Where in Panorama would Zone Protection profiles be configured?
- A . Templates
- B . Device Groups
- C . Shared
- D . Panorama tab
A
Explanation:
Create a Zone Protection profile for the firewalls in the data center template (T_DataCenter). Select the Network tab and, in the Template drop-down, select T_DataCenter.
Select Network ProfilesZone Protection and click Add.
An administrator wants to prevent access to media content websites that are risky.
Which two URL categories should be combined in a custom URL category to accomplish this goal? (Choose two.)
- A . recreation-and-hobbies
- B . streaming-media
- C . known-risk
- D . high-risk
BD
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/content-inspection-features/url-filtering-multi-category.html
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/content-inspection-features/url-filtering-security-categories.html
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
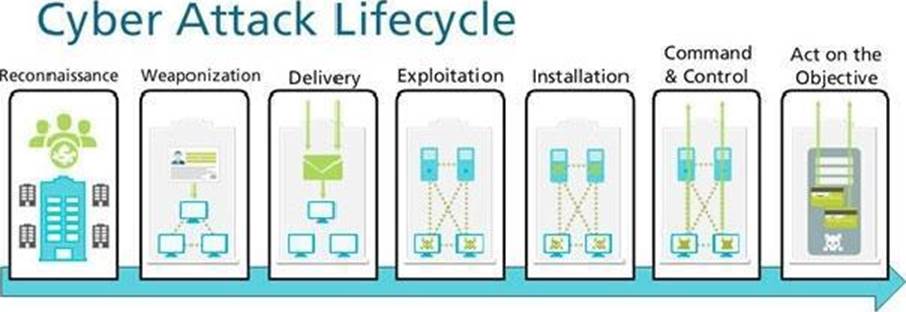
- A . Exploitation
- B . Installation
- C . Reconnaissance
- D . Act on Objective
A
Explanation:
https://www.paloaltonetworks.com/cyberpedia/how-to-break-the-cyber-attack-lifecycle
According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
- A . by minute
- B . hourly
- C . daily
- D . weekly
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/threat-prevention/best-practices-for-content-and-threat-content-updates/best-practices-mission-critical.html
An address object of type IP Wildcard Mask can be referenced in which part of the configuration?
- A . Security policy rule
- B . ACC global filter
- C . external dynamic list
- D . NAT address pool
A
Explanation:
You can use an address object of type IP Wildcard Mask only in a Security policy rule. https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/objects/objects-addresses IP Wildcard Mask
–Enter an IP wildcard address in the format of an IPv4 address followed by a slash and a mask (which must begin with a zero); for example, 10.182.1.1/0.127.248.0. In the wildcard mask, a zero (0) bit indicates that the bit being compared must match the bit in the IP address that is covered by the 0. A one (1) bit in the mask is a wildcard bit, meaning the bit being compared need not match the bit in the IP address that is covered by the 1. Convert the IP address and the wildcard mask to binary. To illustrate the matching: on binary snippet 0011, a wildcard mask of 1010 results in four matches (0001, 0011, 1001, and 1011).
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
- A . SAML
- B . TACACS+
- C . LDAP
- D . Kerberos
AB
Explanation:
The administrative accounts are defined on an external SAML, TACACS+, or RADIUS server.
The server performs both authentication and authorization. For authorization, you define Vendor-Specific Attributes (VSAs) on the TACACS+ or RADIUS server, or SAML attributes on the SAML server. PAN-OS maps the attributes to administrator roles, access domains, user groups, and virtual systems that you define on the firewall.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/firewall-administration/manage-
firewall-administrators/administrative-authentication.html
What do you configure if you want to set up a group of objects based on their ports alone?
- A . address groups
- B . custom objects
- C . application groups
- D . service groups
D
Explanation:
Service = layer 4, Application = layer 7
A Security Profile can block or allow traffic at which point?
- A . after it is matched to a Security policy rule that allows traffic
- B . on either the data plane or the management plane
- C . after it is matched to a Security policy rule that allows or blocks traffic
- D . before it is matched to a Security policy rule
A
Explanation:
Security Profiles are added to the end of Security policy rules. After a packet has been allowed by the Security policy.
Which three filter columns are available when setting up an Application Filter? (Choose three.)
- A . Parent App
- B . Category
- C . Risk
- D . Standard Ports
- E . Subcategory
BCE
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-web-interface-help/objects/objects-application-filters
What are three factors that can be used in domain generation algorithms? (Choose three.)
- A . cryptographic keys
- B . time of day
- C . other unique values
- D . URL custom categories
- E . IP address
ABC
Explanation:
Domain generation algorithms (DGAs) are used to auto-generate domains, typically in large numbers within the context of establishing a malicious command-and-control (C2) communications channel. DGA-based malware (such as Pushdo, BankPatch, and CryptoLocker) limit the number of domains from being blocked by hiding the location of their active C2 servers within a large number of possible
suspects, and can be algorithmically generated based on factors such as time of day, cryptographic keys, or other unique values.
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/threat-prevention/dns-security/domain-generation-algorithm-detection
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
- A . URL Filtering
- B . Vulnerability Protection
- C . Anti-Spyware
- D . Antivirus
C
Explanation:
In addition, you can enable the DNS sinkholing action in Anti-Spyware profiles to enable the firewall to forge a response to a DNS query for a known malicious domain, causing the malicious domain name to resolve to an IP address that you define.
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/security-profiles
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
- A . Block List
- B . Custom URL Categories
- C . PAN-DB URL Categories
- D . Allow List
BC
Explanation:
Action can be set to following three categories:
-Custom URL categories
-External dynamic Lists
-Pan-DB predefined URL categories
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/content-inspection-features/url-filtering-multi-category.html
Which interface type requires no routing or switching but applies Security or NAT policy rules before passing allowed traffic?
- A . Tap
- B . Virtual Wire
- C . Layer 2
- D . Layer 3
B
Explanation:
A virtual wire logically binds two Ethernet interfaces together, allowing for all traffic to pass between the interfaces, or just traffic with selected VLAN tags (no other switching or routing services are available). You can create virtual wire subinterfaces to classify traffic according to an IP address, IP range, or subnet. A virtual wire requires no changes to adjacent network devices.
A virtual wire can bind two Ethernet interfaces of the same medium (both copper or both fiber optic),
or bind a copper interface to a fiber optic interface.
In order to protect users against exploit kits that exploit a vulnerability and then automatically download malicious payloads, which Security profile should be configured?
- A . Anti-Spyware
- B . WildFire
- C . Vulnerability Protection
- D . Antivirus
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/security-profiles
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
- A . DNS Security
- B . Threat Prevention
- C . WildFire
- D . SD-Wan
B
Explanation:
An active Threat Prevention license is required to obtain Palo Alto Networks built-in EDLs. These built-in EDLs protect your network against malicious hosts.
Which prevention technique will prevent attacks based on packet count?
- A . zone protection profile
- B . URL filtering profile
- C . antivirus profile
- D . vulnerability profile
A
Explanation:
DoS Protection adds another layer of defense against attacks on individual devices, which can succeed if the Zone Protection profile thresholds are above the CPS rate of the attack on the device.
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis Unit 42 research and data gathered from telemetry?
- A . Palo Alto Networks C&C IP Addresses
- B . Palo Alto Networks Bulletproof IP Addresses
- C . Palo Alto Networks High-Risk IP Addresses
- D . Palo Alto Networks Known Malicious IP Addresses
D
Explanation:
Palo Alto Networks Known Malicious IP Addresses
–Contains IP addresses that are verified malicious based on WildFire analysis, Unit 42 research, and data gathered from telemetry (Share Threat Intelligence with Palo Alto Networks). Attackers use these IP addresses almost exclusively to distribute malware, initiate command-and-control activity,
and launch attacks.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/built-in-edls
An administrator reads through the following Applications and Threats Content Release Notes before an update:
Which rule would continue to allow the file upload to confluence after the update?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
In order to fulfill the corporate requirement to backup the configuration of Panorama and the Panorama-managed firewalls securely, which protocol should you select when adding a new scheduled config export?
- A . HTTPS
- B . SMB v3
- C . SCP
- D . FTP
In order to fulfill the corporate requirement to backup the configuration of Panorama and the Panorama-managed firewalls securely, which protocol should you select when adding a new scheduled config export?
- A . HTTPS
- B . SMB v3
- C . SCP
- D . FTP
What is a recommended consideration when deploying content updates to the firewall from Panorama?
- A . Before deploying content updates, always check content release version compatibility.
- B . Content updates for firewall A/P HA pairs can only be pushed to the active firewall.
- C . Content updates for firewall A/A HA pairs need a defined master device.
- D . After deploying content updates, perform a commit and push to Panorama.
A
Explanation:
The content release version on the Panorama management server must be the same (or earlier) version as the content release version on any Dedicated Log Collectors or managed firewalls. https://docs.paloaltonetworks.com/panorama/9-1/panorama-admin/set-up-panorama/install-content-and-software-updates-for-panorama/panorama-log-collector-firewall-and-wildfire-version-compatibility#id09d0b616-1197-4f80-be05-fdd7e75f8652
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?
- A . Root
- B . Dynamic
- C . Role-based
- D . Superuser
C
Explanation:
Role Based profile roles: These are custom roles you can configure for more granular access control over the functional areas of the web interface, CLI, and XML API. For example, you can create an Admin Role profile role for your operations staff that provides access to the firewall and network configuration areas of the web interface and a separate profile for your security administrators that provides access to security policy definitions, logs, and reports. On a firewall with multiple virtual systems, you can select whether the role defines access for all virtual systems or specific virtual systems. After new features are added to the product, you must update the roles with corresponding access privileges; the firewall does not automatically add new features to custom role definitions.
Which Palo Alto Networks component provides consolidated policy creation and centralized management?
- A . GlobalProtect
- B . Panorama
- C . Aperture
- D . AutoFocus
B
Explanation:
https://www.paloaltonetworks.com/resources/datasheets/panorama-centralized-management-datasheet
Which two statements are true for the DNS Security service introduced in PAN-OS version 10.0?
(Choose two.)
- A . It is automatically enabled and configured.
- B . It eliminates the need for dynamic DNS updates.
- C . It functions like PAN-DB and requires activation through the app portal.
- D . It removes the 100K limit for DNS entries for the downloaded DNS updates.
BD
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/threat-prevention/dns-security/cloud-delivered-dns-signatures
1) Locally available, downloadable DNS signature sets (packaged with the antivirus and WildFire updates) come with a hard-coded capacity limitation of 100k signatures and do not include signatures generated through advanced analysis.
2) To better accommodate the influx of new DNS signatures being produced on a daily basis, the cloud-based signature database provides users with instant access to newly added DNS signatures without the need to download updates.
Which two settings allow you to restrict access to the management interface? (Choose two )
- A . enabling the Content-ID filter
- B . administrative management services
- C . restricting HTTP and telnet using App-ID
- D . permitted IP addresses
An internal host wants to connect to servers of the internet through using source NAT.
Which policy is required to enable source NAT on the firewall?
- A . NAT policy with source zone and destination zone specified
- B . post-NAT policy with external source and any destination address
- C . NAT policy with no source of destination zone selected
- D . pre-NAT policy with external source and any destination address
Which Security policy set should be used to ensure that a policy is applied first?
- A . Local firewall policy
- B . Shared pre-rulebase
- C . Parent device-group pre-rulebase
- D . Child device-group pre-rulebase
Where does a user assign a tag group to a policy rule in the policy creation window?
- A . General tab
- B . Usage tab
- C . Application tab
- D . Actions tab
A
Explanation:
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/use-tags-to-group-and-visually-distinguish-objects/view-rules-by-tag-group
Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall?
- A . Management
- B . High Availability
- C . Aggregate
- D . Aggregation
C
Explanation:
Only AGGREGATE interface can belong to a zone.
Which statement is true regarding a Best Practice Assessment?
- A . It runs only on firewalls.
- B . It shows how current configuration compares to Palo Alto Networks recommendations.
- C . When guided by an authorized sales engineer, it helps determine the areas of greatest risk where you should focus prevention activities.
- D . It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
B
Explanation:
Best Practice Assessment (BPA) Tool -The BPA for next-generation firewalls and Panorama evaluates a device’s configuration by measuring the adoption of capabilities, validating whether the policies adhere to best practices, and providing recommendations and instructions for how to remediate failed best practice checks.
The Security Policy Adoption Heatmap component filters the information by device groups, serial numbers, zones, areas of architecture, and other categories. The results include trending data, which shows the rate of security improvement as you adopt new capabilities, fix gaps, and progress toward a Zero-Trust network.
The BPA component performs more than 200 security checks on a firewall or Panorama configuration and provides a pass/fail score for each check. Each check is a best practice identified by Palo Alto Networks security experts. If a check returns a failing score, the tool provides the justification for the
failing score and how to fix the issue.
https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks-assessment-and-review-tools
What are the two types of Administrator accounts? (Choose two.)
- A . Role Based
- B . Superuser
- C . Dynamic
- D . Local
AC
Explanation:
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/firewall-administration/manage-firewall-administrators/configure-administrative-accounts-and-authentication/configure-a-firewall-administrator-account
An administrator would like to override the default deny action for a given application, and instead would like to block the traffic and send the ICMP code "communication with the destination is administratively prohibited".
Which security policy action causes this?
- A . Drop
- B . Drop, send ICMP Unreachable
- C . Reset both
- D . Reset server
B
Explanation:
Silently drops the traffic; for an application, it overrides the default deny action. A TCP reset is not sent to the host/application.
For Layer 3 interfaces, to optionally send an ICMP unreachable response to the client, set Action:
Drop and enable the Send ICMP Unreachable
check box. When enabled, the firewall sends the ICMP code for communication with the destination is administratively prohibited–ICMPv4: Type 3, Code 13; ICMPv6: Type 1, Code 1. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClltCAC#:~:text=The%20Deny%20action%20will%20tear,packets%20will%20be%20silently%20discarded.
An administrator wants to prevent hacking attacks through DNS queries to malicious domains.
Which two DNS policy actions can the administrator choose in the Anti-Spyware Security Profile? (Choose two.)
- A . deny
- B . block
- C . sinkhole
- D . override
Which three types of authentication services can be used to authenticate user traffic flowing through the firewall’s data plane? (Choose three.)
- A . SAML 2.0
- B . Kerberos
- C . TACACS
- D . TACACS+
- E . SAML 1.0
ABD
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/authentication/authentication-types.html
If a universal security rule was created for source zones A & B and destination zones A & B, to which traffic would the rule apply?
- A . Some traffic between A & B
- B . Some traffic within A
- C . All traffic within zones A & B
- D . Some traffic within B
A network administrator is required to use a dynamic routing protocol for network connectivity.
Which three dynamic routing protocols are supported by the NGFW Virtual Router for this purpose? (Choose three.)
- A . RIP
- B . OSPF
- C . IS-IS
- D . EIGRP
- E . BGP
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base.
On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days.
Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
- A . All traffic matching the SuperApp_chat, and SuperApp_download is denied because it no longer matches the SuperApp-base application
- B . No impact because the apps were automatically downloaded and installed
- C . No impact because the firewall automatically adds the rules to the App-ID interface
- D . All traffic matching the SuperApp_base, SuperApp_chat, and SuperApp_download is denied until the security administrator approves the applications
A
Explanation:
To allow the new applications, we need to modify or add a new policy.
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/app-id/manage-new-app-ids-introduced-in-content-releases/review-new-app-id-impact-on-existing-policy-rules
An administrator is trying to enforce policy on some (but not all) of the entries in an external dynamic list.
What is the maximum number of entries that they can be excluded?
- A . 50
- B . 100
- C . 200
- D . 1,000
B
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/exclude-entries-from-an-external-dynamic-list
The NetSec Manager asked to create a new EMEA Regional Panorama Administrator profile with customized privileges.
In particular, the new EMEA Regional Panorama Administrator should be able to:
– Access only EMEA-Regional device groups with read-only privileges
– Access only EMEA-Regional templates with read-only privileges
What is the correct configuration for the new EMEA Regional Panorama Administrator profile?
- A . Administrator Type = Device Group and Template Admin Admin Role = EMEA_Regional_Admin_read_only
Access Domain = EMEA-Regional - B . Administrator Type = Dynamic -Admin Role = Superuser (read-only)
- C . Administrator Type = Dynamic -Admin Role = Panorama Administrator
- D . Administrator Type = Custom Panorama Admin Profile = EMEA Regional Admin_read_only
How are Application Filters or Application Groups used in firewall policy?
- A . An Application Group is a static way of grouping applications and cannot be configured as a nested member of Application Group.
- B . An Application Group is a dynamic way of grouping applications and can be configured as a nested member of an Application Group.
- C . An Application Filter is a dynamic way to group applications and can be configured as a nested member of an Application Group.
- D . An Application Filter is a static way of grouping applications and can be configured as a nested member of an Application Group.
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
- A . Disable automatic updates during weekdays
- B . Automatically "download and install" but with the "disable new applications" option used
- C . Automatically "download only" and then install Applications and Threats later, after the administrator approves the update
- D . Configure the option for "Threshold"
D
Explanation:
Schedule content updates so that they download-and-install automatically. Then, set a Threshold that determines the amount of time the firewall waits before installing the latest content. In a mission-critical network, schedule up to a 48 hour threshold. https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/software-and-content-updates/best-practices-for-app-and-threat-content-updates/best-practices-mission-critical#id184AH00L078
How would a Security policy need to be written to allow outbound traffic using Secure Shell (SSH) to destination ports tcp/22 and tcp/4422?
- A . The admin creates a custom service object named "tcp-4422" with port tcp/4422.
The admin then creates a Security policy allowing application "ssh" and service "tcp-4422". - B . The admin creates a custom service object named "tcp-4422" with port tcp/4422.
The admin then creates a Security policy allowing application "ssh", service "tcp-4422", and service "application-default". - C . The admin creates a custom service object named "tcp-4422" with port tcp/4422. The admin also creates a custom service object named "tcp-22" with port tcp/22.
The admin then creates a Security policy allowing application "ssh", service "tcp-4422", and service "tcp-22". - D . The admin creates a Security policy allowing application "ssh" and service "application-default".
C
Explanation:
If you select application default, you will not add other service.
In which threat profile object would you configure the DNS Security service?
- A . Antivirus
- B . Anti-Spyware
- C . WildFire
- D . URL Filtering
B
Explanation:
https://docs.paloaltonetworks.com/dns-security/administration/configure-dns-security/enable-dns-security#:~:text=To%20enable%20DNS%20Security%2C%20you,to%20a%20security%20policy%20rule.
In which threat profile object would you configure the DNS Security service?
- A . Antivirus
- B . Anti-Spyware
- C . WildFire
- D . URL Filtering
B
Explanation:
https://docs.paloaltonetworks.com/dns-security/administration/configure-dns-security/enable-dns-security#:~:text=To%20enable%20DNS%20Security%2C%20you,to%20a%20security%20policy%20rule.
An administrator receives a notification about new malware that is being used to attack hosts.
The malware exploits a software bug in a common application.
Which Security Profile will detect and block access to this threat after the administrator updates the firewall’s threat signature database?
- A . Vulnerability Profile applied to inbound Security policy rules
- B . Antivirus Profile applied to outbound Security policy rules
- C . Data Filtering Profile applied to outbound Security policy rules
- D . Data Filtering Profile applied to inbound Security policy rules
What are two differences between an application group and an application filter? (Choose two.)
- A . Application groups enable access to sanctioned applications explicitly, while application filters enable access to sanctioned applications implicitly.
- B . Application groups are static, while application filters are dynamic.
- C . Application groups dynamically group applications based on attributes, while application filters contain applications that are statically grouped.
- D . Application groups can be added to application filters, while application filters cannot be added to application groups.
Which firewall feature do you need to configure to query Palo Alto Networks service updates over a data-plane interface instead of the management interface?
- A . service route
- B . dynamic updates
- C . SNMP setup
- D . data redistribution
Which firewall feature do you need to configure to query Palo Alto Networks service updates over a data-plane interface instead of the management interface?
- A . service route
- B . dynamic updates
- C . SNMP setup
- D . data redistribution
What are three characteristics of the Palo Alto Networks DNS Security service? (Choose three.)
- A . It uses techniques such as DGA/DNS tunneling detection and machine learning
- B . It requires a valid Threat Prevention license.
- C . It enables users to access real-time protections using advanced predictive analytics.
- D . It requires a valid URL Filtering license.
- E . It requires an active subscription to a third-party DNS Security service.
ABC
Explanation:
DNS Security subscription enables users to access real-time protections using advanced predictive analytics. When techniques such as DGA/DNS tunneling detection and machine learning are used, threats hidden within DNS traffic can be proactively identified and shared through an infinitely scalable cloud service. Because the DNS signatures and protections are stored in a cloud-based architecture, you can access the full database of ever-expanding signatures that have been generated using a multitude of data sources. This list of signatures allows you to defend against an array of threats using DNS in real-time against newly generated malicious domains. To combat future threats, updates to the analysis, detection, and prevention capabilities of the DNS Security service will be available through content releases. To access the DNS Security service, you must have a Threat Prevention license and DNS Security license.
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
- A . Reset-server
- B . Deny
- C . Drop
- D . Block
C
Explanation:
Drop silently drops the packet, while deny gives an update.
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
- A . Reset-server
- B . Deny
- C . Drop
- D . Block
C
Explanation:
Drop silently drops the packet, while deny gives an update.
Based on the graphic, which statement accurately describes the output shown in the Server Monitoring panel?
- A . The User-ID agent is connected to a domain controller labeled lab-client.
- B . The host lab-client has been found by the User-ID agent.
- C . The host lab-client has been found by a domain controller.
- D . The User-ID agent is connected to the firewall labeled lab-client.
A
Explanation:
lab-client is not a host, it is the name we are giving to the agent that is connecting to the specified domain controller (Active Directory).
The Administrator profile "PCNSA Admin" is configured with an Authentication profile "Authentication Sequence PCNSA".
The Authentication Sequence PCNSA has a profile list with four Authentication profiles: Auth Profile LDAP
Auth Profile Radius Auth Profile Local Auth Profile TACACS
After a network outage, the LDAP server is no longer reachable. The RADIUS server is still reachable but has lost the "PCNSA Admin" username and password.
Which option describes the "PCNSA Admin" login capabilities after the outage?
- A . Auth OK because of the Auth Profile TACACS
- B . Auth KO because RADIUS server lost user and password for PCNSA Admin
- C . Auth OK because of the Auth Profile Local
- D . Auth KO because LDAP server is not reachable
An administrator needs to add capability to perform real-time signature lookups to block or sinkhole all known malware domains.
Which type of single unified engine will get this result?
- A . User-ID
- B . App-ID
- C . Security Processing Engine
- D . Content-ID
D
Explanation:
Content-IDTM combines a real-time threat prevention engine with a comprehensive URL database and elements of application identification to limit unauthorized data and file transfers and detect and block a wide range of exploits, malware, dangerous web surfing as well as targeted and unknown threats.
https://www.paloaltonetworks.com/content/dam/pan/en_US/assets/pdf/tech-briefs/techbrief- content-id.pdf
Which three types of entries can be excluded from an external dynamic list? (Choose three.)
- A . IP addresses
- B . Applications
- C . User-ID
- D . Domains
- E . URLs
ADE
Explanation:
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/view-external-dynamic-list-entries
An administrator would like to determine the default deny action for the application dns-over-
https.
Which action would yield the information?
- A . View the application details in beacon paloaltonetworks.com
- B . Check the action for the Security policy matching that traffic
- C . Check the action for the decoder in the antivirus profile
- D . View the application details in Objects > Applications
An administrator configured a Security policy rule with an Antivirus Security profile. The administrator did not change the action for the profile.
If a virus gets detected, how will the firewall handle the traffic?
- A . It allows the traffic but generates an entry in the Threat logs.
- B . It drops the traffic because the profile was not set to explicitly allow the traffic.
- C . It allows the traffic because the profile was not set the explicitly deny the traffic.
- D . It uses the default action assigned to the virus signature.
Which security policy rule would be needed to match traffic that passes between the Outside zone and Inside zone, but does not match traffic that passes within the zones?
- A . global
- B . intrazone
- C . interzone
- D . universal
C
Explanation:
intrazone allows traffic within a zone not between different zones.
An internal host wants to connect to servers of the internet through using source NAT.
Which policy is required to enable source NAT on the firewall?
- A . post-NAT policy with external source and any destination address
- B . NAT policy with no source of destination zone selected
- C . NAT policy with source zone and destination zone specified
- D . pre-NAT policy with external source and any destination address
An administrator would like to create a URL Filtering log entry when users browse to any gambling website.
What combination of Security policy and Security profile actions is correct?
- A . Security policy = drop, Gambling category in URL profile = allow
- B . Security policy = deny. Gambling category in URL profile = block
- C . Security policy = allow, Gambling category in URL profile = alert
- D . Security policy = allow. Gambling category in URL profile = allow
C
Explanation:
A log entry is generated in the URL filtering log.
https://docs.paloaltonetworks.com/advanced-url-filtering/administration/url-filtering-basics/url-filtering-profiles
An administrator would like to create a URL Filtering log entry when users browse to any gambling website.
What combination of Security policy and Security profile actions is correct?
- A . Security policy = drop, Gambling category in URL profile = allow
- B . Security policy = deny. Gambling category in URL profile = block
- C . Security policy = allow, Gambling category in URL profile = alert
- D . Security policy = allow. Gambling category in URL profile = allow
C
Explanation:
A log entry is generated in the URL filtering log.
https://docs.paloaltonetworks.com/advanced-url-filtering/administration/url-filtering-basics/url-filtering-profiles
An administrator is updating Security policy to align with best practices.
Which Policy Optimizer feature is shown in the screenshot below?
- A . Rules without App Controls
- B . New App Viewer
- C . Rule Usage -Unused
- D . Unused Apps
A
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/app-id/security-policy-rule-optimization/migrate-port-based-to-app-id-based-security-policy-rules
How do you reset the hit count on a Security policy rule?
- A . select a security policy rule, right click Hit Count > Reset
- B . with a dataplane reboot
- C . Device > Setup > Logging and Reporting Settings > Reset Hit Count
- D . in the CLI, type command reset hitcount <POLICY-NAME>
How do you reset the hit count on a Security policy rule?
- A . select a security policy rule, right click Hit Count > Reset
- B . with a dataplane reboot
- C . Device > Setup > Logging and Reporting Settings > Reset Hit Count
- D . in the CLI, type command reset hitcount <POLICY-NAME>
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
- A . Translation Type
- B . Interface
- C . Address Type
- D . IP Address
What are the requirements for using Palo Alto Networks EDL Hosting Sen/ice?
- A . any supported Palo Alto Networks firewall or Prisma Access firewall
- B . an additional subscription free of charge
- C . a firewall device running with a minimum version of PAN-OS 10.1
- D . an additional paid subscription
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
- A . Layer 2
- B . Tap
- C . Layer 3
- D . Virtual Wire
Which statement is true regarding NAT rules?
- A . Static NAT rules have precedence over other forms of NAT.
- B . Translation of the IP address and port occurs before security processing.
- C . NAT rules are processed in order from top to bottom.
- D . Firewall supports NAT on Layer 3 interfaces only.
C
Explanation:
Which statement is true regarding NAT rules?
- A . Static NAT rules have precedence over other forms of NAT.
- B . Translation of the IP address and port occurs before security processing.
- C . NAT rules are processed in order from top to bottom.
- D . Firewall supports NAT on Layer 3 interfaces only.
C
Explanation:
Which statement is true regarding NAT rules?
- A . Static NAT rules have precedence over other forms of NAT.
- B . Translation of the IP address and port occurs before security processing.
- C . NAT rules are processed in order from top to bottom.
- D . Firewall supports NAT on Layer 3 interfaces only.
C
Explanation:
What is the minimum timeframe that can be set on the firewall to check for new WildFire signatures?
- A . every 30 minutes
- B . every 5 minutes
- C . once every 24 hours
- D . every 1 minute
D
Explanation:
Because new WildFire signatures are now available every five minutes, it is a best practice to use this setting to ensure the firewall retrieves these signatures within a minute of availability.
Which Security profile can be used to detect and block compromised hosts from trying to communicate with external command-and-control (C2) servers?
- A . URL Filtering
- B . Antivirus
- C . Vulnerability
- D . Anti-Spyware
When creating a custom URL category object, which is a valid type?
- A . domain match
- B . host names
- C . wildcard
- D . category match
D
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/objects/objects-custom-objects-url-category.html
When creating a custom URL category object, which is a valid type?
- A . domain match
- B . host names
- C . wildcard
- D . category match
D
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/objects/objects-custom-objects-url-category.html
What are two valid selections within an Anti-Spyware profile? (Choose two.)
- A . Random early drop
- B . Drop
- C . Deny
- D . Default
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
- A . outbound
- B . north south
- C . inbound
- D . east west
Which feature would be useful for preventing traffic from hosting providers that place few restrictions on content, whose services are frequently used by attackers to distribute illegal or unethical material?
- A . Palo Alto Networks Bulletproof IP Addresses
- B . Palo Alto Networks C&C IP Addresses
- C . Palo Alto Networks Known Malicious IP Addresses
- D . Palo Alto Networks High-Risk IP Addresses
A
Explanation:
To block hosts that use bulletproof hosts to provide malicious, illegal, and/or unethical content, use the bulletproof IP address list in policy. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PM0pCAG
Which statement is true about Panorama managed devices?
- A . Panorama automatically removes local configuration locks after a commit from Panorama.
- B . Local configuration locks prohibit Security policy changes for a Panorama managed device.
- C . Security policy rules configured on local firewalls always take precedence.
- D . Local configuration locks can be manually unlocked from Panorama.
B
Explanation:
When a user has a configuration lock, it is not possible to perform a commit or push a policy from Panorama. If the administrator is not available to remove the lock, a device WebGUI or CLI command can be used by a superuser to force the removal of the configuration lock. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CltACAS
When an ethernet interface is configured with an IPv4 address, which type of zone is it a
member of?
- A . Layer 3
- B . Virtual Wire
- C . Tap
- D . Tunnel
A network administrator created an intrazone Security policy rule on the firewall. The source zones were set to IT. Finance, and HR.
Which two types of traffic will the rule apply to? (Choose two)
- A . traffic between zone IT and zone Finance
- B . traffic between zone Finance and zone HR
- C . traffic within zone IT
- D . traffic within zone HR
What is the maximum volume of concurrent administrative account sessions?
- A . 2
- B . Unlimited
- C . 10
- D . 1
What are two predefined AntiSpyware profiles? (Choose two.)
- A . Default
- B . Standard
- C . Secure
- D . Strict
Where within the firewall GUI can all existing tags be viewed?
- A . Policies > Tags
- B . Network > Tags
- C . Objects > Tags
- D . Monitor > Tags
Where within the firewall GUI can all existing tags be viewed?
- A . Policies > Tags
- B . Network > Tags
- C . Objects > Tags
- D . Monitor > Tags
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
- A . User identification
- B . Filtration protection
- C . Vulnerability protection
- D . Antivirus
- E . Application identification
- F . Anti-spyware
When is the content inspection performed in the packet flow process?
- A . after the application has been identified
- B . after the SSL Proxy re-encrypts the packet
- C . before the packet forwarding process
- D . before session lookup
A
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0
To enable DNS sinkholing, which two addresses should be reserved? (Choose two.)
- A . MAC
- B . IPv6
- C . Email
- D . IPv4
BD
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClGECA0
An administrator would like to apply a more restrictive Security profile to traffic for file sharing applications. The administrator does not want to update the Security policy or object when new applications are released.
Which object should the administrator use as a match condition in the Security policy?
- A . the Content Delivery Networks URL category
- B . the Online Storage and Backup URL category
- C . an application group containing all of the file-sharing App-IDs reported in the traffic logs
- D . an application filter for applications whose subcategory is file-sharing
An administrator is reviewing the Security policy rules shown in the screenshot below.
Which statement is correct about the information displayed?
- A . Eleven rules use the "Infrastructure* tag.
- B . The view Rulebase as Groups is checked.
- C . There are seven Security policy rules on this firewall.
- D . Highlight Unused Rules is checked.
Given the screenshot, what two types of route is the administrator configuring? (Choose two.)
- A . BGP
- B . static route
- C . default route
- D . OSPF
What is a function of application tags?
- A . creation of new zones
- B . application prioritization
- C . automated referenced applications in a policy
- D . IP address allocations in DHCP
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
- A . Configure an authentication policy
- B . Configure an authentication sequence
- C . Configure an authentication profile
- D . Isolate the management interface on a dedicated management VLAN
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/firewall-administration/manage-firewall-administrators/configure-administrative-accounts-and-authentication/configure-a-firewall-administrator-account
Which rule type is appropriate for matching traffic occurring within a specified zone?
- A . Universal
- B . Shadowed
- C . Intrazone
- D . Interzone
Drag and Drop Question
Place the following steps in the packet processing order of operations from first to last.
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0
You receive notification about a new malware that infects hosts. An infection results in the infected host attempting to contact a command-and-control server.
Which Security Profile when applied to outbound Security policy rules detects and prevents this threat from establishing a command-and-control connection?
- A . Antivirus Profile
- B . Data Filtering Profile
- C . Vulnerability Protection Profile
- D . Anti-Spyware Profile
D
Explanation:
Anti-Spyware Security Profiles block spyware on compromised hosts from trying to communicate with external command-and-control (C2) servers, thus enabling you to detect malicious traffic leaving
the network from infected clients.
The data plane provides which two data processing features of the firewall? (Choose two.)
- A . signature matching
- B . reporting
- C . network processing
- D . logging
Which type of DNS signatures are used by the firewall to identify malicious and command-and-control domains?
- A . DNS Malicious signatures
- B . DNS Security signatures
- C . DNS Malware signatures
- D . DNS Block signatures
B
Explanation:
https://docs.paloaltonetworks.com/dns-security/administration/configure-dns-security/enable-dns-security#tabs-id066476b2-c4dd-4fc0-b7e4-f4ba32e19f60
What is an advantage for using application tags?
- A . They are helpful during the creation of new zones
- B . They help with the design of IP address allocations in DHCP.
- C . They help content updates automate policy updates
- D . They help with the creation of interfaces
C
Explanation:
Tags. All Tags. Are specific to the creation of Policy. They have several purposes, apply to any object, can be defined and so forth. I am uncertain as to whether any action subsequent to their application is automated or not. The only thing I’m clear on is, they are Security Policy related, or to it’s creation, whether automated or not.
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
- A . override
- B . allow
- C . block
- D . continue
Which two statements are correct about App-ID content updates? (Choose two.)
- A . Updated application content may change how security policy rules are enforced
- B . After an application content update, new applications must be manually classified prior to use
- C . Existing security policy rules are not affected by application content updates
- D . After an application content update, new applications are automatically identified and classified
AD
Explanation:
As new App-IDs are introduced and delivered to the firewall via weekly updates, dynamic filters are automatically updated for those applications that meet the filter criteria. This helps minimize administrative effort associated with security policy management. https://www.paloaltonetworks.com/resources/techbriefs/app-id-tech-brief.html
A website is unexpectedly allowed due to miscategorization.
What are two ways to resolve this issue for a proper response? (Choose two.)
- A . Create a URL category and assign the affected URL.
Update the active URL Filtering profile site access setting for the custom URL category to block. - B . Review the categorization of the website on https://urlfiltering paloaltonetworks.com.
Submit for "request change", identifying the appropriate categorization, and wait for confirmation before testing again. - C . Identify the URL category being assigned to the website.
Edit the active URL Filtering profile and update that category’s site access settings to block. - D . Create a URL category and assign the affected URL.
Add a Security policy with a URL category qualifier of the custom URL category below the original policy.
Set the policy action to Deny.
An administrator wants to create a NAT policy to allow multiple source IP addresses to be translated to the same public IP address.
What is the most appropriate NAT policy to achieve this?
- A . Dynamic IP and Port
- B . Dynamic IP
- C . Static IP
- D . Destination
A
Explanation:
Dynamic IP and Port (Many-to-One, Hide NAT, Source NAT) https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CllzCAC