Paloalto Networks PCNSC Palo Alto Networks Certified Network Security Consultant Online Training
Paloalto Networks PCNSC Online Training
The questions for PCNSC were last updated at Apr 22,2025.
- Exam Code: PCNSC
- Exam Name: Palo Alto Networks Certified Network Security Consultant
- Certification Provider: Paloalto Networks
- Latest update: Apr 22,2025
An organization has Palo Alto Networks MGfWs that sendlogs to remote monitoring and security management platforms. The network team has report has excessive traffic on the corporate WAN.
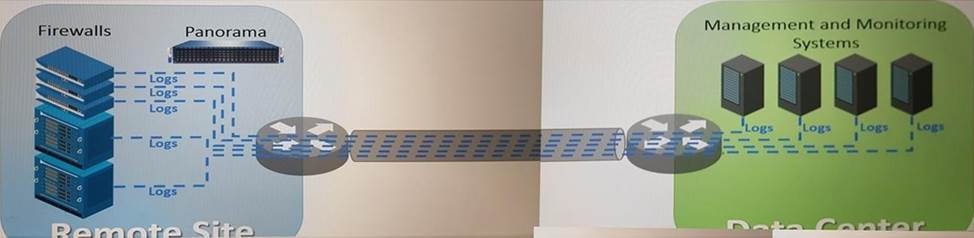
How could the Palo Alto Networks NOFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
- A . forward logs from firewalls only to Panorama, and have Panorama forward log* lo other external service.
- B . Any configuration on an M-500 would address the insufficient bandwidth concerns.
- C . Configure logcompression and optimization features on all remote firewalls.
- D . Forward logs from external sources to Panorama for correlation, arid from Panorama send to the NGFW
Refer to the exhibit.
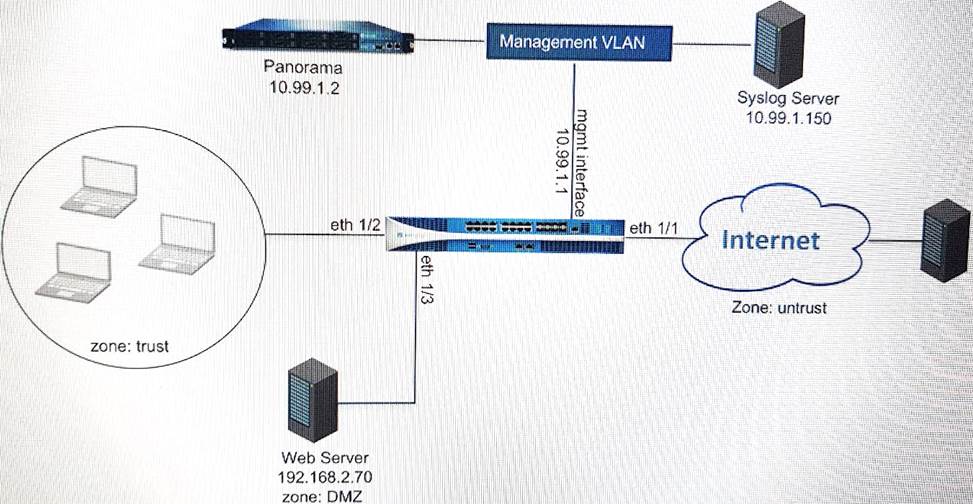
An administrator cannot see any of theTraffic logs from the Palo Alto Networks NGFW on Panorama. The configuration problem seems to be on the firewall side.
Where is the best place on the Palo Alto Networks NGFW to check whether the configuration is correct?
A)
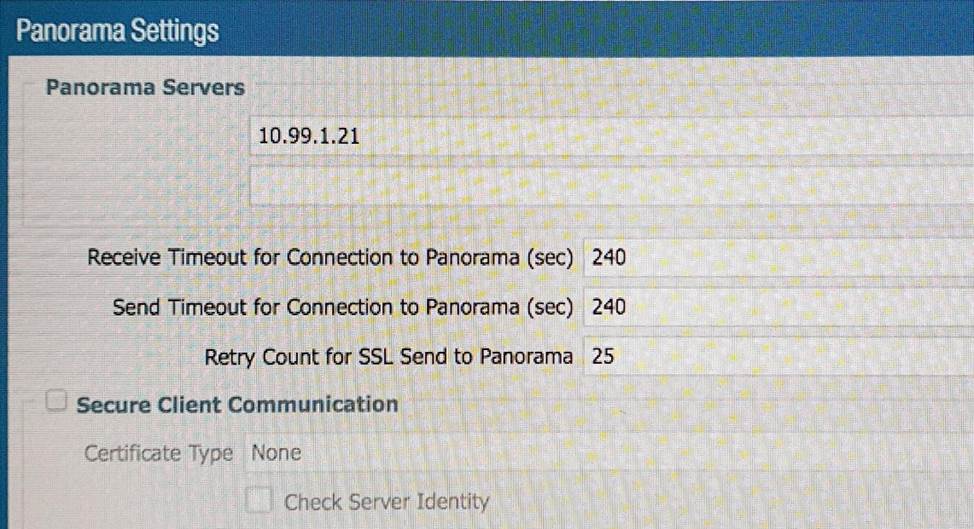
B)
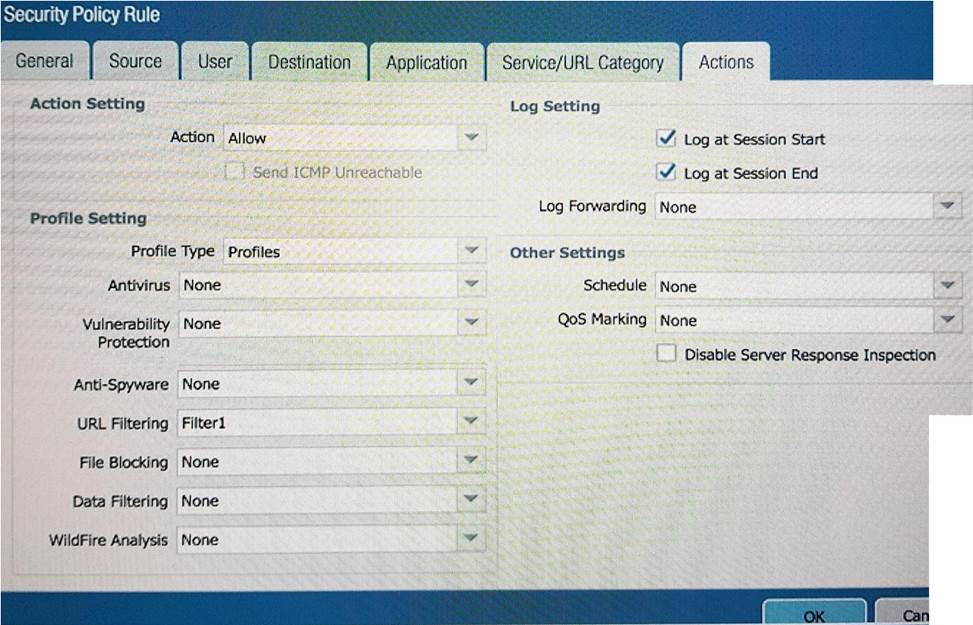
C)
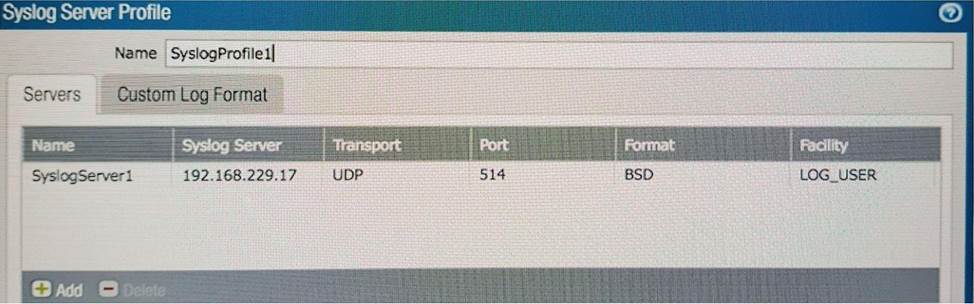
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
An administrator has left a firewall to used default port for all management services.
Which three function performed by the dataplane? (Choose three.)
- A . NTP
- B . antivirus
- C . NAT
- D . WildFire updates
- E . file blocking
A speed/duplex negotiation mismatch is between the Palo Alto Networks management port and the switch it connect.
How would an administrator configure the interface to IGbps?
- A . set deviceconfig system speed-duplex 10Gbps-full-duplex
- B . set deviceconfig interface speed-duplex 1Gbs–full-duplex
- C . set deviceconfig interface speed-duplex 1Gbs–half-duplex
- D . set deviceconfig system speed-duplex 1Gbs–half-duplex.
A firewall administrator has been asked to configure a Palo Alto Networks NGFW to prevent against compromised hosts trying tophone-number or bacon out to eternal command-and-control (C2) servers.
Which Security Profile type will prevent these behaviors?
- A . Vulnerability Protection
- B . Antivirus
- C . Wildfire
- D . Anti-Spyware
What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 8.1 version?
- A . When Panorama is reverted to an earlier PAN-OS release, variable used in template stacks will be removed authentically.
- B . Panorama cannot be reverted to an earlier PAN-OS release if variables are used in
templates or stacks. - C . An administrator must use the Expedition tool to adapt the configuration to the pre-pan-OS 8.1 state.
- D . Administrators need to manually update variable characters to those to used in pre-PAN-OS 8.1.
If an administrator wants to decrypt SMTP traffic and possesses the saver’s certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
- A . TLS Bidirectional Inspection
- B . SSL Inbound Inspection
- C . SSH Forward now proxy
- D . SMTP inbound Decryption
An administrator has enabled OSPF on a virtual router on the NGFW OSPF is not adding new routes to the virtual router.
Which two options enable the administrator top troubleshoot this issue? (Choose two.)
- A . Perform atraffic pcap at the routing stage.
- B . View System logs.
- C . Add a redistribution profile to forward as BGP updates.
- D . View Runtime Status virtual router.
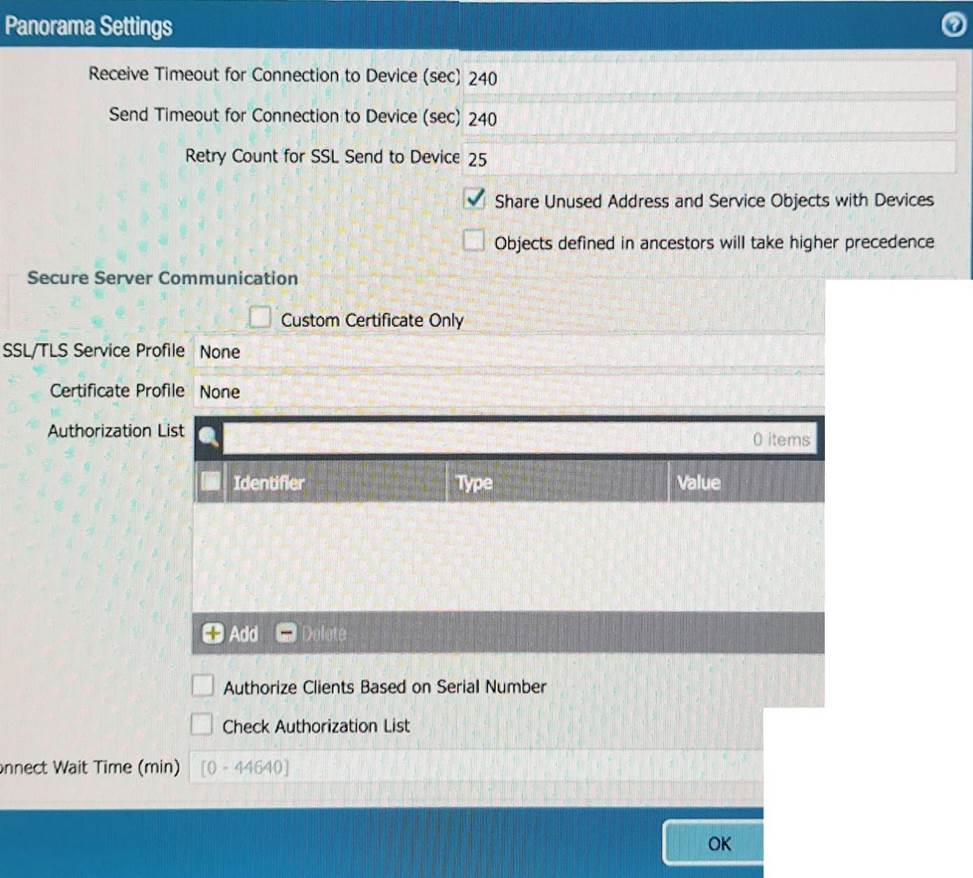
Which processing order will be enabled when a panorama administrator selects the setting "Objects defined in ancestors will takes higher precedence?
- A . Descendant objects, will take precedence overancestor objects.
- B . Ancestor will have precedence over descendant objects.
- C . Ancestor objects will have precedence over other ancestor objects.
- D . Descendant object will take precedence over other descendant objects.
Which administrative authentication method supports authorization by an external service?
- A . RADIUS
- B . SSH keys
- C . Certification
- D . LDAP
Latest PCNSC Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

