Paloalto Networks PCDRA Palo Alto Networks Certified Detection and Remediation Analyst Online Training
Paloalto Networks PCDRA Online Training
The questions for PCDRA were last updated at Dec 19,2025.
- Exam Code: PCDRA
- Exam Name: Palo Alto Networks Certified Detection and Remediation Analyst
- Certification Provider: Paloalto Networks
- Latest update: Dec 19,2025
In incident-related widgets, how would you filter the display to only show incidents that were “starred”?
- A . Create a custom XQL widget
- B . This is not currently supported
- C . Create a custom report and filter on starred incidents
- D . Click the star in the widget
Where would you view the WildFire report in an incident?
- A . next to relevant Key Artifacts in the incidents details page
- B . under Response –> Action Center
- C . under the gear icon –> Agent Audit Logs
- D . on the HUB page at apps.paloaltonetworks.com
What does the following output tell us?
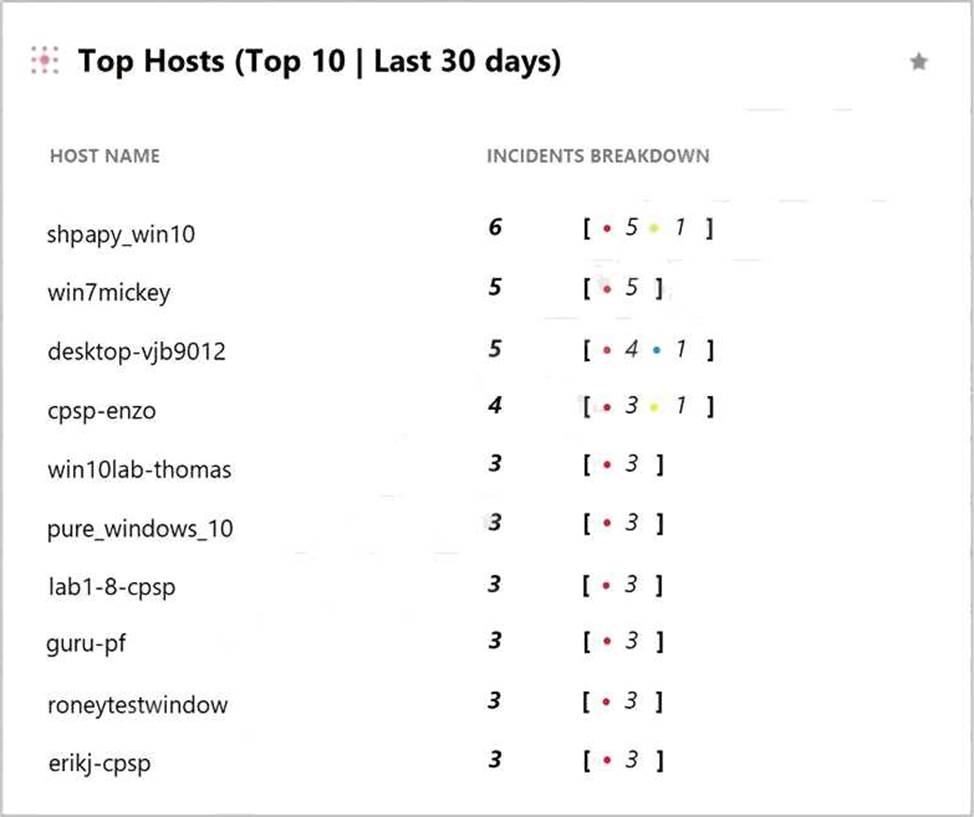
- A . There is one low severity incident.
- B . Host shpapy_win10 had the most vulnerabilities.
- C . There is one informational severity alert.
- D . This is an actual output of the Top 10 hosts with the most malware.
Which engine, of the following, in Cortex XDR determines the most relevant artifacts in each alert and aggregates all alerts related to an event into an incident?
- A . Sensor Engine
- B . Causality Analysis Engine
- C . Log Stitching Engine
- D . Causality Chain Engine
Which type of BIOC rule is currently available in Cortex XDR?
- A . Threat Actor
- B . Discovery
- C . Network
- D . Dropper
In Windows and macOS you need to prevent the Cortex XDR Agent from blocking execution of a file based on the digital signer.
What is one way to add an exception for the singer?
- A . In the Restrictions Profile, add the file name and path to the Executable Files allow list.
- B . Create a new rule exception and use the singer as the characteristic.
- C . Add the signer to the allow list in the malware profile.
- D . Add the signer to the allow list under the action center page.
As a Malware Analyst working with Cortex XDR you notice an alert suggesting that there was a prevented attempt to download Cobalt Strike on one of your servers. Days later, you learn about a massive ongoing supply chain attack. Using Cortex XDR you recognize that your server was compromised by the attack and that Cortex XDR prevented it.
What steps can you take to ensure that the same protection is extended to all your servers?
- A . Create Behavioral Threat Protection (BTP) rules to recognize and prevent the activity.
- B . Enable DLL Protection on all servers but there might be some false positives.
- C . Create IOCs of the malicious files you have found to prevent their execution.
- D . Enable Behavioral Threat Protection (BTP) with cytool to prevent the attack from spreading.
Which statement is true based on the following Agent Auto Upgrade widget?
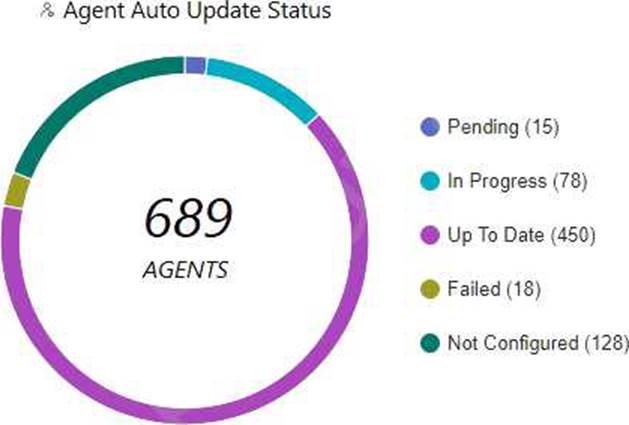
- A . There are a total of 689 Up To Date agents.
- B . Agent Auto Upgrade was enabled but not on all endpoints.
- C . Agent Auto Upgrade has not been enabled.
- D . There are more agents in Pending status than In Progress status.
What is the purpose of targeting software vendors in a supply-chain attack?
- A . to take advantage of a trusted software delivery method.
- B . to steal users’ login credentials.
- C . to access source code.
- D . to report Zero-day vulnerabilities.
What is the standard installation disk space recommended to install a Broker VM?
- A . 1GB disk space
- B . 2GB disk space
- C . 512GB disk space
- D . 256GB disk space
Latest PCDRA Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

