accessing secure facilities
- F . Raise an opportunity for improvement to have a large sign in reception reminding everyone requiring access must use their swipe card at all times
- G . Raise a nonconformity against control A.7.2 ‘physical entry’ as a secure area is not adequately protected
- H . Tell the organisation they must write to their contractors, reminding them of the need to use access cards appropriately
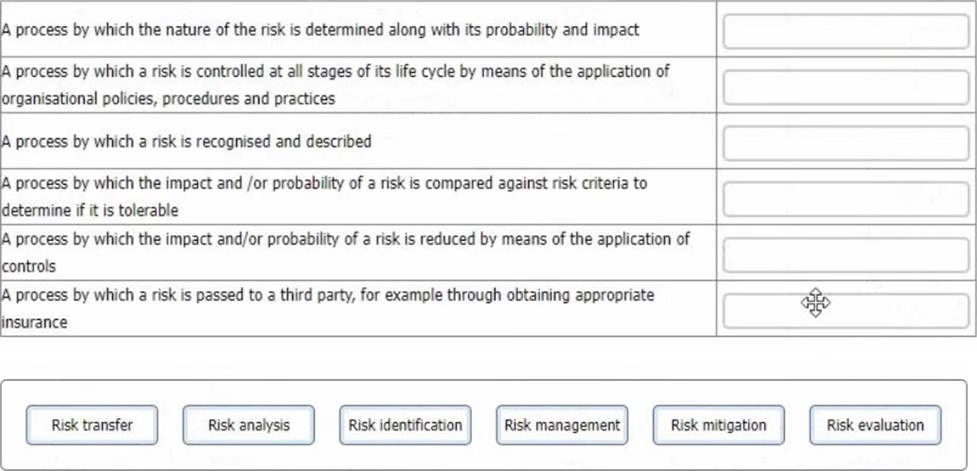
DRAG DROP
You are an experienced ISMS audit team leader providing instruction to an auditor in training. They are unclear in their understanding of risk processes and ask you to provide them with an example of each of the processes detailed below.
Match each of the descriptions provided to one of the following risk management processes.
To complete the table click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.
Latest ISO-IEC-27001 Lead Auditor Dumps Valid Version with 100 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund