Palo Alto Networks PCNSE6 Palo Alto Networks Certified Network Security Engineer 6 Online Training
Palo Alto Networks PCNSE6 Online Training
The questions for PCNSE6 were last updated at Dec 24,2025.
- Exam Code: PCNSE6
- Exam Name: Palo Alto Networks Certified Network Security Engineer 6
- Certification Provider: Palo Alto Networks
- Latest update: Dec 24,2025
A firewall administrator is troubleshooting problems with traffic passing through the Palo Alto Networks firewall.
Which method will show the global counters associated with the traffic after configuring the appropriate packet filters?
- A . From the CLI, issue the show counter interface command for the egress interface.
- B . From the GUI, select "Show global counters" under the Monitor tab.
- C . From the CLI, issue the show counter global filter packet-filter yes command.
- D . From the CLI, issue the show counter interface command for the ingress interface.
Which feature can be configured with an IPv6 address?
- A . Static Route
- B . RIPv2
- C . DHCP Server
- D . BGP
When creating an application filter, which of the following is true?
- A . They are used by malware
- B . Excessive bandwidth may be used as a filter match criteria
- C . They are called dynamic because they automatically adapt to new IP addresses
- D . They are called dynamic because they will automatically include new applications from an application signature update if the new application’s type is included in the filter
Which statement accurately reflects the functionality of using regions as objects in Security policies?
- A . Predefined regions are provided for countries, not but not for cities. The administrator can set up custom regions, including latitude and longitude, to specify the geographic position of that particular region.
- B . The administrator can set up custom regions, including latitude and longitude, to specify the geographic position of that particular region. These custom regions can be used in the "Source User" field of the Security Policies.
- C . Regions cannot be used in the "Source User" field of the Security Policies, unless the administrator has set up custom regions.
- D . The administrator can set up custom regions, including latitude and longitude, to specify the geographic position of that particular region. Both predefined regions and custom regions can be used in the "Source User" field.
In Active/Active HA environments, redundancy for the HA3 interface can be achieved by
- A . Configuring a corresponding HA4 interface
- B . Configuring HA3 as an Aggregate Ethernet bundle
- C . Configuring multiple HA3 interfaces
- D . Configuring HA3 in a redundant group
A Palo Alto Networks firewall has the following interface configuration;
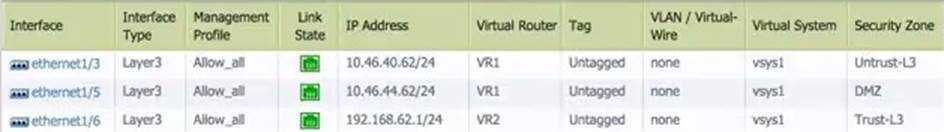
Hosts are directly connected on the following interfaces:
Ethernet 1/6 – Host IP 192.168.62.2
Ethernet 1/3 – Host IP 10.46.40.63
The security administrator is investigating why ICMP traffic between the hosts is not working.
She first ensures that ail traffic is allowed between zones based on the following security policy rule:
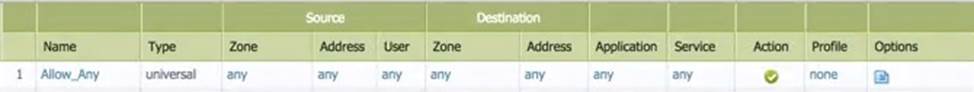
The routing table of the firewall shows the following output:
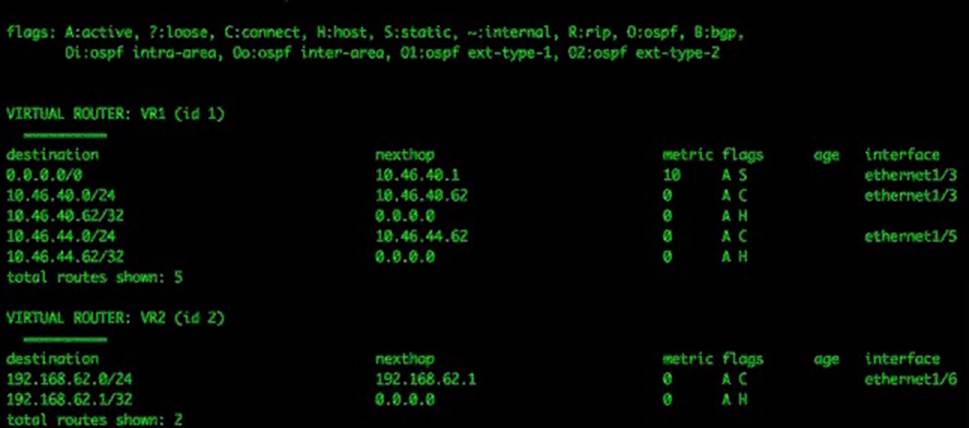
Which interface configuration change should be applied to ethernet1/6 to allow the two hosts to communicate based on this information?
- A . Change the Management Profile.
- B . Change the security policy to explicitly allow ICMP on this interface.
- C . Change the configured zone to DMZ.
- D . Change the Virtual Router setting to VR1.
What can cause missing SSL packets when performing a packet capture on data plane interfaces?
- A . There is a hardware problem with the offloading FPGA on the management plane.
- B . The missing packets are offloaded to the management plane CPU.
- C . The packets are hardware offloaded to the offload processor on the data plane.
- D . The packets are not captured because they are encrypted.
Which three processor types are found on the data plane of a PA-5050? Choose 3 answers
- A . Multi-Core Security Processor
- B . Signature Match Processor
- C . Network Processor
- D . Protocol Decoder Processor
- E . Management Processor
What happens at the point of Threat Prevention license expiration?
- A . Threat Prevention no longer updated; existing database still effective
- B . Threat Prevention is no longer used; applicable traffic is allowed
- C . Threat Prevention no longer used; applicable traffic is blocked
- D . Threat Prevention no longer used; traffic is allowed or blocked by configuration per Security Rule
Wildfire may be used for identifying which of the following types of traffic?
- A . Malware
- B . DNS
- C . DHCP
- D . URL Content
Latest PCNSE6 Dumps Valid Version with 153 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

