Palo Alto Networks PCNSE Palo Alto Networks Certified Network Security Engineer Exam Online Training
Palo Alto Networks PCNSE Online Training
The questions for PCNSE were last updated at Apr 28,2025.
- Exam Code: PCNSE
- Exam Name: Palo Alto Networks Certified Network Security Engineer Exam
- Certification Provider: Palo Alto Networks
- Latest update: Apr 28,2025
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this.
Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
- A . Navigate to Network > Zone Protection Click Add
Select Packet Based Attack Protection > TCP/IP Drop Set "Reject Non-syn-TCP" to No Set "Asymmetric Path" to Bypass - B . > set session tcp-reject-non-syn no
- C . Navigate to Network > Zone Protection Click Add
Select Packet Based Attack Protection > TCP/IP Drop Set "Reject Non-syn-TCP" to Global Set "Asymmetric Path" to Global - D . # set deviceconfig setting session tcp-reject-non-syn no
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL.
When creating a new rule, what is needed to allow the application to resolve dependencies?
- A . Add SSL and web-browsing applications to the same rule.
- B . Add web-browsing application to the same rule.
- C . Add SSL application to the same rule.
- D . SSL and web-browsing must both be explicitly allowed.
What are three tasks that cannot be configured from Panorama by using a template stack? (Choose three.)
- A . Change the firewall management IP address
- B . Configure a device block list
- C . Add administrator accounts
- D . Rename a vsys on a multi-vsys firewall
- E . Enable operational modes such as normal mode, multi-vsys mode, or FIPS-CC mode
Given the following snippet of a WildFire submission log did the end-user get access to the requested information and why or why not?
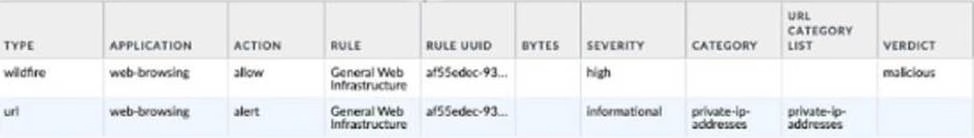
- A . Yes, because the action is set to alert
- B . No, because this is an example from a defeated phishing attack
- C . No, because the severity is high and the verdict is malicious.
- D . Yes, because the action is set to allow.
Which statement is correct given the following message from the PanGPA log on the GlobalProtect app?
Failed to connect to server at port:47 67
- A . The PanGPS process failed to connect to the PanGPA process on port 4767
- B . The GlobalProtect app failed to connect to the GlobalProtect Portal on port 4767
- C . The PanGPA process failed to connect to the PanGPS process on port 4767
- D . The GlobalProtect app failed to connect to the GlobalProtect Gateway on port 4767
An engineer reviews high availability (HA) settings to understand a recent HA failover event.
Review the screenshot below.
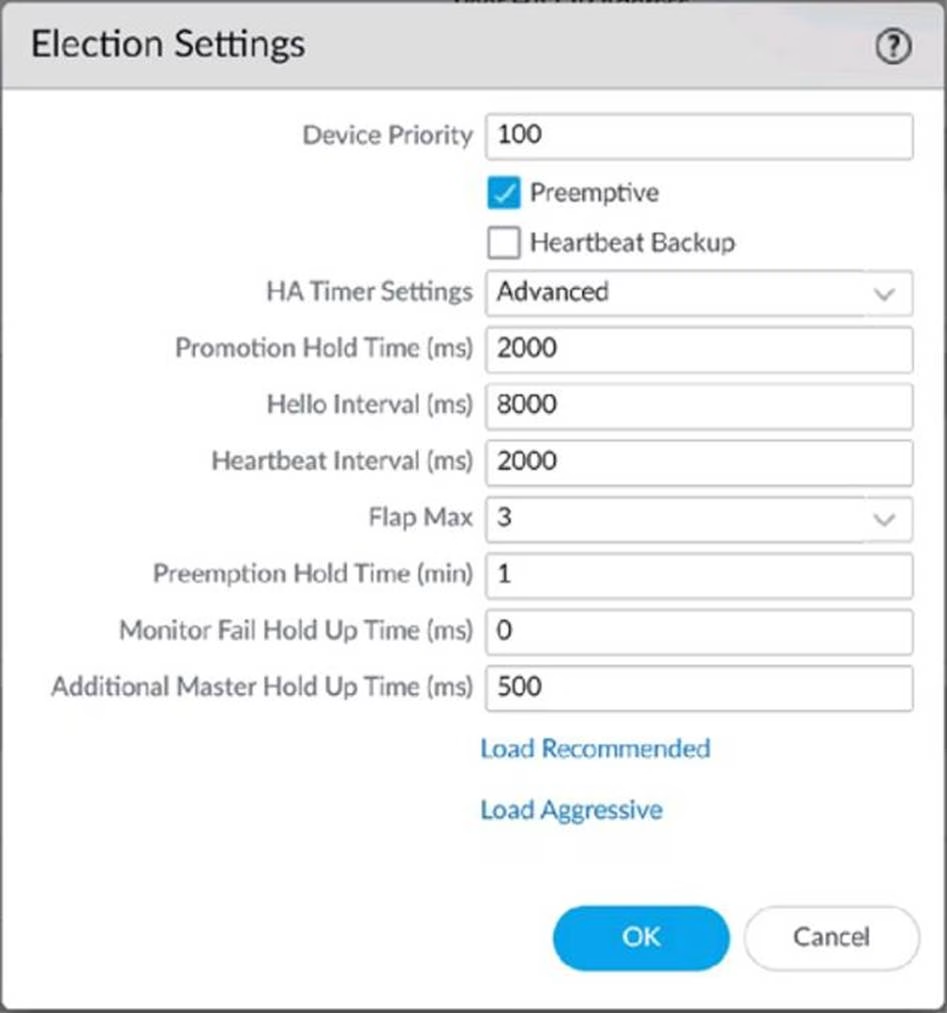
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
- A . Hello Interval
- B . Promotion Hold Time
- C . Heartbeat Interval
- D . Monitor Fail Hold Up Time
ln a security-first network, what is the recommended threshold value for apps and threats to be dynamically updated?
- A . 1 to 4 hours
- B . 6 to 12 hours
- C . 24 hours
- D . 36 hours
ln a security-first network, what is the recommended threshold value for apps and threats to be dynamically updated?
- A . 1 to 4 hours
- B . 6 to 12 hours
- C . 24 hours
- D . 36 hours
A company wants to add threat prevention to the network without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
- A . VirtualWire
- B . Layer3
- C . TAP
- D . Layer2
Latest PCNSE Dumps Valid Version with 280 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund