PECB ISO-IEC-27001 Lead Auditor PECB Certified ISO/IEC 27001 Lead Auditor exam Online Training
PECB ISO-IEC-27001 Lead Auditor Online Training
The questions for ISO-IEC-27001 Lead Auditor were last updated at Feb 21,2025.
- Exam Code: ISO-IEC-27001 Lead Auditor
- Exam Name: PECB Certified ISO/IEC 27001 Lead Auditor exam
- Certification Provider: PECB
- Latest update: Feb 21,2025
Which three of the following options are an advantage of using a sampling plan for the audit?
- A . Overrules the auditor’s instincts
- B . Use of the plan for consecutive audits
- C . Provides a suitable understanding of the ISMS
- D . Implements the audit plan efficiently
- E . Gives confidence in the audit results
- F . Misses key issues
After completing Stage 1 and in preparation for a Stage 2 initial certification audit, the auditee informs the audit team leader that they wish to extend the audit scope to include two additional sites that have recently been acquired by the organisation.
Considering this information, what action would you expect the audit team leader to take?
- A . Increase the length of the Stage 2 audit to include the extra sites
- B . Obtain information about the additional sites to inform the certification body
- C . Arrange to complete a remote Stage 1 audit of the two sites using a video conferencing platform
- D . Inform the auditee that the request can be accepted but a full Stage 1 audit must be repeated
DRAG DROP
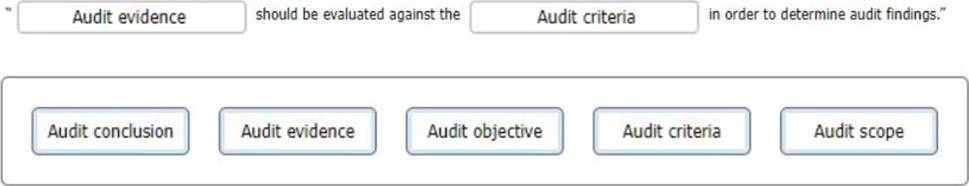
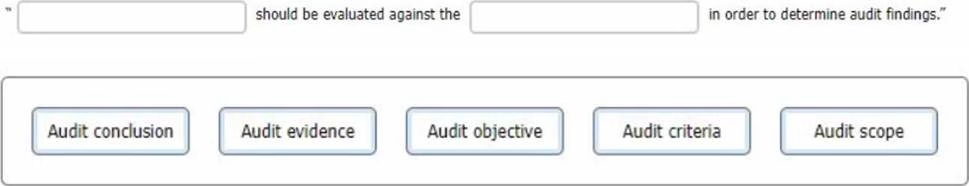
In regard to generating an audit finding, select the words that best complete the following sentence.
To complete the sentence with the best word(s), click on the blank section you want to complete so that it Is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
During discussions with the individual(s) managing the audit programme of a certification body, the Management System Representative of the client organisation asks for a specific auditor for the certification audit. Select two of the following options for how the individual(s) managing the audit programme should respond.
- A . Advise the Management System Representative that his request can be accepted
- B . Suggest that the Management System Representative chooses another certification body
- C . State that his request will be considered but may not be taken up
- D . Suggest asking the certification body management to permit the request
- E . Advise the Management System Representative that the audit team selection is a decision that the audit programme manager needs to make based on the resources available
During an opening meeting of a Stage 2 audit, the Managing Director of the client organisation invites the audit team to view a new company video lasting 45 minutes.
Which two of the following responses should the audit team leader make?
- A . Advise the Managing Director that the audit team has to keep to the planned schedule
- B . State that the audit team leader will stay behind after the opening meeting to view the video on behalf of the team
- C . Invite the Managing Director to the auditors’ hotel for a viewing that evening.
- D . Suggest that the video could be viewed during a refreshment break
- E . State that the audit team will make a decision on the viewing at a later time
- F . Advise the Managing Director that the audit team agrees to his request
DRAG DROP
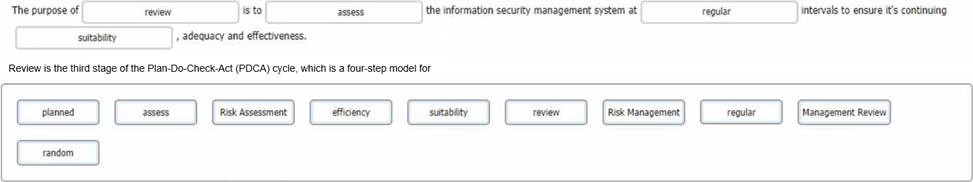
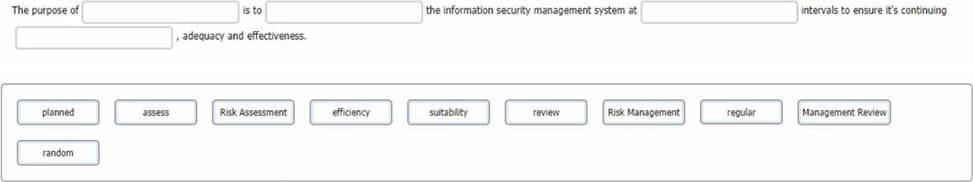
You are an experienced ISMS audit team leader, talking to an Auditor in training who has been assigned to your audit team. You want to ensure that they understand the importance of the Check stage of the Plan-Do-Check-Act cycle in respect of the operation of the information security management system.
You do this by asking him to select the words that best complete the sentence:
To complete the sentence with the best word(s), click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
You are an ISMS auditor conducting a third-party surveillance audit of a telecom’s provider. You are in the equipment staging room where network switches are pre-programmed before being despatched to clients. You note that recently there has been a significant increase in the number of switches failing their initial configuration test and being returned for reprogramming.
You ask the Chief Tester why and she says, ‘It’s a result of the recent ISMS upgrade’. Before the upgrade each technician had their own hard copy work instructions. Now, the eight members of my team have to share two laptops to access the clients’ configuration instructions online. These delays put pressure on the technicians, resulting in more mistakes being made’.
Based solely on the information above, which clause of ISO to raise a nonconformity against’ Select one.
- A . Clause 7.5 – Documented information
- B . Clause 8.1 – Operational planning and control
- C . Clause 10.2 – Nonconformity and corrective action
- D . Clause 7.3 – Awareness
- E . Clause 7.2 – Competence
- F . Clause 7.4 – Communication
During a third-party certification audit you are presented with a list of issues by an auditee.
Which four of the following constitute ‘external’ issues in the context of a management system to ISO/IEC 27001:2022?
- A . A rise in interest rates in response to high inflation
- B . A reduction in grants as a result of a change in government policy
- C . Poor levels of staff competence as a result of cuts in training expenditure
- D . Increased absenteeism as a result of poor management
- E . Higher labour costs as a result of an aging population
- F . Inability to source raw materials due to government sanctions
- G . Poor morale as a result of staff holidays being reduced
- H . A fall in productivity linked to outdated production equipment
You are performing an ISMS audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to verify the information security incident management process. The IT Security Manager presents the information security incident management procedure and explains that the process is based on ISO/IEC 27035-1:2016.
You review the document and notice a statement "any information security weakness, event, and incident should be reported to the Point of Contact (PoC) within 1 hour after identification". When interviewing staff, you found that there were differences in the understanding of the meaning of "weakness, event, and incident".
You sample incident report records from the event tracking system for the last 6 months with summarized results in the following table.
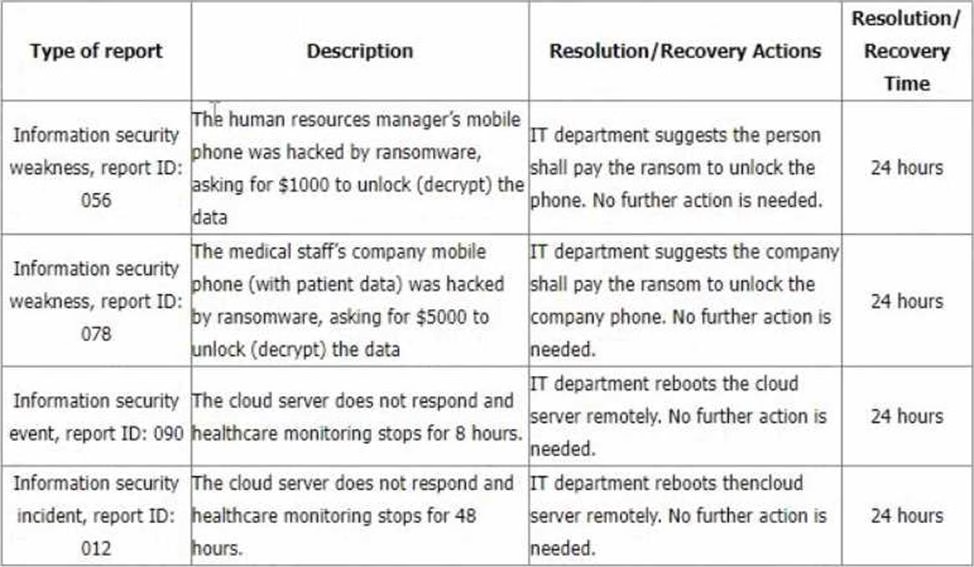
You would like to further investigate other areas to collect more audit evidence. Select two options that will not be in your audit trail.
- A . Collect more evidence on how and when the Human Resources manager pays the ransom fee to unlock personal mobile data, i.e., credit card, and bank transfer. (Relevant to control A.5.26)
- B . Collect more evidence on what the service requirements of healthcare monitoring are. (Relevant to clause 4.2)
- C . Collect more evidence on how the organization determined no further action was needed after the incident. (Relevant to control A.5.26)
- D . Collect more evidence on how the organisation determined the incident recovery time. (Relevant to control A.5.27)
- E . Collect more evidence on the incident recovery procedures. (Relevant to control A.5.26)
- F . Collect more evidence by interviewing more staff about their understanding of the reporting process. (Relevant to control A.6.8)
- G . Collect more evidence on how and when the company pays the ransom fee to unlock the company’s mobile phone and data, i.e., credit card, and bank transfer. (Relevant to control A.5.26)
You are an experienced audit team leader guiding an auditor in training,
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the TECHNOLOGICAL controls listed in the Statement of Applicability (SoA) and implemented at the site. Select four controls from the following that would you expect the auditor in training to review.
- A . The development and maintenance of an information asset inventory
- B . Rules for transferring information within the organisation and to other organisations
- C . Confidentiality and nondisclosure agreements
- D . How protection against malware is implemented
- E . Access to and from the loading bay
- F . The conducting of verification checks on personnel
- G . Remote working arrangements
- H . How information security has been addressed within supplier agreements
- I . How the organisation evaluates its exposure to technical vulnerabilities
- J . The organisation’s business continuity arrangements
- K . The organisation’s arrangements for information deletion
- L . Information security awareness, education and training
- M . How access to source code and development tools are managed
- N . The operation of the site CCTV and door control systems
- O . The organisation’s arrangements for maintaining equipment
- P . How power and data cables enter the building
Latest ISO-IEC-27001 Lead Auditor Dumps Valid Version with 100 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund