Palo Alto Networks PCNSE Palo Alto Networks Certified Network Security Engineer Exam Online Training
Palo Alto Networks PCNSE Online Training
The questions for PCNSE were last updated at Apr 23,2025.
- Exam Code: PCNSE
- Exam Name: Palo Alto Networks Certified Network Security Engineer Exam
- Certification Provider: Palo Alto Networks
- Latest update: Apr 23,2025
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0."
How should the administrator identify the root cause of this error message?
- A . In the IKE Gateway configuration, verify that the IP address for each VPN peer is accurate
- B . Verify that the IP addresses can be pinged and that routing issues are not causing the connection failure
- C . Check whether the VPN peer on one end is set up correctly using policy-based VPN
- D . In the IPSec Crypto profile configuration, verify that PFS is either enabled on both VPN peers or disabled on both VPN peers.
A network administrator is trying to prevent domain username and password submissions to phishing sites on some allowed URL categories
Which set of steps does the administrator need to take in the URL Filtering profile to prevent credential phishing on the firewall?
- A . Choose the URL categories in the User Credential Submission column and set action to block Select the User credential Detection tab and select Use Domain Credential Filter Commit
- B . Choose the URL categories in the User Credential Submission column and set action to block Select the User credential Detection tab and select use IP User Mapping Commit
- C . Choose the URL categories on Site Access column and set action to block Click the User credential
Detection tab and select IP User Mapping Commit - D . Choose the URL categories in the User Credential Submission column and set action to block Select the URL filtering settings and enable Domain Credential Filter Commit
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
- A . Inherit settings from the Shared group
- B . Inherit IPSec crypto profiles
- C . Inherit all Security policy rules and objects
- D . Inherit parent Security policy rules and objects
An administrator Just enabled HA Heartbeat Backup on two devices However, the status on tie firewall’s dashboard is showing as down High Availability.
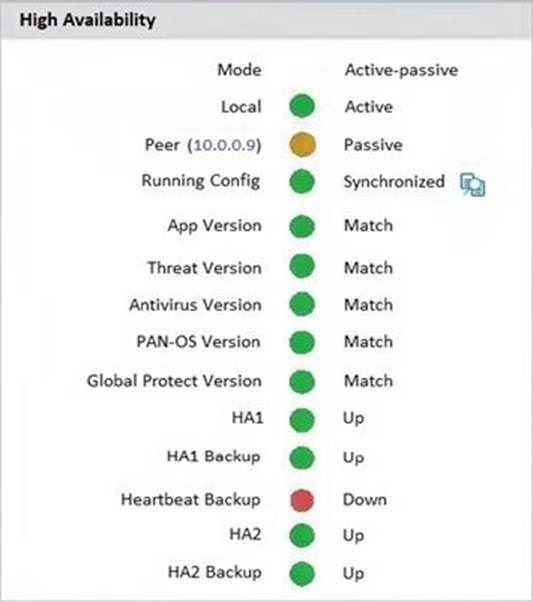
What could an administrator do to troubleshoot the issue?
- A . Go to Device > High Availability> General > HA Pair Settings > Setup and configuring the peer IP for heartbeat backup
- B . Check peer IP address In the permit list In Device > Setup > Management > Interfaces > Management Interface Settings
- C . Go to Device > High Availability > HA Communications> General> and check the Heartbeat Backup under Election Settings
- D . Check peer IP address for heartbeat backup to Device > High Availability > HA Communications > Packet Forwarding settings.
An administrator has purchased WildFire subscriptions for 90 firewalls globally.
What should the administrator consider with regards to the WildFire infra-structure?
- A . To comply with data privacy regulations, WildFire signatures and ver-dicts are not shared globally.
- B . Palo Alto Networks owns and maintains one global cloud and four WildFire regional clouds.
- C . Each WildFire cloud analyzes samples and generates malware signatures and verdicts independently of the other WildFire clouds.
- D . The WildFire Global Cloud only provides bare metal analysis.
Which three items must be configured to implement application override? (Choose three )
- A . Custom app
- B . Security policy rule
- C . Application override policy rule
- D . Decryption policy rule
- E . Application filter
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
- A . HSCI-C
- B . Console Backup
- C . HA3
- D . HA2 backup
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
- A . Resource Protection
- B . TCP Port Scan Protection
- C . Packet Based Attack Protection
- D . Packet Buffer Protection
What is the best definition of the Heartbeat Interval?
- A . The interval in milliseconds between hello packets
- B . The frequency at which the HA peers check link or path availability
- C . The frequency at which the HA peers exchange ping
- D . The interval during which the firewall will remain active following a link monitor failure
After importing a pre-configured firewall configuration to Panorama, what step is required to ensure a commit/push is successful without duplicating local configurations?
- A . Ensure Force Template Values is checked when pushing configuration.
- B . Push the Template first, then push Device Group to the newly managed firewall.
- C . Perform the Export or push Device Config Bundle to the newly managed firewall.
- D . Push the Device Group first, then push Template to the newly managed firewall
Latest PCNSE Dumps Valid Version with 280 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

