Palo Alto Networks PCNSE Palo Alto Networks Certified Network Security Engineer Exam Online Training
Palo Alto Networks PCNSE Online Training
The questions for PCNSE were last updated at Apr 23,2025.
- Exam Code: PCNSE
- Exam Name: Palo Alto Networks Certified Network Security Engineer Exam
- Certification Provider: Palo Alto Networks
- Latest update: Apr 23,2025
Which two statements correctly describe Session 380280? (Choose two.)

- A . The session went through SSL decryption processing.
- B . The session has ended with the end-reason unknown.
- C . The application has been identified as web-browsing.
- D . The session did not go through SSL decryption processing.
An administrator is troubleshooting why video traffic is not being properly classified.
If this traffic does not match any QoS classes, what default class is assigned?
- A . 1
- B . 2
- C . 3
- D . 4
Refer to Exhibit:
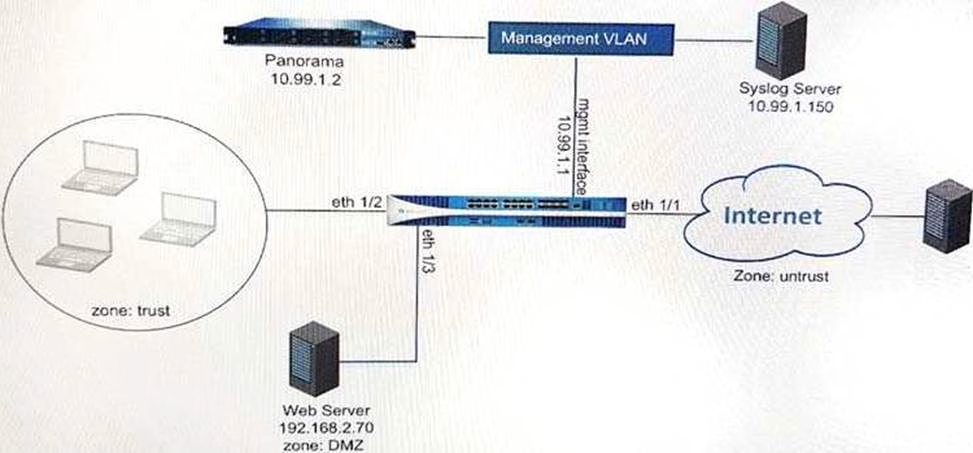
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall.
Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
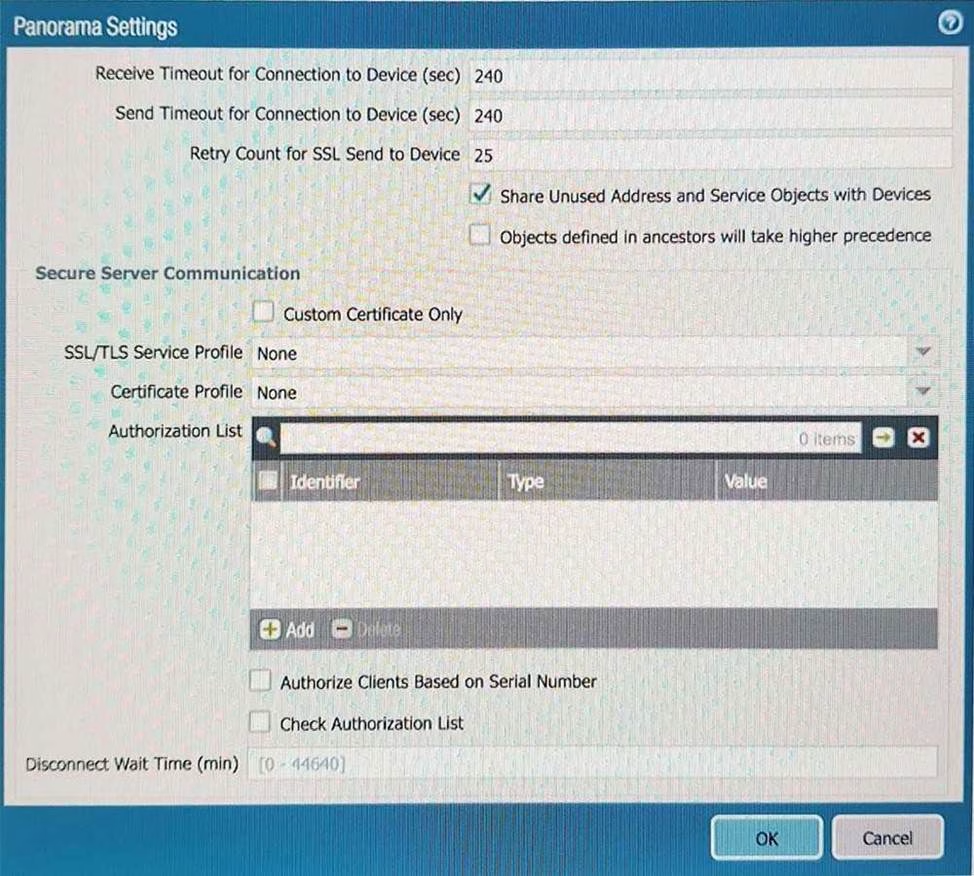
A)
B)
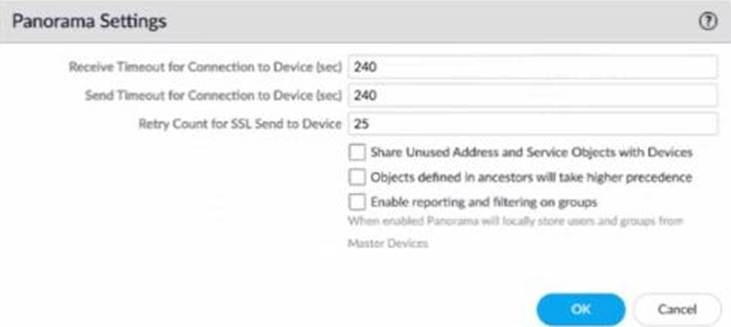
C)
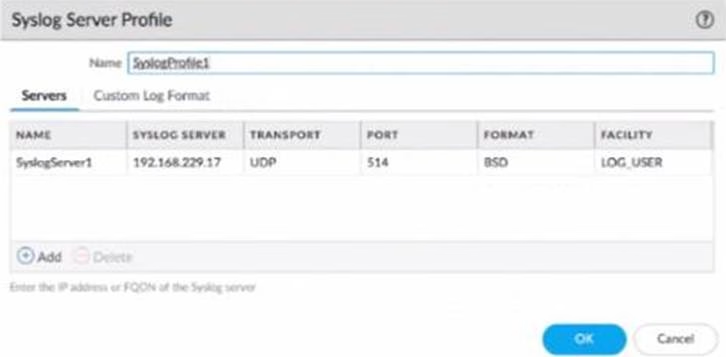
D)
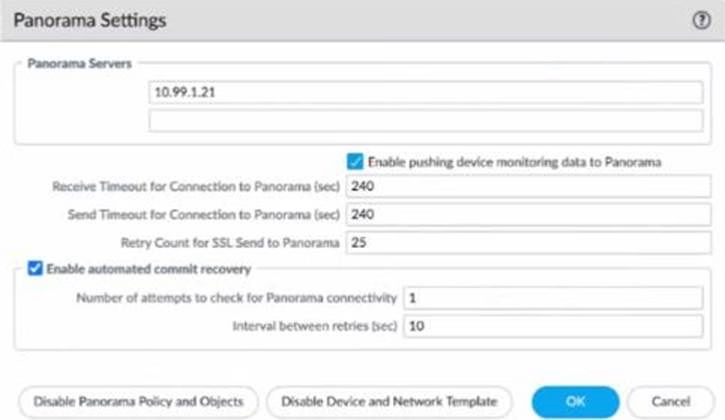
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
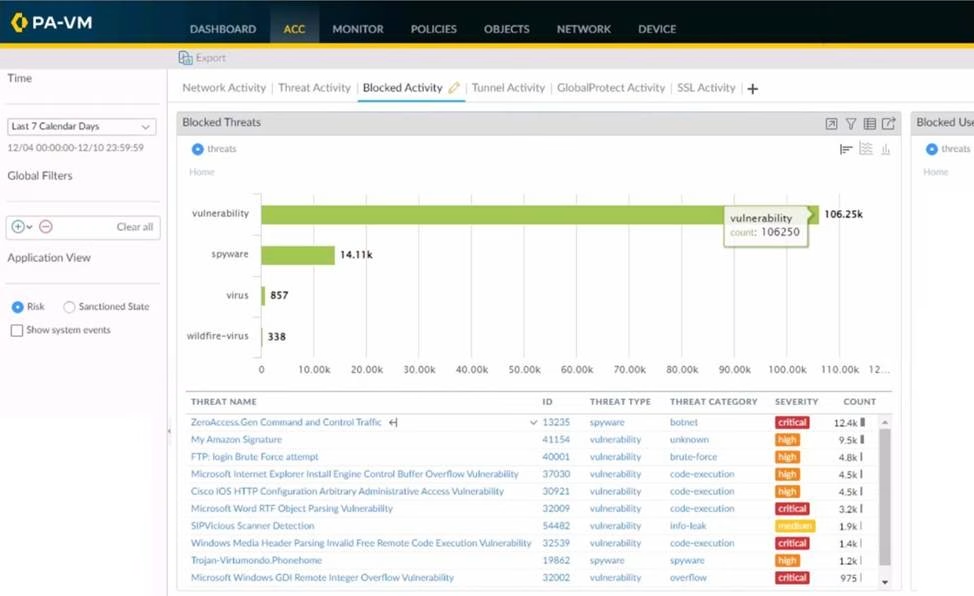
Using the above screenshot of the ACC, what is the best method to set a global filter, narrow down Blocked User Activity, and locate the user(s) that could be compromised by a botnet?
- A . Click the hyperlink for the Zero Access.Gen threat.
- B . Click the left arrow beside the Zero Access.Gen threat.
- C . Click the source user with the highest threat count.
- D . Click the hyperlink for the hotport threat Category.
An administrator has configured OSPF with Advanced Routing enabled on a Palo Alto Networks firewall running PAN-OS 10.2. After OSPF was configured, the administrator noticed that OSPF routes were not being learned.
Which two actions could an administrator take to troubleshoot this issue? (Choose two.)
- A . Run the CLI command show advanced-routing ospf neighbor
- B . In the WebUI, view the Runtime Stats in the virtual router
- C . Look for configuration problems in Network > virtual router > OSPF
- D . In the WebUI, view Runtime Stats in the logical router
A network administrator configured a site-to-site VPN tunnel where the peer device will act as initiator None of the peer addresses are known
What can the administrator configure to establish the VPN connection?
- A . Set up certificate authentication.
- B . Use the Dynamic IP address type.
- C . Enable Passive Mode
- D . Configure the peer address as an FQDN.
An engineer is configuring a template in Panorama which will contain settings that need to be applied to all firewalls in production.
Which three parts of a template an engineer can configure? (Choose three.)
- A . NTP Server Address
- B . Antivirus Profile
- C . Authentication Profile
- D . Service Route Configuration
- E . Dynamic Address Groups
In a template, which two objects can be configured? (Choose two.)
- A . SD-WAN path quality profile
- B . Monitor profile
- C . IPsec tunnel
- D . Application group
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama. However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
- A . Export the log database.
- B . Use the import option to pull logs.
- C . Use the scp logdb export command.
- D . Use the ACC to consolidate the logs.
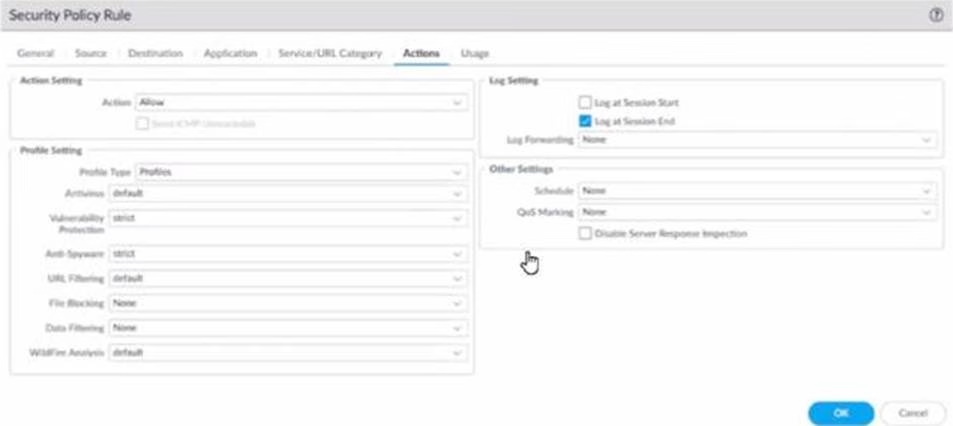
Refer to the exhibit.
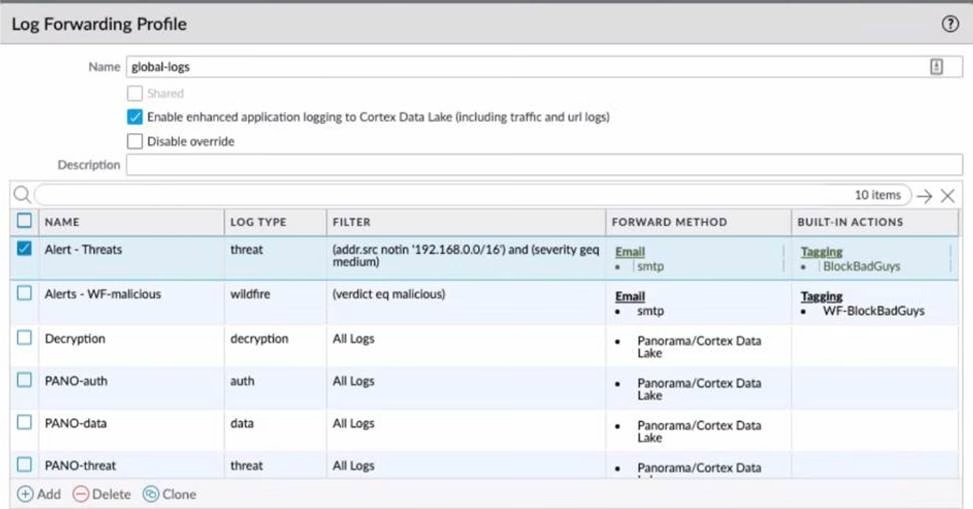
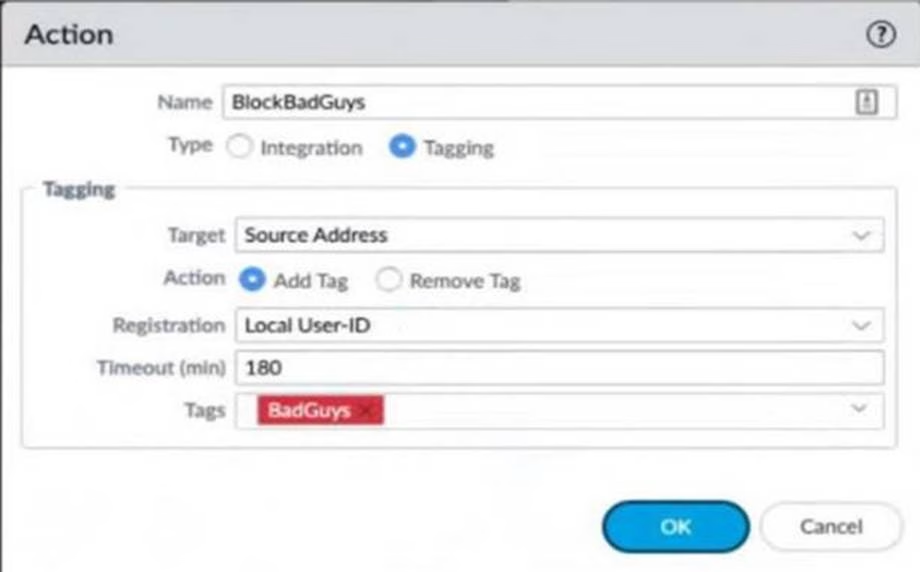
Review the images. A firewall policy that permits web traffic includes the global-logs policy is depicted
What is the result of traffic that matches the "Alert – Threats" Profile Match List?
- A . The source address of SMTP traffic that matches a threat is automatically blocked as BadGuys for 180 minutes.
- B . The source address of traffic that matches a threat is automatically blocked as BadGuys for 180 minutes.
- C . The source address of traffic that matches a threat is automatically tagged as BadGuys for 180 minutes.
- D . The source address of SMTP traffic that matches a threat is automatically tagged as BadGuys for 180 minutes.
Latest PCNSE Dumps Valid Version with 280 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

