Palo Alto Networks PCNSE Palo Alto Networks Certified Network Security Engineer Exam Online Training
Palo Alto Networks PCNSE Online Training
The questions for PCNSE were last updated at Apr 21,2025.
- Exam Code: PCNSE
- Exam Name: Palo Alto Networks Certified Network Security Engineer Exam
- Certification Provider: Palo Alto Networks
- Latest update: Apr 21,2025
Which log type would provide information about traffic blocked by a Zone Protection profile?
- A . Data Filtering
- B . IP-Tag
- C . Traffic
- D . Threat
Refer to the exhibit.
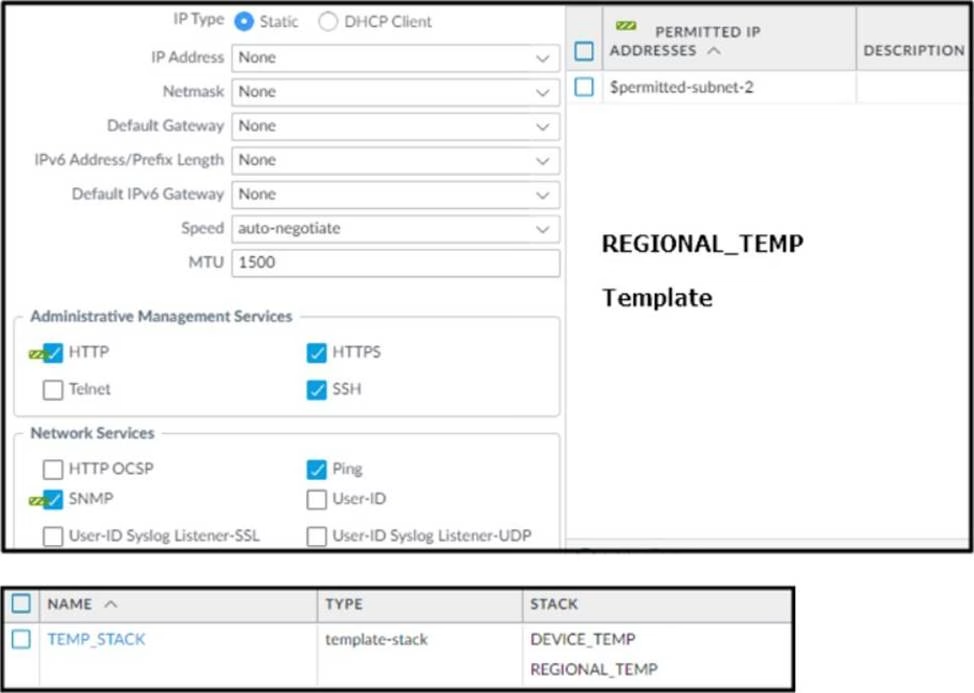
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
- A . The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1.
- B . The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-2.
- C . The firewall will allow HTTP, Telnet, SNMP, HTTPS, SSH and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
- D . The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
An administrator troubleshoots an issue that causes packet drops.
Which log type will help the engineer verify whether packet buffer protection was activated?
- A . Data Filtering
- B . Configuration
- C . Threat
- D . Traffic
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
- A . NAT
- B . DOS protection
- C . QoS
- D . Tunnel inspection
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security
certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
- A . A web server certificate signed by the organization’s PKI
- B . A self-signed certificate generated on the firewall
- C . A subordinate Certificate Authority certificate signed by the organization’s PKI
- D . A web server certificate signed by an external Certificate Authority
Which new PAN-OS 11.0 feature supports IPv6 traffic?
- A . DHCPv6 Client with Prefix Delegation
- B . OSPF
- C . DHCP Server
- D . IKEv1
An organization is interested in migrating from their existing web proxy architecture to the Web Proxy feature of their PAN-OS 11.0 firewalls. Currently. HTTP and SSL requests contain the c IP address of the web server and the client browser is redirected to the proxy
Which PAN-OS proxy method should be configured to maintain this type of traffic flow?
- A . DNS proxy
- B . Explicit proxy
- C . SSL forward proxy
- D . Transparent proxy
Which two profiles should be configured when sharing tags from threat logs with a remote User-ID agent? (Choose two.)
- A . Log Ingestion
- B . HTTP
- C . Log Forwarding
- D . LDAP
An administrator needs to identify which NAT policy is being used for internet traffic.
From the Monitor tab of the firewall GUI, how can the administrator identify which NAT policy is in use for a traffic flow?
- A . Click Session Browser and review the session details.
- B . Click Traffic view and review the information in the detailed log view.
- C . Click Traffic view; ensure that the Source or Destination NAT columns are included and review the information in the detailed log view.
- D . Click App Scope > Network Monitor and filter the report for NAT rules.
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
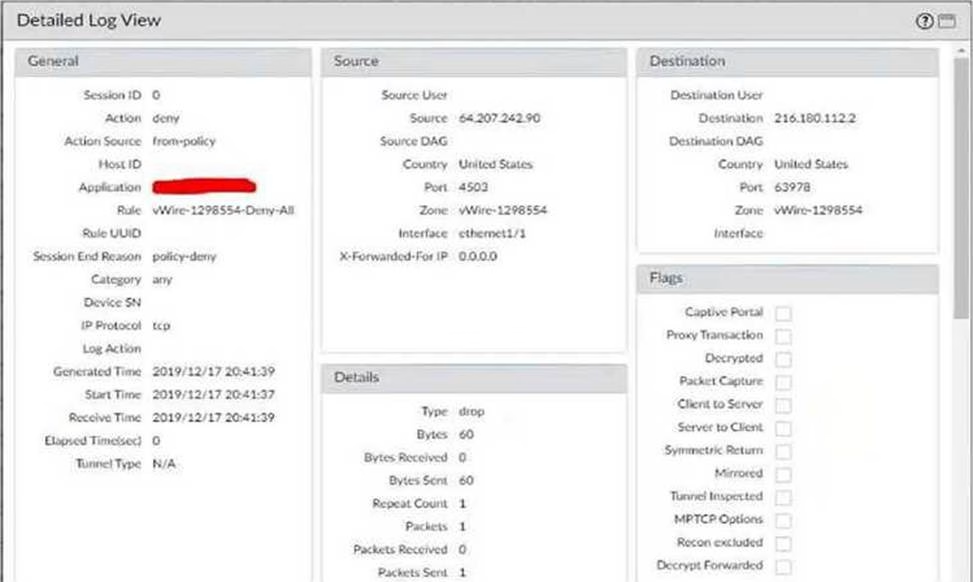
- A . Incomplete
- B . unknown-tcp
- C . Insufficient-data
- D . not-applicable
Latest PCNSE Dumps Valid Version with 280 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

