Paloalto Networks PCCET Palo Alto Networks Certified Cybersecurity Entry-level Technician Online Training
Paloalto Networks PCCET Online Training
The questions for PCCET were last updated at Oct 15,2025.
- Exam Code: PCCET
- Exam Name: Palo Alto Networks Certified Cybersecurity Entry-level Technician
- Certification Provider: Paloalto Networks
- Latest update: Oct 15,2025
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A . Dynamic
- B . Pre-exploit protection
- C . Bare-metal
- D . Static
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
- A . connectors and interfaces
- B . infrastructure and containers
- C . containers and developers
- D . data center and UPS
Which type of Wi-Fi attack depends on the victim initiating the connection?
- A . Evil twin
- B . Jasager
- C . Parager
- D . Mirai
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
- A . North-South traffic
- B . Intrazone traffic
- C . East-West traffic
- D . Interzone traffic
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A . NetOps
- B . SecOps
- C . SecDevOps
- D . DevOps
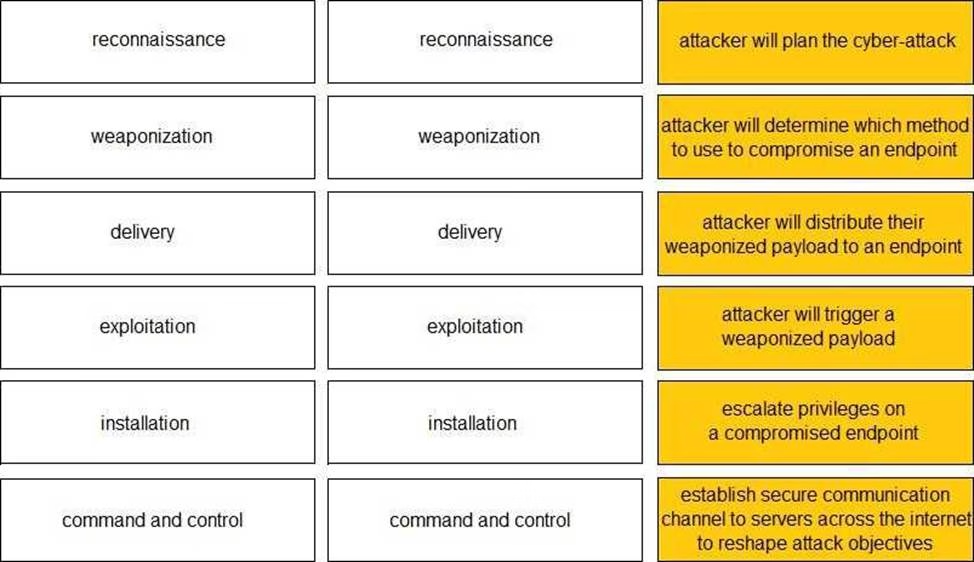
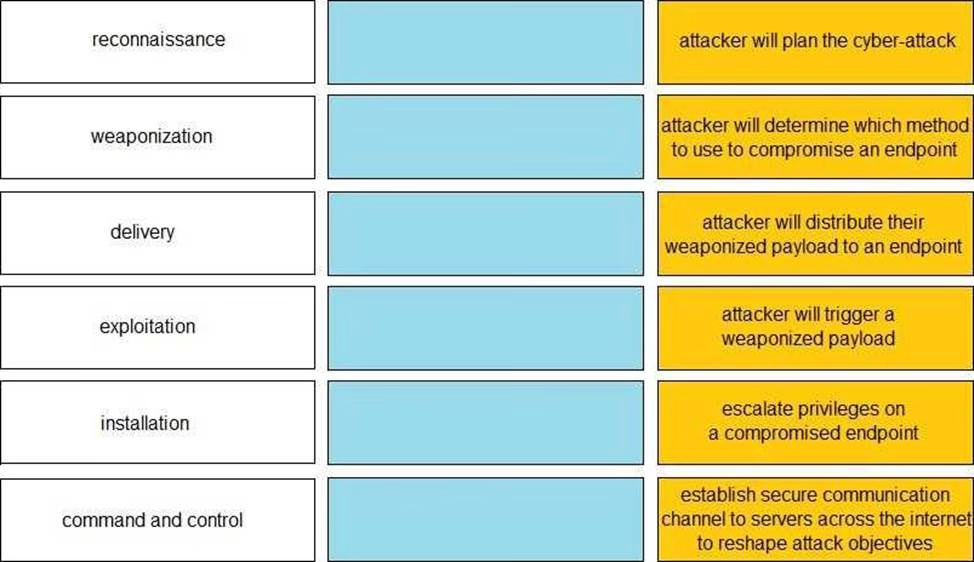
DRAG DROP
Given the graphic, match each stage of the cyber-attack lifecycle to its description.
DRAG DROP
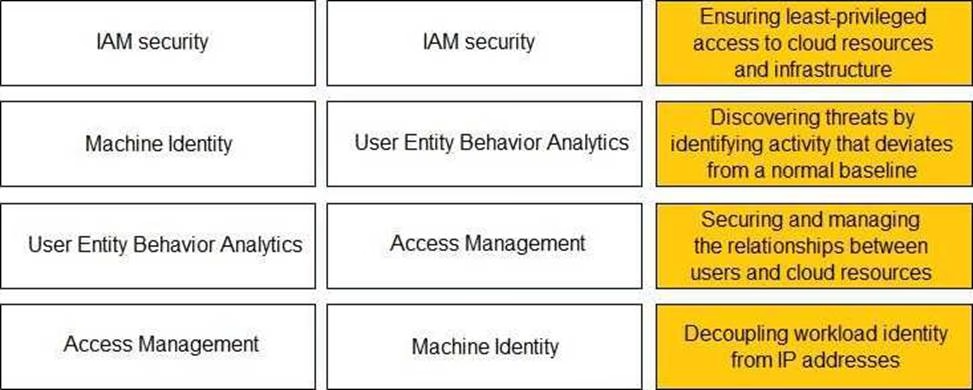
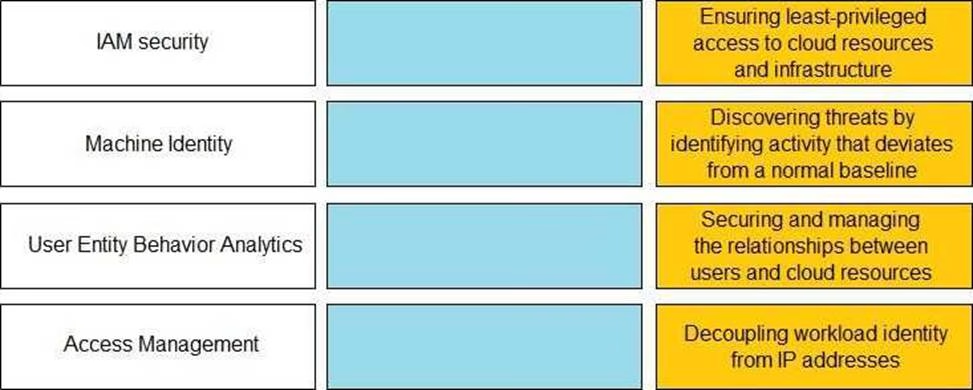
Match the Identity and Access Management (IAM) security control with the appropriate definition.
On an endpoint, which method should you use to secure applications against exploits?
- A . endpoint-based firewall
- B . strong user passwords
- C . full-disk encryption
- D . software patches
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
- A . Department of Homeland Security
- B . MITRE
- C . Office of Cyber Security and Information Assurance
- D . Cybersecurity Vulnerability Research Center
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
- A . MineMeld
- B . AutoFocus
- C . WildFire
- D . Cortex XDR
Latest PCCET Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund